一、安装traefik
先安装traefik-crds、下面的
---
# Source: traefik/templates/rbac/serviceaccount.yaml
kind: ServiceAccount
apiVersion: v1
metadata:
name: traefik-release
namespace: traefik
labels:
app.kubernetes.io/name: traefik
app.kubernetes.io/instance: traefik-release-default
helm.sh/chart: traefik-35.4.0
app.kubernetes.io/managed-by: Helm
annotations:
automountServiceAccountToken: false
---
# Source: traefik/templates/rbac/clusterrole.yaml
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: traefik-release-default
labels:
app.kubernetes.io/name: traefik
app.kubernetes.io/instance: traefik-release-default
helm.sh/chart: traefik-35.4.0
app.kubernetes.io/managed-by: Helm
rules:
- apiGroups:
- ""
resources:
- configmaps
- nodes
- services
verbs:
- get
- list
- watch
- apiGroups:
- discovery.k8s.io
resources:
- endpointslices
verbs:
- list
- watch
- apiGroups:
- ""
resources:
- secrets
verbs:
- get
- list
- watch
- apiGroups:
- extensions
- networking.k8s.io
resources:
- ingressclasses
- ingresses
verbs:
- get
- list
- watch
- apiGroups:
- extensions
- networking.k8s.io
resources:
- ingresses/status
verbs:
- update
- apiGroups:
- traefik.io
resources:
- ingressroutes
- ingressroutetcps
- ingressrouteudps
- middlewares
- middlewaretcps
- serverstransports
- serverstransporttcps
- tlsoptions
- tlsstores
- traefikservices
verbs:
- get
- list
- watch
---
# Source: traefik/templates/rbac/clusterrolebinding.yaml
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: traefik-release-default
labels:
app.kubernetes.io/name: traefik
app.kubernetes.io/instance: traefik-release-default
helm.sh/chart: traefik-35.4.0
app.kubernetes.io/managed-by: Helm
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: traefik-release-default
subjects:
- kind: ServiceAccount
name: traefik-release
namespace: traefik
---
# 添加PVC定义
apiVersion: v1
kind: PersistentVolumeClaim
metadata:
name: traefik-data-pvc
namespace: traefik
spec:
accessModes:
- ReadWriteMany # CephFS支持多节点读写
storageClassName: ceph-cephfs
resources:
requests:
storage: 1Gi # 根据实际需求调整大小
---
# Source: traefik/templates/deployment.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: traefik-release
namespace: traefik
labels:
app.kubernetes.io/name: traefik
app.kubernetes.io/instance: traefik-release-default
helm.sh/chart: traefik-35.4.0
app.kubernetes.io/managed-by: Helm
annotations:
spec:
replicas: 1
selector:
matchLabels:
app.kubernetes.io/name: traefik
app.kubernetes.io/instance: traefik-release-default
strategy:
type: RollingUpdate
rollingUpdate:
maxUnavailable: 0
maxSurge: 1
minReadySeconds: 0
template:
metadata:
annotations:
prometheus.io/scrape: "true"
prometheus.io/path: "/metrics"
prometheus.io/port: "9100"
labels:
app.kubernetes.io/name: traefik
app.kubernetes.io/instance: traefik-release-default
helm.sh/chart: traefik-35.4.0
app.kubernetes.io/managed-by: Helm
spec:
securityContext:
runAsUser: 0
runAsGroup: 0
fsGroup: 0
capabilities:
add: ["NET_BIND_SERVICE"]
serviceAccountName: traefik-release
automountServiceAccountToken: true
terminationGracePeriodSeconds: 60
hostNetwork: false
containers:
- image: registry.cn-guangzhou.aliyuncs.com/xingcangku/traefik:v3.0.0
imagePullPolicy: IfNotPresent
name: traefik-release
resources:
readinessProbe:
httpGet:
path: /ping
port: 9000
scheme: HTTP
failureThreshold: 1
initialDelaySeconds: 2
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 2
livenessProbe:
httpGet:
path: /ping
port: 9000
scheme: HTTP
failureThreshold: 3
initialDelaySeconds: 2
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 2
lifecycle:
ports:
- name: metrics
containerPort: 9100
protocol: TCP
- name: traefik
containerPort: 9000
protocol: TCP
- name: web
containerPort: 8000
protocol: TCP
- name: websecure
containerPort: 8443
protocol: TCP
securityContext:
allowPrivilegeEscalation: false
capabilities:
drop:
- ALL
- NET_BIND_SERVICE
readOnlyRootFilesystem: false
volumeMounts:
- name: data
mountPath: /data
readOnly: false # 允许写入
args:
- "--global.checknewversion"
- "--global.sendanonymoususage"
- "--entryPoints.metrics.address=:9100/tcp"
- "--entryPoints.traefik.address=:9000/tcp"
- "--entryPoints.web.address=:8000/tcp"
- "--entryPoints.websecure.address=:8443/tcp"
- "--api.dashboard=true"
- "--ping=true"
- "--metrics.prometheus=true"
- "--metrics.prometheus.entrypoint=metrics"
- "--providers.kubernetescrd"
- "--providers.kubernetescrd.allowEmptyServices=true"
- "--providers.kubernetesingress"
- "--providers.kubernetesingress.allowEmptyServices=true"
- "--providers.kubernetesingress.ingressendpoint.publishedservice=traefik/traefik-release"
- "--entryPoints.websecure.http.tls=true"
- "--log.level=INFO"
env:
- name: POD_NAME
valueFrom:
fieldRef:
fieldPath: metadata.name
- name: POD_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
volumes:
# 替换emptyDir为PVC
- name: data
persistentVolumeClaim:
claimName: traefik-data-pvc
securityContext:
runAsGroup: 65532
runAsNonRoot: true
runAsUser: 65532
---
# Source: traefik/templates/service.yaml
apiVersion: v1
kind: Service
metadata:
name: traefik
namespace: traefik
labels:
app.kubernetes.io/name: traefik
app.kubernetes.io/instance: traefik-release-default
helm.sh/chart: traefik-35.4.0
app.kubernetes.io/managed-by: Helm
annotations:
spec:
type: LoadBalancer
selector:
app.kubernetes.io/name: traefik
app.kubernetes.io/instance: traefik-release-default
ports:
- port: 8000
name: web
targetPort: web
protocol: TCP
- port: 8443
name: websecure
targetPort: websecure
protocol: TCP
---
# Source: traefik/templates/ingressclass.yaml
apiVersion: networking.k8s.io/v1
kind: IngressClass
metadata:
annotations:
ingressclass.kubernetes.io/is-default-class: "true"
labels:
app.kubernetes.io/name: traefik
app.kubernetes.io/instance: traefik-release-default
helm.sh/chart: traefik-35.4.0
app.kubernetes.io/managed-by: Helm
name: traefik-release
spec:
controller: traefik.io/ingress-controller
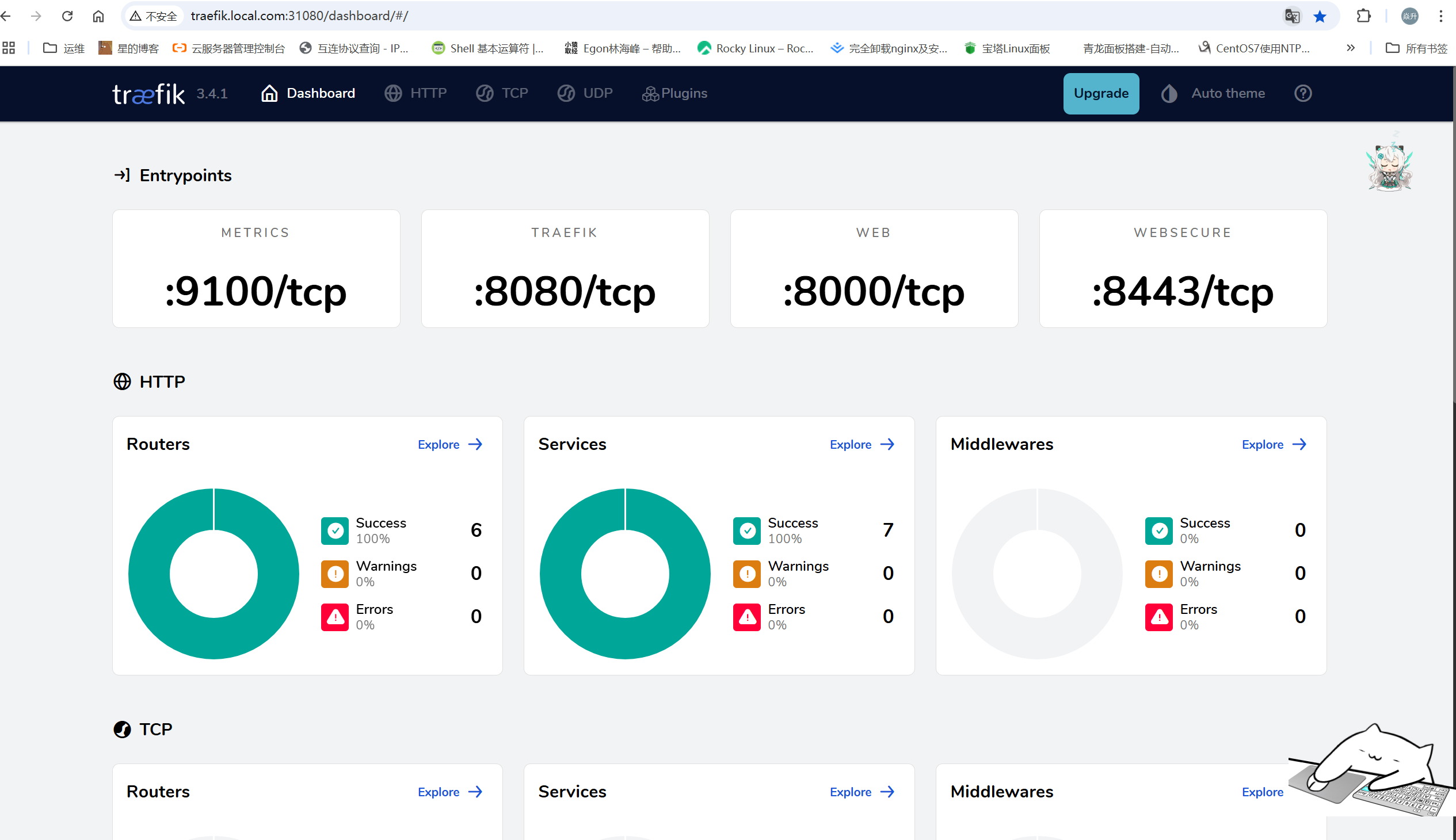
root@k8s01:~/helm/traefik/traefik-helm-chart-35.4.0/traefik# cat dashboard.yaml
apiVersion: traefik.io/v1alpha1
kind: IngressRoute
metadata:
name: dashboard
namespace: traefik
spec:
entryPoints:
- web
routes:
- match: Host(`traefik.local.com`)
kind: Rule
services:
- name: api@internal
kind: TraefikService
二、测试traefik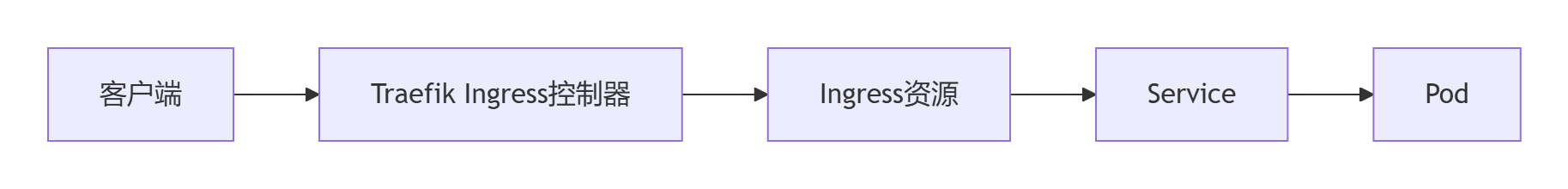
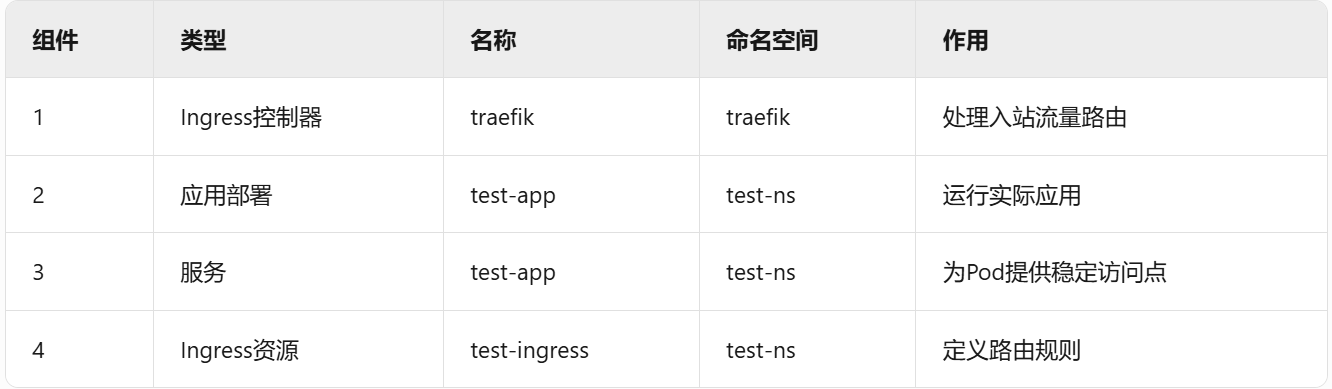
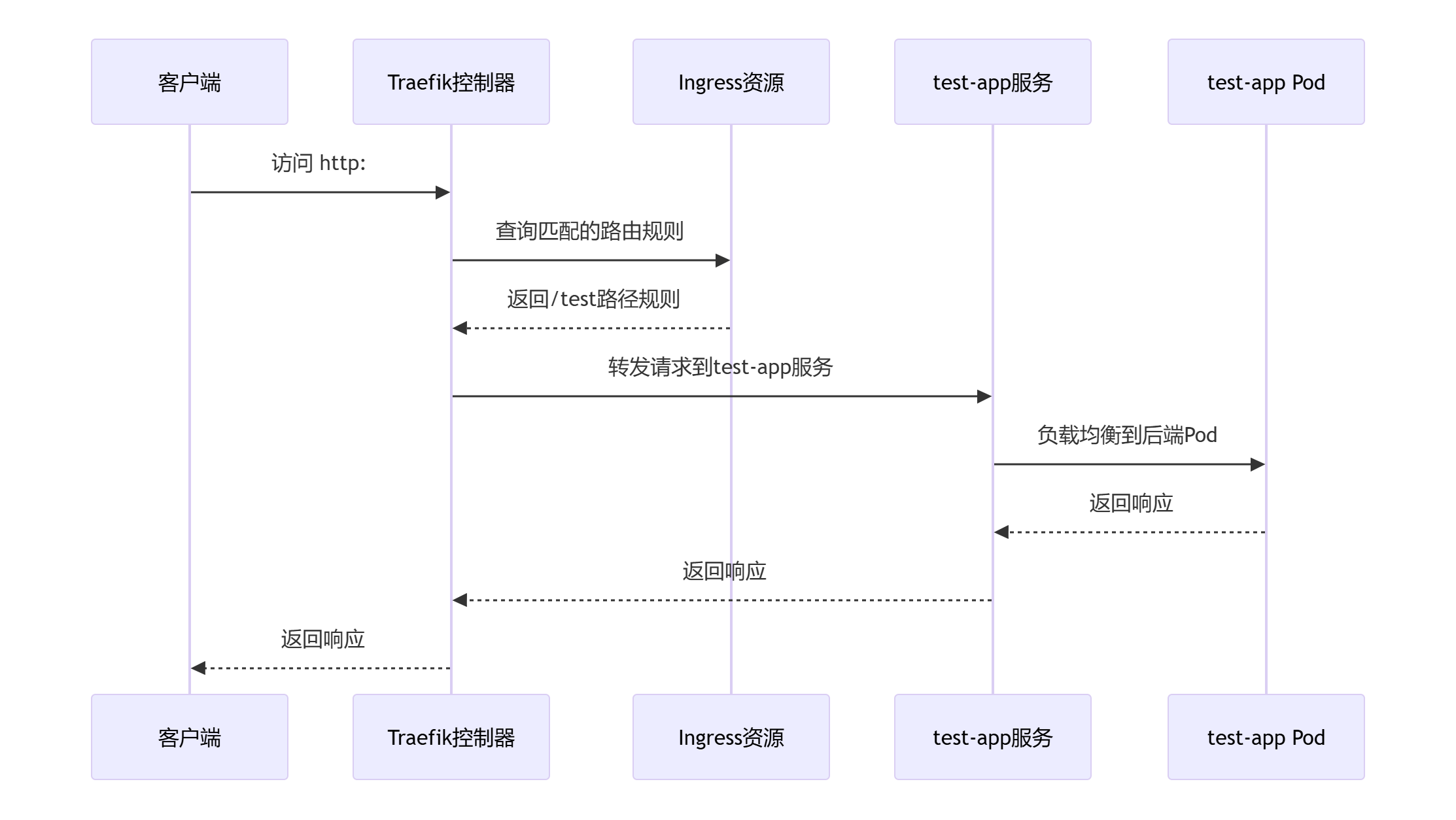
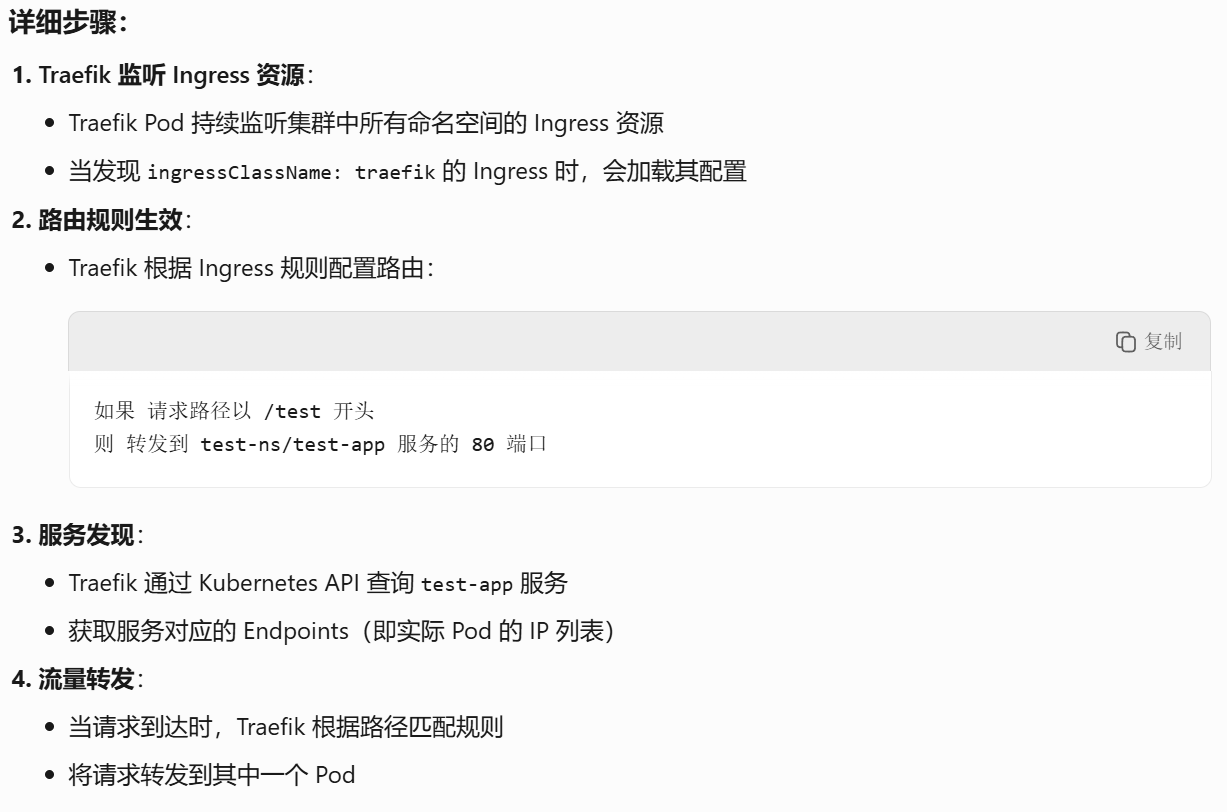
kubectl create ns test-ns
kubectl -n test-ns create deployment test-app --image=registry.cn-guangzhou.aliyuncs.com/xingcangku/nginx-alpine:1.0
kubectl -n test-ns expose deployment test-app --port=80cat <<EOF | kubectl apply -f -
> apiVersion: networking.k8s.io/v1
> kind: Ingress
> metadata:
> name: test-ingress
> namespace: test-ns
> spec:
> ingressClassName: traefik
> rules:
> - http:
> paths:
> - path: /test
> pathType: Prefix
> backend:
> service:
> name: test-app
> port:
> number: 80
> EOFWEB_PORT=$(kubectl get svc -n traefik traefik -o jsonpath='{.spec.ports[?(@.name=="web")].nodePort}')curl -v http://$NODE_IP:$WEB_PORT/test
* Trying 192.168.3.200:32305...
* Connected to 192.168.3.200 (192.168.3.200) port 32305 (#0)
> GET /test HTTP/1.1
> Host: 192.168.3.200:32305
> User-Agent: curl/7.81.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 404 Not Found
< Content-Length: 153
< Content-Type: text/html
< Date: Thu, 29 May 2025 18:06:51 GMT
< Server: nginx/1.27.5
<
<html>
<head><title>404 Not Found</title></head>
<body>
<center><h1>404 Not Found</h1></center>
<hr><center>nginx/1.27.5</center>
</body>
</html>
* Connection #0 to host 192.168.3.200 left intact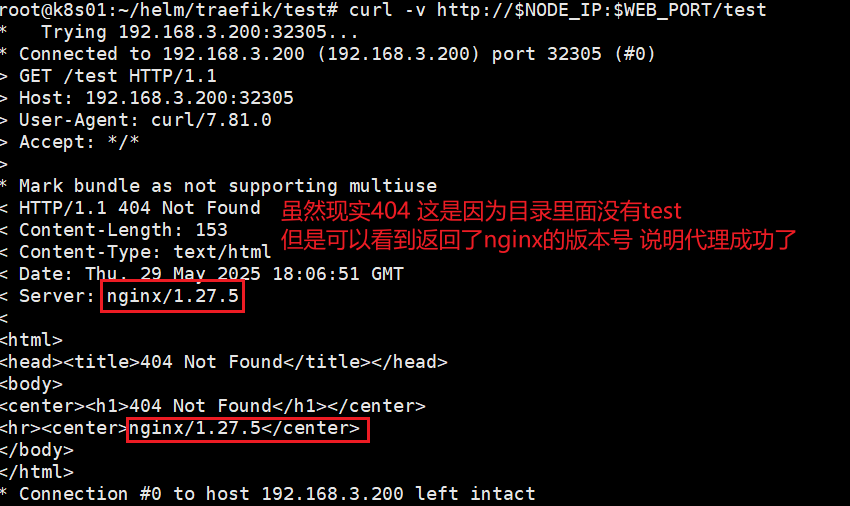
#更新路径
cat <<EOF | kubectl apply -f -
> apiVersion: networking.k8s.io/v1
> kind: Ingress
> metadata:
> name: test-ingress
> namespace: test-ns
> spec:
> ingressClassName: traefik
> rules:
> - http:
> paths:
> - path: /
> pathType: Prefix
> backend:
> service:
> name: test-app
> port:
> number: 80
> EOF
# 测试访问根路径
curl -v http://$NODE_IP:$WEB_PORT/
* Trying 192.168.3.200:32305...
* Connected to 192.168.3.200 (192.168.3.200) port 32305 (#0)
> GET / HTTP/1.1
> Host: 192.168.3.200:32305
> User-Agent: curl/7.81.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 200 OK
< Accept-Ranges: bytes
< Content-Length: 615
< Content-Type: text/html
< Date: Thu, 29 May 2025 18:08:48 GMT
< Etag: "67ffa8c6-267"
< Last-Modified: Wed, 16 Apr 2025 12:55:34 GMT
< Server: nginx/1.27.5
<
<!DOCTYPE html>
<html>
<head>
<title>Welcome to nginx!</title>
<style>
html { color-scheme: light dark; }
body { width: 35em; margin: 0 auto;
font-family: Tahoma, Verdana, Arial, sans-serif; }
</style>
</head>
<body>
<h1>Welcome to nginx!</h1>
<p>If you see this page, the nginx web server is successfully installed and
working. Further configuration is required.</p>
<p>For online documentation and support please refer to
<a href="http://nginx.org/">nginx.org</a>.<br/>
Commercial support is available at
<a href="http://nginx.com/">nginx.com</a>.</p>
<p><em>Thank you for using nginx.</em></p>
</body>
</html>
* Connection #0 to host 192.168.3.200 left intact#可以在集群内部访问
curl http://traefik-service.default.svc.cluster.localroot@k8s01:~/helm/traefik/test# kubectl get ingress -n test-ns
NAME CLASS HOSTS ADDRESS PORTS AGE
test-ingress traefik * 80 48m
root@k8s01:~/helm/traefik/test# kubectl describe ingress test-ingress -n test-ns
Name: test-ingress
Labels: <none>
Namespace: test-ns
Address:
Ingress Class: traefik
Default backend: <default>
Rules:
Host Path Backends
---- ---- --------
*
/ test-app:80 (10.244.1.13:80)
Annotations: <none>
Events: <none>
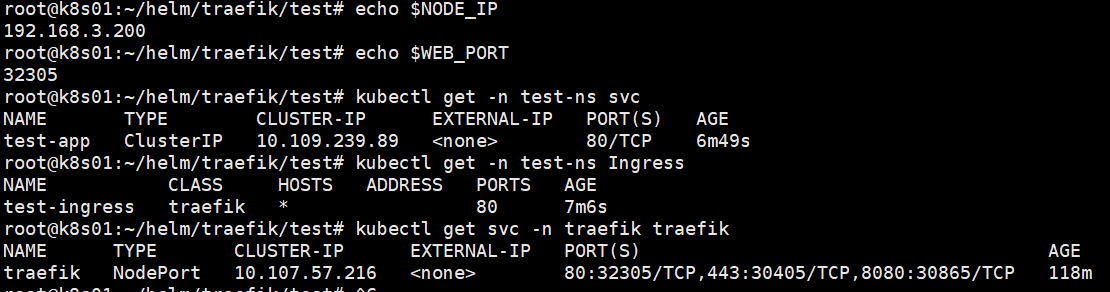
#命令查询
root@k8s01:~/helm/traefik/traefik-helm-chart-35.4.0/traefik# kubectl -n traefik describe svc traefik
Name: traefik
Namespace: traefik
Labels: app.kubernetes.io/instance=traefik-release-default
app.kubernetes.io/managed-by=Helm
app.kubernetes.io/name=traefik
helm.sh/chart=traefik-35.4.0
Annotations: <none>
Selector: app.kubernetes.io/instance=traefik-release-default,app.kubernetes.io/name=traefik
Type: LoadBalancer
IP Family Policy: SingleStack
IP Families: IPv4
IP: 10.103.186.47
IPs: 10.103.186.47
Port: web 8000/TCP
TargetPort: web/TCP
NodePort: web 30615/TCP
Endpoints: 10.244.2.30:8000
Port: websecure 8443/TCP
TargetPort: websecure/TCP
NodePort: websecure 32113/TCP
Endpoints: 10.244.2.30:8443
Session Affinity: None
External Traffic Policy: Cluster
Events: <none>
root@k8s01:~/helm/traefik/traefik-helm-chart-35.4.0/traefik# kubectl -n traefik get endpoints
NAME ENDPOINTS AGE
traefik 10.244.2.30:8000,10.244.2.30:8443 26s
traefik-crds 10.244.0.169:8000,10.244.0.169:8443 2d4h
root@k8s01:~/helm/traefik/traefik-helm-chart-35.4.0/traefik# cat service.yaml
# Source: traefik/templates/service.yaml
apiVersion: v1
kind: Service
metadata:
name: traefik
namespace: traefik
labels:
app.kubernetes.io/name: traefik
app.kubernetes.io/instance: traefik-release-default
helm.sh/chart: traefik-35.4.0
app.kubernetes.io/managed-by: Helm
annotations:
spec:
type: LoadBalancer
selector:
app.kubernetes.io/name: traefik
app.kubernetes.io/instance: traefik-release-default
ports:
- port: 8000
name: web
targetPort: web
protocol: TCP
- port: 8443
name: websecure
targetPort: websecure
protocol: TCP
root@k8s01:~/helm/traefik/traefik-helm-chart-35.4.0/traefik# kubectl get -n traefik svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
traefik LoadBalancer 10.103.186.47 <pending> 8000:30615/TCP,8443:32113/TCP 7m11s
traefik-crds LoadBalancer 10.101.202.240 <pending> 80:31080/TCP,443:32480/TCP,6379:30634/TCP 2d5h
root@k8s01:~/helm/traefik/traefik-helm-chart-35.4.0/traefik# kubectl get pods -n traefik -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
traefik-crds-766d79b985-c2sbr 1/1 Running 3 (6h13m ago) 2d4h 10.244.0.169 k8s01 <none> <none>
traefik-release-589c7ff647-pdjh4 1/1 Running 0 25m 10.244.2.30 k8s03 <none> <none>
root@k8s01:~/helm/traefik/traefik-helm-chart-35.4.0/traefik#


评论 (0)