一、安装kubernetes插件
在Jenkins的插件管理中安装Kubernetes插件
jenkins——>系统管理——>插件管理——>avaliable plugins
二、本集群连接
2.1创建sa账号
如果jenkins在k8s集群中部署,直接创建sa账号,并进行rbac授权即可,yaml文件参考前面文章。2.2创建cloud资源
然后在jenkins——>系统管理——>Clouds——>New cloud——>输入cloud name并勾选类型为kubernetes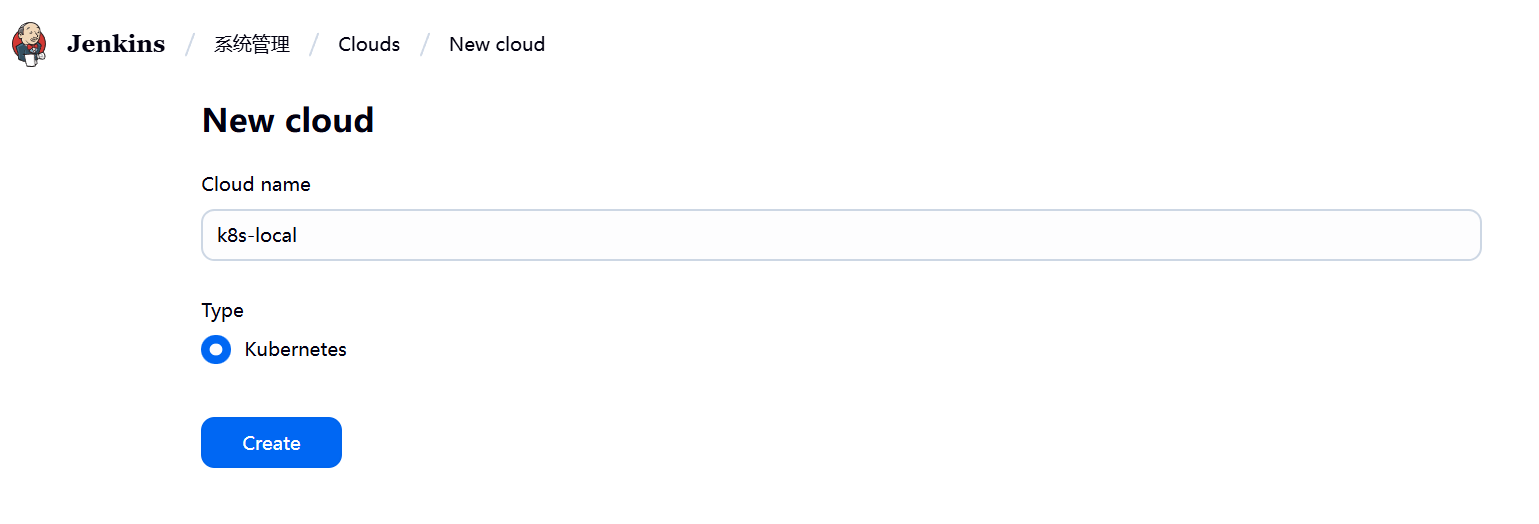
root@k8s-01:~/jenkins# cat deployment.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: jenkins
namespace: cicd
spec:
replicas: 1
selector:
matchLabels:
app: jenkins
template:
metadata:
labels:
app: jenkins
spec:
securityContext:
fsGroup: 1000 # 确保 Jenkins 用户有存储写入权限
serviceAccountName: jenkins-admin
automountServiceAccountToken: true
# 新增节点选择器,将 Pod 固定在 k8s-03 节点
nodeSelector:
kubernetes.io/hostname: k8s-03
containers:
- name: jenkins
image: registry.cn-guangzhou.aliyuncs.com/xingcangku/jenkins-jenkins-lts-jdk17:lts-jdk17
imagePullPolicy: IfNotPresent
ports:
- containerPort: 8080
- containerPort: 50000
# 新增环境变量(可选)
env:
- name: JAVA_HOME
value: "/usr/lib/jvm/amazon-corretto-17.0.16.8.1-linux-x64"
volumeMounts:
- name: jenkins-data
mountPath: /var/jenkins_home
# ============ 新增挂载 ============
- name: host-jvm
mountPath: /usr/lib/jvm
- name: maven-data
mountPath: /usr/local/maven
resources:
limits:
cpu: "1"
memory: "3Gi"
requests:
cpu: "0.5"
memory: "1Gi"
livenessProbe:
httpGet:
path: /login
port: 8080
initialDelaySeconds: 90
periodSeconds: 10
volumes:
- name: jenkins-data
persistentVolumeClaim:
claimName: jenkins-pvc
# ============ 新增的卷配置 ============
- name: host-jvm
hostPath:
path: /usr/lib/jvm
type: Directory
- name: maven-data
hostPath:
path: /usr/local/maven
type: Directoryroot@k8s-01:~/jenkins# cat new-rbac.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: jenkins-admin
namespace: cicd
---
# 创建自定义 ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: jenkins-clusterrole
rules:
- apiGroups: [""]
resources: ["pods", "pods/log", "services"]
verbs: ["get", "list", "watch", "create", "update", "delete"]
- apiGroups: ["apps"]
resources: ["deployments"]
verbs: ["*"]
---
# 绑定 ServiceAccount 到 ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: jenkins-crb
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: jenkins-clusterrole
subjects:
- kind: ServiceAccount
name: jenkins-admin
namespace: cicdk8s1.24版本以后,行为变更:从 Kubernetes v1.24 开始,不再自动为 ServiceAccount 创建 Secret(令牌不再存储在 Secret 中)
TokenRequest API:现在需要使用 TokenRequest API 获取令牌
root@k8s-01:~/jenkins# cat jenkins-secret.yaml
apiVersion: v1
kind: Secret
metadata:
name: jenkins-admin-token
namespace: cicd
annotations:
kubernetes.io/service-account.name: jenkins-admin
type: kubernetes.io/service-account-token
root@k8s-01:~/jenkins# kubectl apply -n cicd -f jenkins-secret.yaml
secret/jenkins-admin-token created
root@k8s-01:~/jenkins# kubectl describe sa jenkins-admin -n cicd
Name: jenkins-admin
Namespace: cicd
Labels: <none>
Annotations: <none>
Image pull secrets: <none>
Mountable secrets: <none>
Tokens: jenkins-admin-token
Events: <none>
root@k8s-01:~/jenkins# kubectl get secret jenkins-admin-token -n cicd -o jsonpath='{.data.token}' | base64 -d
eyJhbGciOiJSUzI1NiIsImtpZCI6IjJ0MTFFdDhfdnFBYkNuTnBSSXlyOFIzN1B0MW13cVVJNlFwZDV1VzR1WXcifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJjaWNkIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImplbmtpbnMtYWRtaW4tdG9rZW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiamVua2lucy1hZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjRkY2ViZjg1LTI0NzEtNGJjYi04Yzg5LWQ0MWI0NjAzN2RkZSIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpjaWNkOmplbmtpbnMtYWRtaW4ifQ.qvBiSwdCVbfMDnP0ElhnMcn__q65HDqidWw2JDQbrn7zrgNX2jjXlDxhA8RQFQaHhrTPGrOuP60vzfz4WgvJxwJvwIHaqqAbK8r3t-eTBpXNKltY3GEFEqxyjVlTd8q0DLW0OWZHUVZJrWhYT00Xa1ZViJgwQ2X0ogpAphSlvR351ZEDmDDxwxk4WwioZpmU22_weFamlU0g9SQVW5kBYGw06Tq_dPNL7cB0CDdPy0mSYckquEtG4xh-EIddPs9cGd1_OGurjwEkwX2-HvlfCXfoFkgo42lrOCaouWE4I4e21OXUCg5erFONSWSPKhhmhiLsjikByweCE0qaA2ZIUw#还要另外创建serviceAccount
root@k8s-01:~/jenkins# cat jenkins-secret.yaml rbac.yaml
apiVersion: v1
kind: Secret
metadata:
name: jenkins-admin-token
namespace: cicd
annotations:
kubernetes.io/service-account.name: jenkins-admin
type: kubernetes.io/service-account-token
# rbac.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: jenkins-admin
namespace: cicd
---
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: jenkins-admin-crb
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: edit # 授予命名空间内管理权限
subjects:
- kind: ServiceAccount
name: jenkins-admin
namespace: cicd#Kubernetes 服务证书 key
root@k8s-01:~/jenkins# kubectl get secret jenkins-admin-token -n cicd -o jsonpath='{.data.ca\.crt}' | base64 -d
-----BEGIN CERTIFICATE-----
MIIDBTCCAe2gAwIBAgIIUTF7Qh3Q+fowDQYJKoZIhvcNAQELBQAwFTETMBEGA1UE
AxMKa3ViZXJuZXRlczAeFw0yNTA3MzAxMjU3MDdaFw0zNTA3MjgxMzAyMDdaMBUx
EzARBgNVBAMTCmt1YmVybmV0ZXMwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEK
AoIBAQCv6lpzywPfjhKfl0HCNA/onj3MJyWI4z1JUwDlukI2j7ygm+kM2rWLpRYY
wjNrvzq7R4ZD2SfiFbN/Lo/EV0zM0MXdcsI8hkR6txlKXjRkrC5crCihd9idk2UR
Ov25k7bE3JpvG/zVswNMuliHx38gNsv1tfSv75lfCKyiyO3rrnj3LR9iYFvArgzY
a1F5FXNjw0HVRVIPeH060i75G3YhKDVAQoZVdMoJfW7wwZDDHnh1/GB16a9Jws+r
MjIQVD0YtxhQdg7WeV2nfCs0L8yXInKXwX6MGv+/HRPw140TihZwnC9gYFPisRJ5
EtUV+uq78w3Vj7Y2ANlTTQbN/F1bAgMBAAGjWTBXMA4GA1UdDwEB/wQEAwICpDAP
BgNVHRMBAf8EBTADAQH/MB0GA1UdDgQWBBSvRW0owjCv5rHXwOgsyrI2QC0CxDAV
BgNVHREEDjAMggprdWJlcm5ldGVzMA0GCSqGSIb3DQEBCwUAA4IBAQBL7BDL9wKu
TTZ4Lx8aGAIjuEP1slw8FnDuFY2V2M8cu2wX1tlqYKJkIbwwc/dr59j6LhLgTZaP
p02lQJXNRG6vR4zydgzXgsTMDXK1ANI6+7/jYgCwixGgBs/IafISCFkm1IkQ70Cw
rgibN4MvybWewmucS21F62HQzO1xvrHGL8YVxvFvaUyhL9+7VhYeIX2MF3E2jLl5
kzT74Awv0O+4zBcULKrYQqNEErf5fpRLi+y9SaKA2e85DWexkhkIb6y1lZScLjRp
q1lkgXqcriE653t78WrE1dSaCJY8QI94jYr4B2u7S1sbNJ9vPCDHQfFfl0DgRI/e
K8+av0Qro/aA
-----END CERTIFICATE-----点击kubernetes cloud details填写cloud详细信息
- Kubernetes地址:在集群内部暴露的k8s service名称https://kubernetes.default.svc
- Kubernetes命名空间:jenkins sa所属的名称空间cicd
- Jenkins地址:jenkins svc的名称:8080端口http://jenkins.cicd.svc:8080
使用刚刚获取的令牌在 Jenkins 中创建凭据:
凭据类型:Secret text
Secret:粘贴上面的令牌值
ID:k8s-service-account-token
配置完成后点击连接测试,显示k8s集群版本,证明配置无误。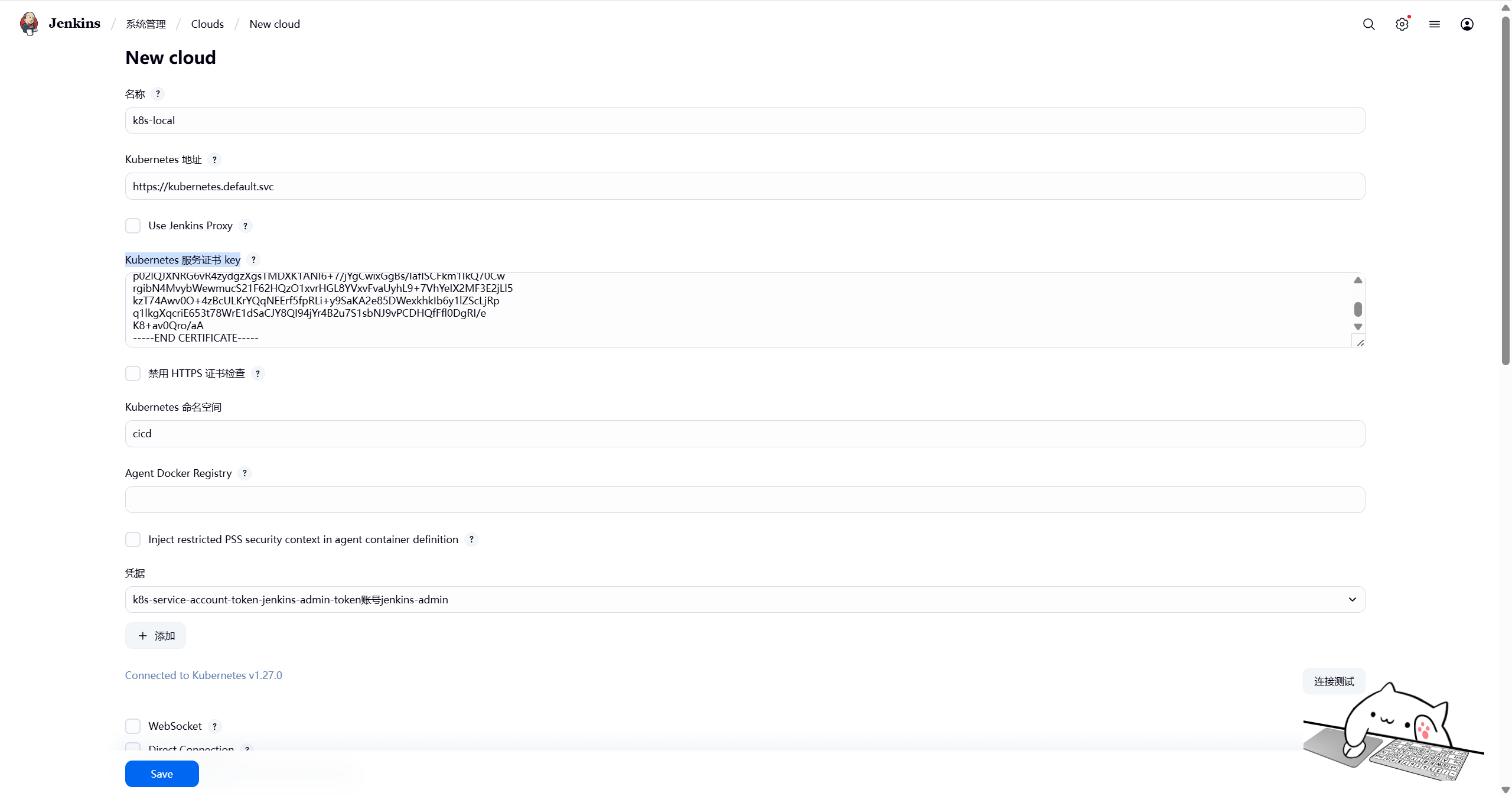
三、跨集群连接
在某些情况下,jenkins部署在k8s集群外,通过二进制或者docker方式部署,如果想要连接k8s集群实现资源自动创建。或者当前jenkins部署在k8s集群A中,需要通过jenkins实现集群B资源的自动创建发布,使用此方式连接。3.1配置思路
jenkins要想连接并操作k8s集群,需要配置授权,请求k8s集群的kube apiserver的请求,可以和kubectl一样利用config文件用作请求的鉴权,默认在~/.kube/config下,也可以单独严格指定权限细节,生成一个jenkins专用的config文件。
在jenkins中能够识别的证书文件为PKCS#12 certificate,因此需要先将kubeconfig文件中的证书转换生成PKCS#12格式的pfx证书文件3.2生成证书
我们可以使用yq命令行工具解析yaml,并提取相关的内容,然后通过base 64解码,最后生成文件
安装yq工具,仓库地址:https://github.com/mikefarah/yq
[root@k8s-master ~]# wget https://github.com/mikefarah/yq/releases/download/v4.34.1/yq_linux_amd64.tar.gz
[root@k8s-master ~]# tar -zxvf yq_linux_amd64.tar.gz
[root@k8s-master ~]# mv yq_linux_amd64 /usr/bin/yq
[root@k8s-master ~]# yq --version
yq (https://github.com/mikefarah/yq/) version v4.34.1
[root@k8s-master ~]# mkdir -p /opt/jenkins-crt/certificate-authority-data——>base 64解码——>ca.crt
client-certificate-data——>base 64解码——>client.crt
client-key-data——>base 64解码——>client.key[root@k8s-master ~]# yq e '.clusters[0].cluster.certificate-authority-data' /root/.kube/config | base64 -d > /opt/jenkins-crt/ca.crt
[root@k8s-master ~]# yq e '.users[0].user.client-certificate-data' /root/.kube/config | base64 -d > /opt/jenkins-crt/client.crt
[root@k8s-master ~]# yq e '.users[0].user.client-key-data' /root/.kube/config | base64 -d > /opt/jenkins-crt/client.key
[root@k8s-master ~]# cd /opt/jenkins-crt/
[root@k8s-master jenkins-crt]# ls -la
总用量 12
drwxr-xr-x 2 root root 56 6月 10 20:54 .
drwxr-xr-x. 6 root root 65 6月 10 20:37 ..
-rw-r--r-- 1 root root 1099 6月 10 20:53 ca.crt
-rw-r--r-- 1 root root 1147 6月 10 20:53 client.crt
-rw-r--r-- 1 root root 1675 6月 10 20:54 client.key3.3转换证书
通过openssl进行证书格式的转换,生成Client P12认证文件cert.pfx,输入两次密码并牢记密码。[root@k8s-master jenkins-crt]# openssl pkcs12 -export -out cert.pfx -inkey client.key -in client.crt -certfile ca.crt
Enter Export Password:
Verifying - Enter Export Password:
[root@k8s-master jenkins-crt]# ls -la
总用量 16
drwxr-xr-x 2 root root 72 6月 10 20:55 .
drwxr-xr-x. 6 root root 65 6月 10 20:37 ..
-rw-r--r-- 1 root root 1099 6月 10 20:53 ca.crt
-rw------- 1 root root 3221 6月 10 20:55 cert.pfx
-rw-r--r-- 1 root root 1147 6月 10 20:53 client.crt
-rw-r--r-- 1 root root 1675 6月 10 20:54 client.key3.4导入证书
打开jenkins的web界面,系统管理——>Credentials——>添加全局凭据
凭据的类型选择Certificate,证书上传刚才生成的cert.pfx证书文件,输入通过openssl生成证书文件时输入的密码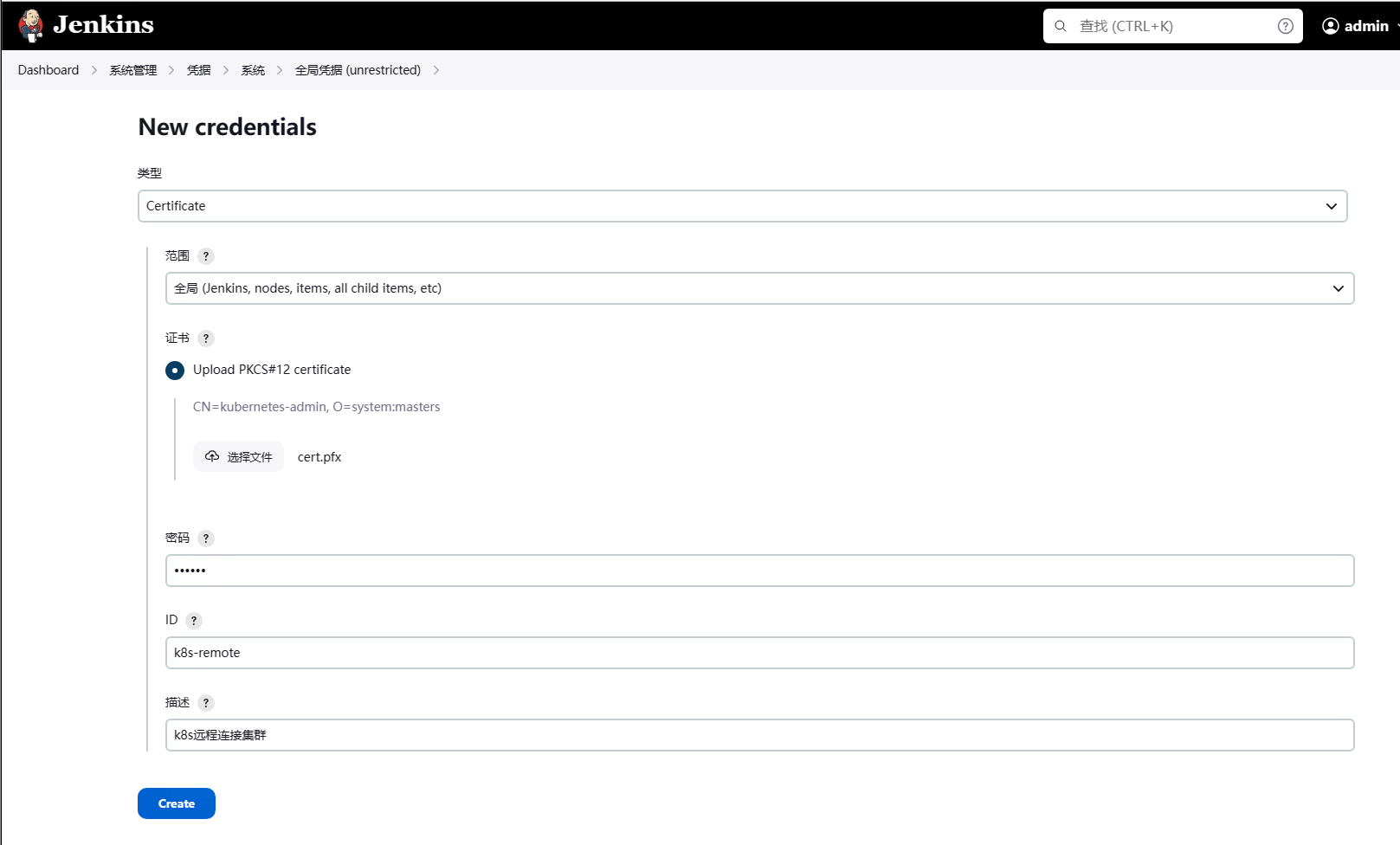
3.5配置远程k8s集群地址
jenkins——>系统管理——>Clouds——>New cloud——>输入cloud name并勾选类型为kubernetes
填写cloud详细信息
- Kubernetes地址:/root/.kube/config文件中cluster部分中server的内容
- Kubernetes命名空间:/root/.kube/config文件中cluster部分中name的内容
- Jenkins地址:jenkins服务的地址
- kubernetes服务证书key:ca.crt内容
- 凭据:选择刚刚创建的Certificate凭据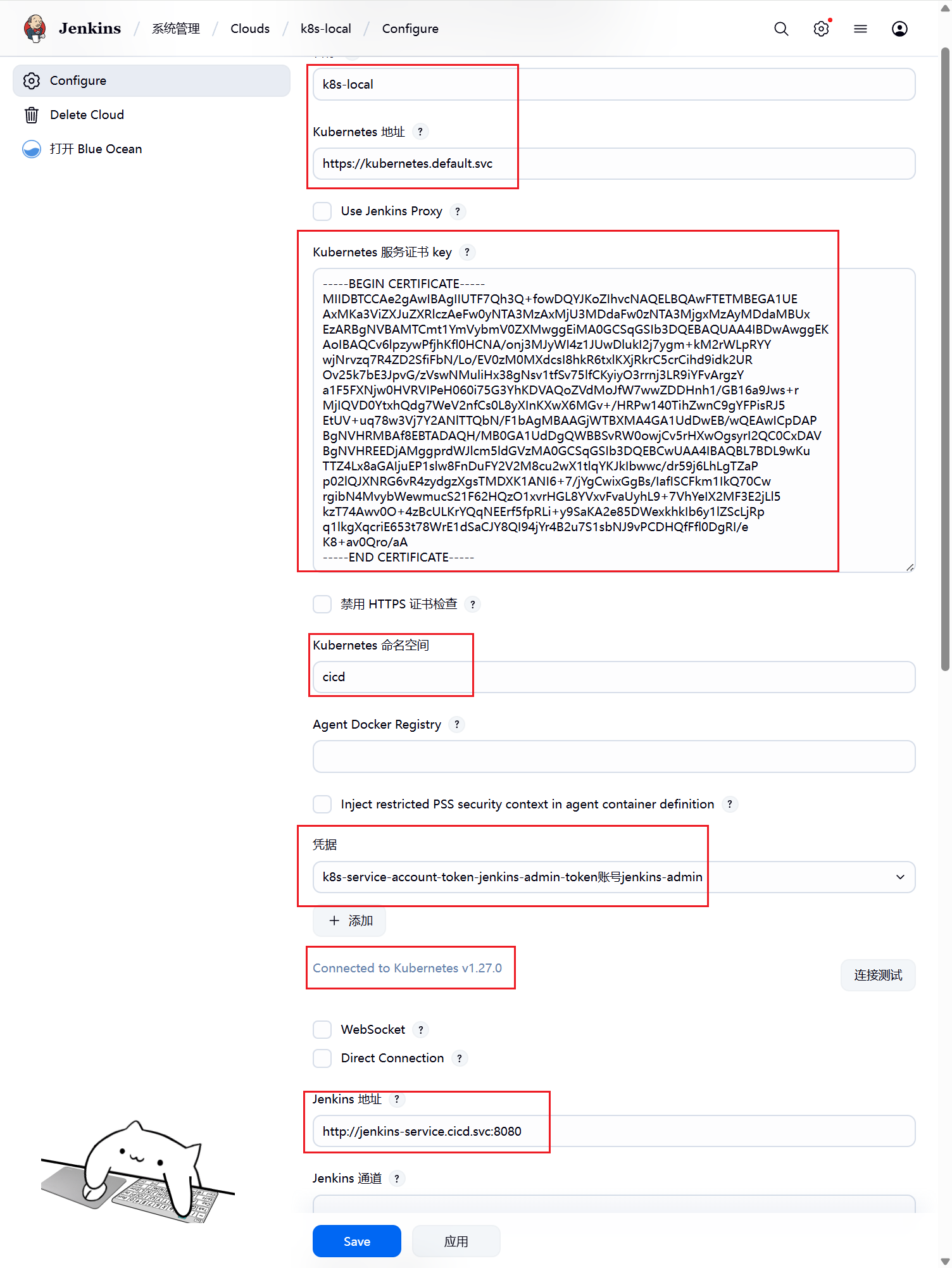
配置完成后点击连接测试,显示k8s集群版本,证明配置无误。四、动态slave介绍
4.1为什么需要动态slave
目前大多公司都采用 Jenkins 集群来搭建符合需求的 CI/CD 流程,然而传统的 Jenkins Slave 一主多从方式会存在一些痛点,比如:
- 主 Master 发生单点故障时,整个流程都不可用了
- 每个 Slave 的配置环境不一样,来完成不同语言的编译打包等操作,但是这些差异化的配置导致管理起来非常不方便,维护起来也是比较费劲
- 资源分配不均衡,有的 Slave 要运行的 job 出现排队等待,而有的 Slave 处于空闲状态
- 资源有浪费,每台 Slave 可能是物理机或者虚拟机,当 Slave 处于空闲状态时,也不会完全释放掉资源。
正因为上面的这些种种痛点,我们渴望一种更高效更可靠的方式来完成这个 CI/CD 流程,而 Docker虚拟化容器技术能很好的解决这个痛点,又特别是在 Kubernetes 集群环境下面能够更好来解决上面的问题,下图是基于 Kubernetes 搭建 Jenkins 集群的简单示意图: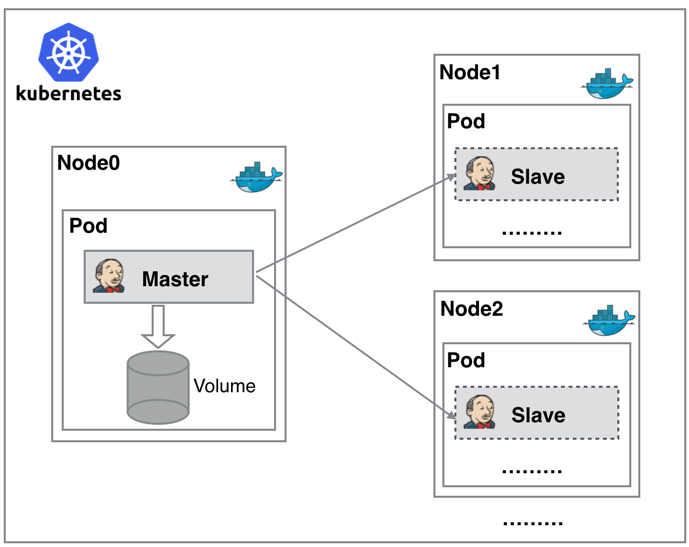
从图上可以看到 Jenkins Master 和 Jenkins Slave 以 Pod 形式运行在 Kubernetes 集群的 Node 上,Master 运行在其中一个节点,并且将其配置数据存储到一个 Volume 上去,Slave 运行在各个节点上,并且它不是一直处于运行状态,它会按照需求动态的创建并自动删除。
这种方式的工作流程大致为:当 Jenkins Master 接受到 Build 请求时,会根据配置的 Label 动态创建一个运行在 Pod 中的 Jenkins Slave 并注册到 Master 上,当运行完 Job 后,这个 Slave 会被注销并且这个 Pod 也会自动删除,恢复到最初状态。4.2Jenkins Slave好处
- 服务高可用,当 Jenkins Master 出现故障时,Kubernetes 会自动创建一个新的 Jenkins Master 容器,并且将 Volume 分配给新创建的容器,保证数据不丢失,从而达到集群服务高可用(这是k8s带来的资源控制器带来的优势)
- 动态伸缩,合理使用资源,每次运行 Job 时,会自动创建一个 Jenkins Slave,Job 完成后,Slave 自动注销并删除容器,资源自动释放,而且 Kubernetes 会根据每个资源的使用情况,动态分配 Slave 到空闲的节点上创建,降低出现因某节点资源利用率高,还排队等待在该节点的情况。
- 扩展性好,当 Kubernetes 集群的资源严重不足而导致 Job 排队等待时,可以很容易的添加一个 Kubernetes Node 到集群中,从而实现扩展。五、动态slave配置
5.1制作slave镜像
slave镜像应该包含以下功能:
- 运行jenkins-agent服务
- 使用kubectl命令操作k8s集群
- 使用nerdctl工具管理container镜像
- 使用buildctl构建container镜像。#获取文件
root@k8s-01:~/jenkins/work# cp /usr/bin/kubectl .
root@k8s-01:~/jenkins/work# cp /usr/bin/nerdctl .
root@k8s-01:~/jenkins/work# cp /usr/local/bin/buildctl .
root@k8s-01:~/jenkins/work# ls
buildctl Dockerfile kubectl nerdctl#构建镜像
#在构建镜像过程中基于inbound-agent镜像,因为其中已经包含了jenkins-agent服务相关组件,再添加kubectl工具用于操作k8s,nerdctl和buildctl工具用于构建和管理container镜像。
root@k8s-01:~/jenkins/work# cat Dockerfile
FROM jenkins/inbound-agent:latest-jdk17
USER root
COPY kubectl /usr/bin/kubectl
COPY nerdctl /usr/bin/nerdctl
COPY buildctl /usr/bin/buildctl
root@k8s-01:~/jenkins/work# docker build -t jenkins-agent:v1 .
[+] Building 714.4s (9/9) FINISHED docker:default
=> [internal] load build definition from Dockerfile 0.0s
=> => transferring dockerfile: 181B 0.0s
=> [internal] load metadata for docker.io/jenkins/inbound-agent:latest-jdk17 4.1s
=> [internal] load .dockerignore 0.0s
=> => transferring context: 2B 0.0s
=> [1/4] FROM docker.io/jenkins/inbound-agent:latest-jdk17@sha256:591ba0391e1dc47af64432198be00a9e457c74d215970c4f1af592a21 709.8s
=> => resolve docker.io/jenkins/inbound-agent:latest-jdk17@sha256:591ba0391e1dc47af64432198be00a9e457c74d215970c4f1af592a210a 0.0s
=> => sha256:a90156da31f7db1823e946282d3743d1f917b9622d122a1d45818ef43c6f5dc9 8.35kB / 8.35kB 0.0s
=> => sha256:59e22667830bf04fb35e15ed9c70023e9d121719bb87f0db7f3159ee7c7e0b8d 28.23MB / 28.23MB 327.6s
=> => sha256:9ac051fdbd99f7d8c9e496724860b8ae3373f24d6f8a54f1d9096526df425d3c 43.12MB / 43.12MB 581.2s
=> => sha256:85a4e35755fb1aa44b91602297dc8d9f10eb8ad3f32baab32094cebc0eda41a4 3.32kB / 3.32kB 0.8s
=> => sha256:591ba0391e1dc47af64432198be00a9e457c74d215970c4f1af592a210a6c37b 3.14kB / 3.14kB 0.0s
=> => sha256:7eddb97bde91ed86d7e82e7fa5f23370b33e87882aafdbcfb2782fdec95f6231 2.19kB / 2.19kB 0.0s
=> => sha256:cef14de45bb7cc343e593f80531764848fe724db9084ae4a3cabacc7a7e24083 1.24MB / 1.24MB 14.3s
=> => sha256:28f95146d6851ca39a2ce18612cb5e5b19845ef85e4bb95bfa3095193fdf5777 1.24MB / 1.24MB 28.5s
=> => sha256:68a03bb16ee6a2c356d2e354bab5ec566dd7ef1e4e6daee52c1f87aa9d0cd139 62.99MB / 62.99MB 709.1s
=> => extracting sha256:59e22667830bf04fb35e15ed9c70023e9d121719bb87f0db7f3159ee7c7e0b8d 2.1s
=> => sha256:1c55318e78a1d3f438c6ca3cf6532d365a86fabbf7e3ecd14140e455f1489991 161B / 161B 328.8s
=> => sha256:4f4fb700ef54461cfa02571ae0db9a0dc1e0cdb5577484a6d75e68dc38e8acc1 32B / 32B 329.5s
=> => sha256:392ad068a4827c711e9af3956bd5d3bcac7e8d66b3dd35bb0a9fae60de47f80d 2.37kB / 2.37kB 330.2s
=> => extracting sha256:85a4e35755fb1aa44b91602297dc8d9f10eb8ad3f32baab32094cebc0eda41a4 0.0s
=> => sha256:65375761a96d26587431452e982c657d479c41c41027a7f0acf37a6a21fd1112 180B / 180B 330.9s
=> => extracting sha256:9ac051fdbd99f7d8c9e496724860b8ae3373f24d6f8a54f1d9096526df425d3c 2.3s
=> => extracting sha256:cef14de45bb7cc343e593f80531764848fe724db9084ae4a3cabacc7a7e24083 0.0s
=> => extracting sha256:28f95146d6851ca39a2ce18612cb5e5b19845ef85e4bb95bfa3095193fdf5777 0.0s
=> => extracting sha256:68a03bb16ee6a2c356d2e354bab5ec566dd7ef1e4e6daee52c1f87aa9d0cd139 0.6s
=> => extracting sha256:1c55318e78a1d3f438c6ca3cf6532d365a86fabbf7e3ecd14140e455f1489991 0.0s
=> => extracting sha256:4f4fb700ef54461cfa02571ae0db9a0dc1e0cdb5577484a6d75e68dc38e8acc1 0.0s
=> => extracting sha256:392ad068a4827c711e9af3956bd5d3bcac7e8d66b3dd35bb0a9fae60de47f80d 0.0s
=> => extracting sha256:65375761a96d26587431452e982c657d479c41c41027a7f0acf37a6a21fd1112 0.0s
=> [internal] load build context 0.7s
=> => transferring context: 107.93MB 0.7s
=> [2/4] COPY kubectl /usr/bin/kubectl 0.2s
=> [3/4] COPY nerdctl /usr/bin/nerdctl 0.1s
=> [4/4] COPY buildctl /usr/bin/buildctl 0.1s
=> exporting to image 0.1s
=> => exporting layers 0.1s
=> => writing image sha256:ad852c7e884a5f9f6e87fcb6112fbe0c616b601a69ae5cf74ba09f2456d4e578 0.0s
=> => naming to docker.io/library/jenkins-agent:v1 0.0s
root@k8s-01:~/jenkins# docker login --username=aliyun3891595718 registry.cn-guangzhou.aliyuncs.com
Password:
WARNING! Your credentials are stored unencrypted in '/root/.docker/config.json'.
Configure a credential helper to remove this warning. See
https://docs.docker.com/go/credential-store/
Login Succeeded
root@k8s-01:~/jenkins# docker push registry.cn-guangzhou.aliyuncs.com/xingcangku/jenkins-cangku:v1
The push refers to repository [registry.cn-guangzhou.aliyuncs.com/xingcangku/jenkins-cangku]
2de7e3a095aa: Pushed
235bf2aaf23c: Pushed
9c18f60b53bc: Pushed
ec380c7051cf: Pushed
0c3e60359c38: Pushed
5f70bf18a086: Pushed
433332898d75: Pushed
b2c56f1e2ab9: Pushed
1411e4580b87: Pushed
df5f57ff732b: Pushed
3f360379e3d1: Pushed
f03c3dd333b7: Pushed
7cc7fe68eff6: Pushed
v1: digest: sha256:b3e519ae85d0f05ff170778c8ffae494879397d9881ca8bc905bc889da82fc07 size: 30475.2创建kube-config资源
为了能让slave容器中能够使用 kubectl 工具来访问我们的 Kubernetes 集群,需要将其添加为secret资源,并挂载到pod中。
root@k8s-01:~/jenkins/work# kubectl create secret generic -n cicd kube-config --from-file=/root/.kube/config
secret/kube-config created5.2.1测试
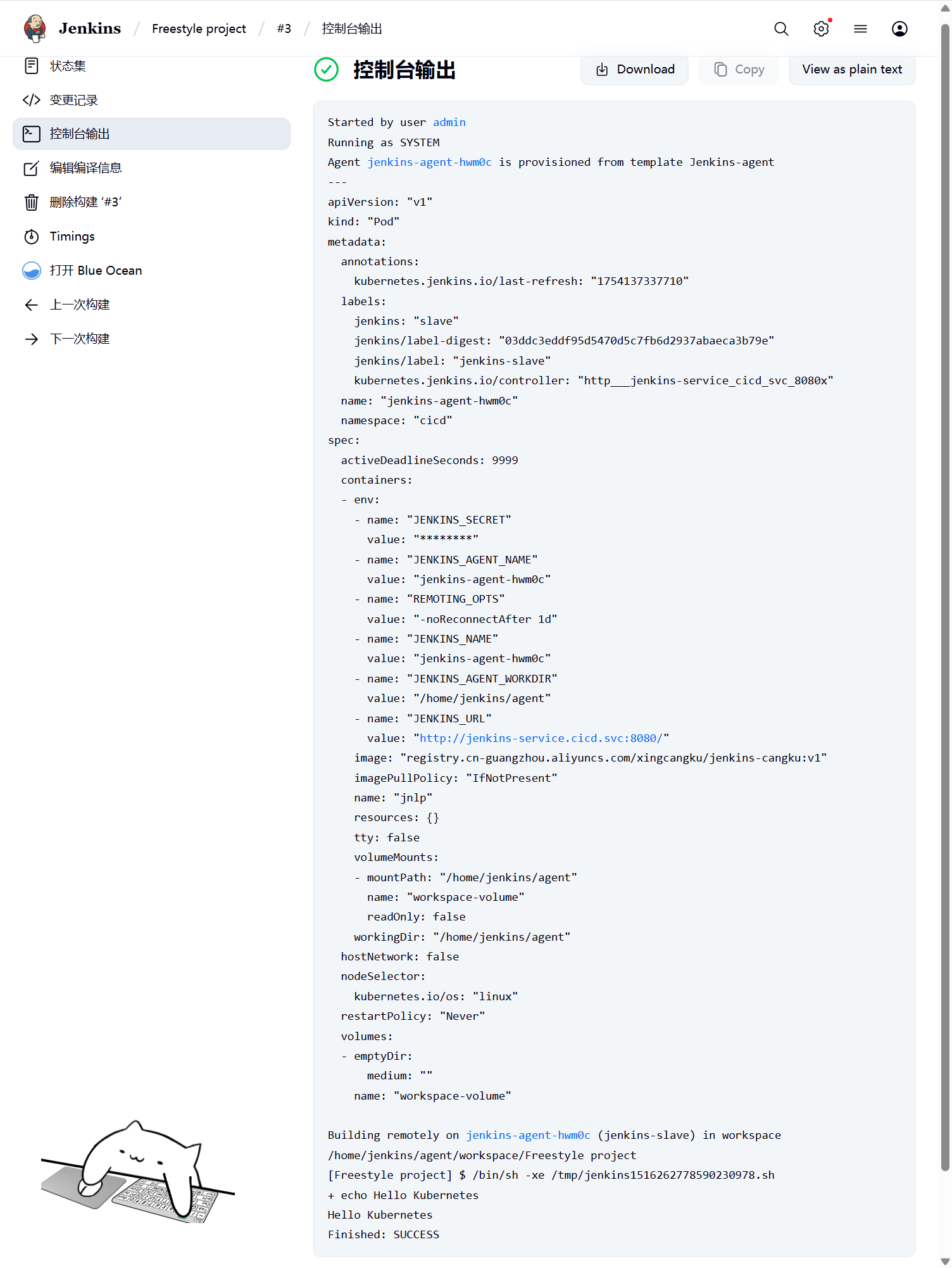
创建一个自由风格的流水线 下面是配置截图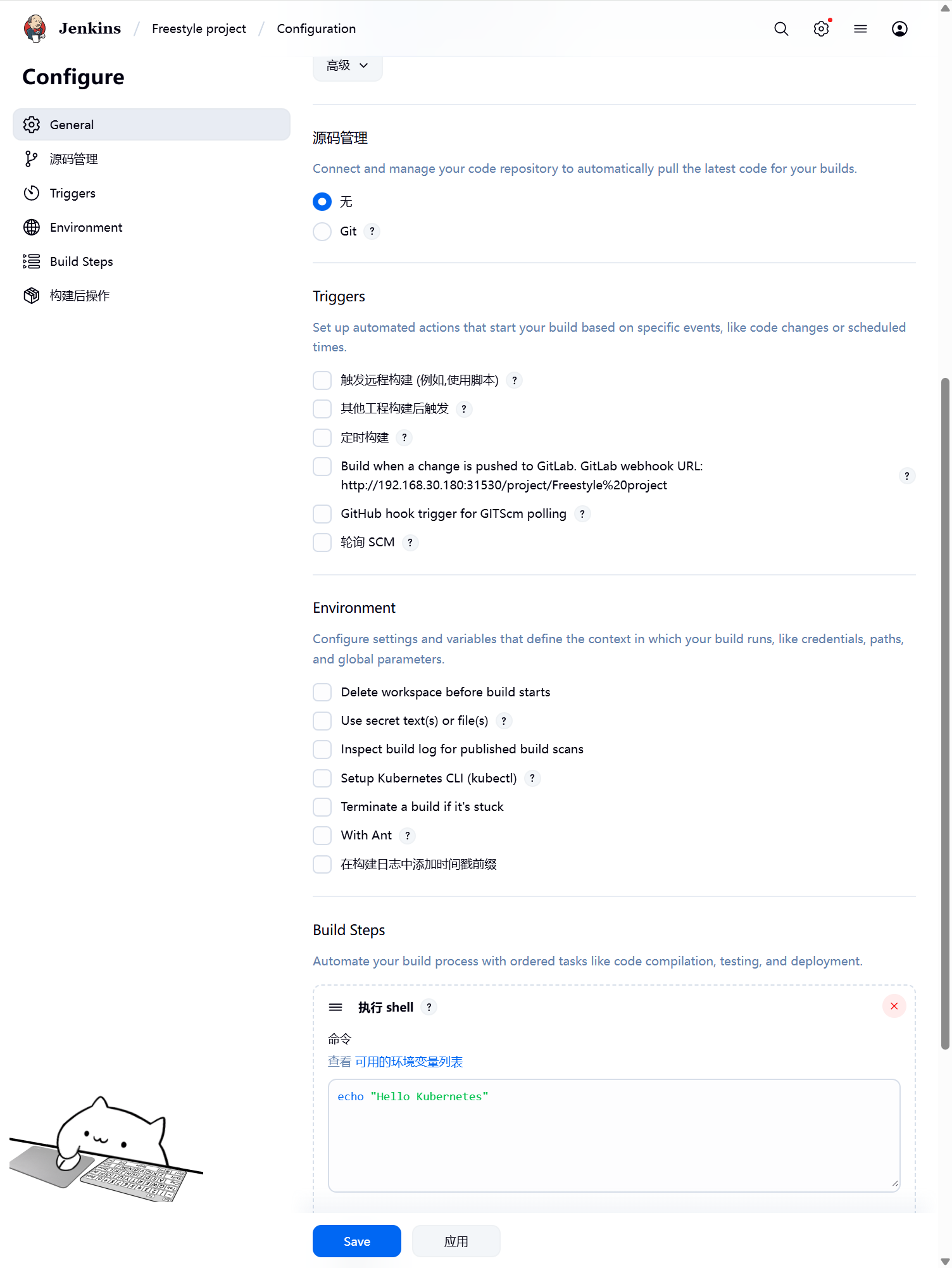
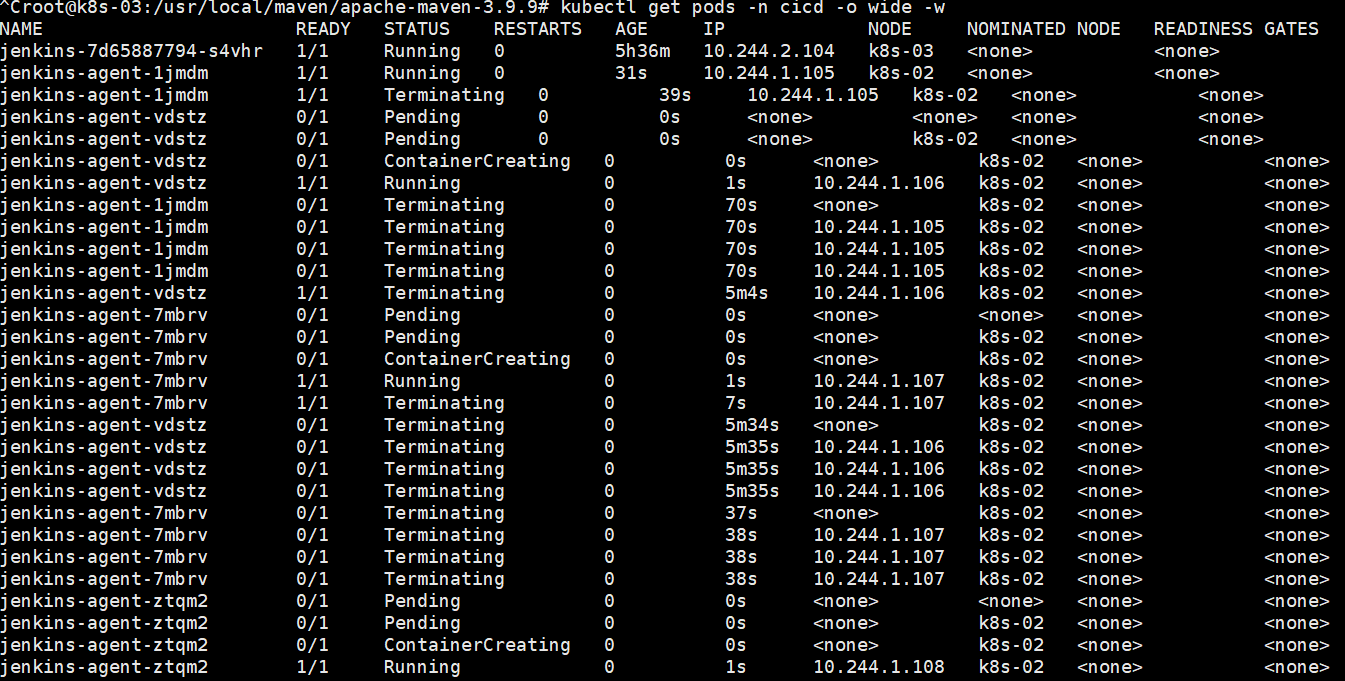
正常的日志显示,会起一个pod来执行的命令结束以后就会销毁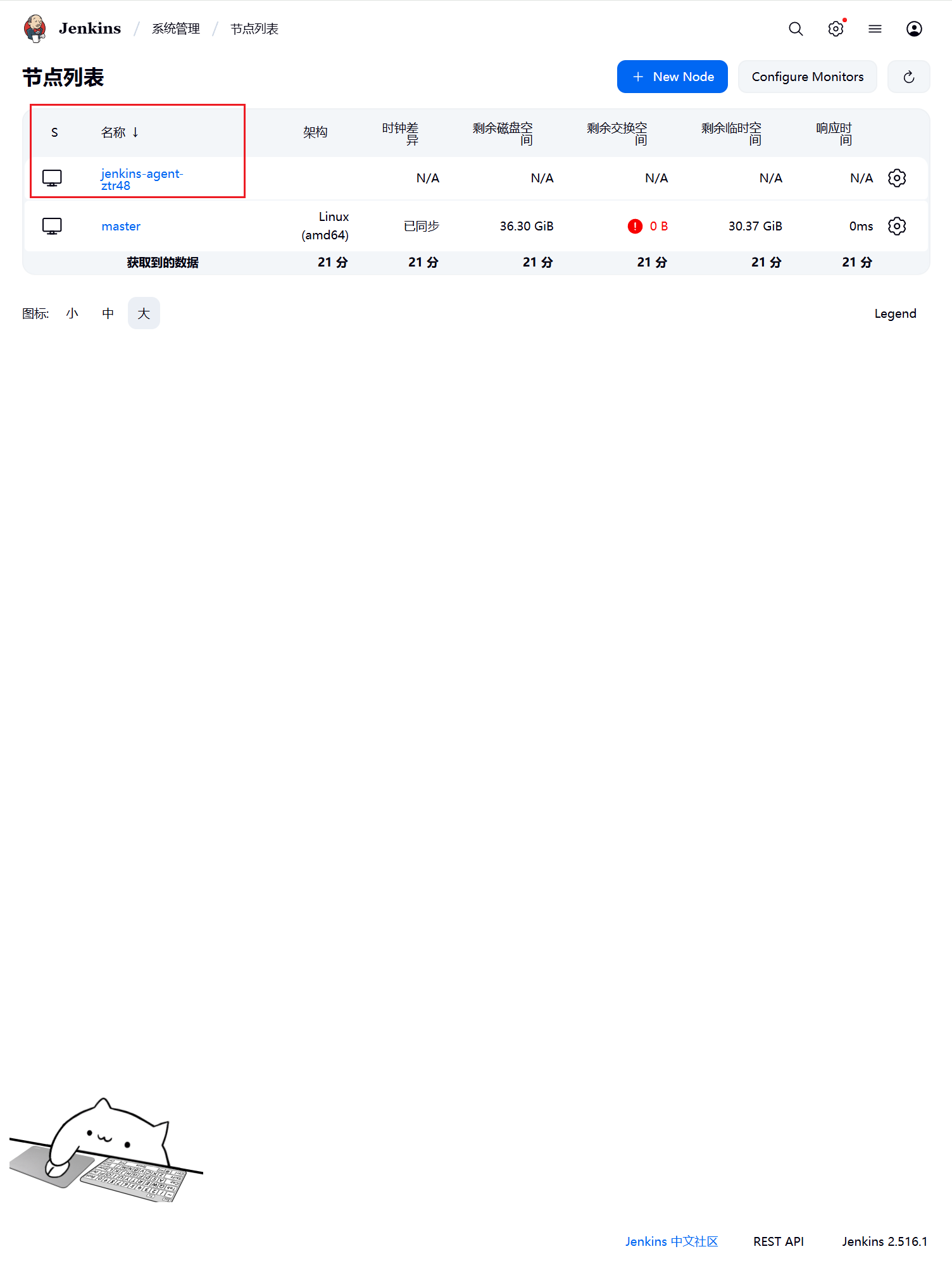
5.3节点开启buildkit服务(可选)
container容器运行时仅能运行容器,如果需要在CICD阶段构建镜像,则需要在执行构建镜像的节点手动安装buildkit服务并启用,具体步骤可参考文档:https://axzys.cn/index.php/archives/536/
也可以在slave pod中新增一个container,运行buildkit服务。5.4配置Pod Template(可选)
配置 Pod Template,就是配置 Jenkins Slave 运行的 Pod 模板,命名空间我们同样是用cicd,Labels设置为jenkins-slave,对于后面执行 Job 的时候需要用到该值,容器名称填写jnlp,这样可以替换默认的agent容器。镜像使用的是刚刚我们制作的slave镜像,加入了 kubectl 等一些实用的工具。
运行命令和命令参数为空。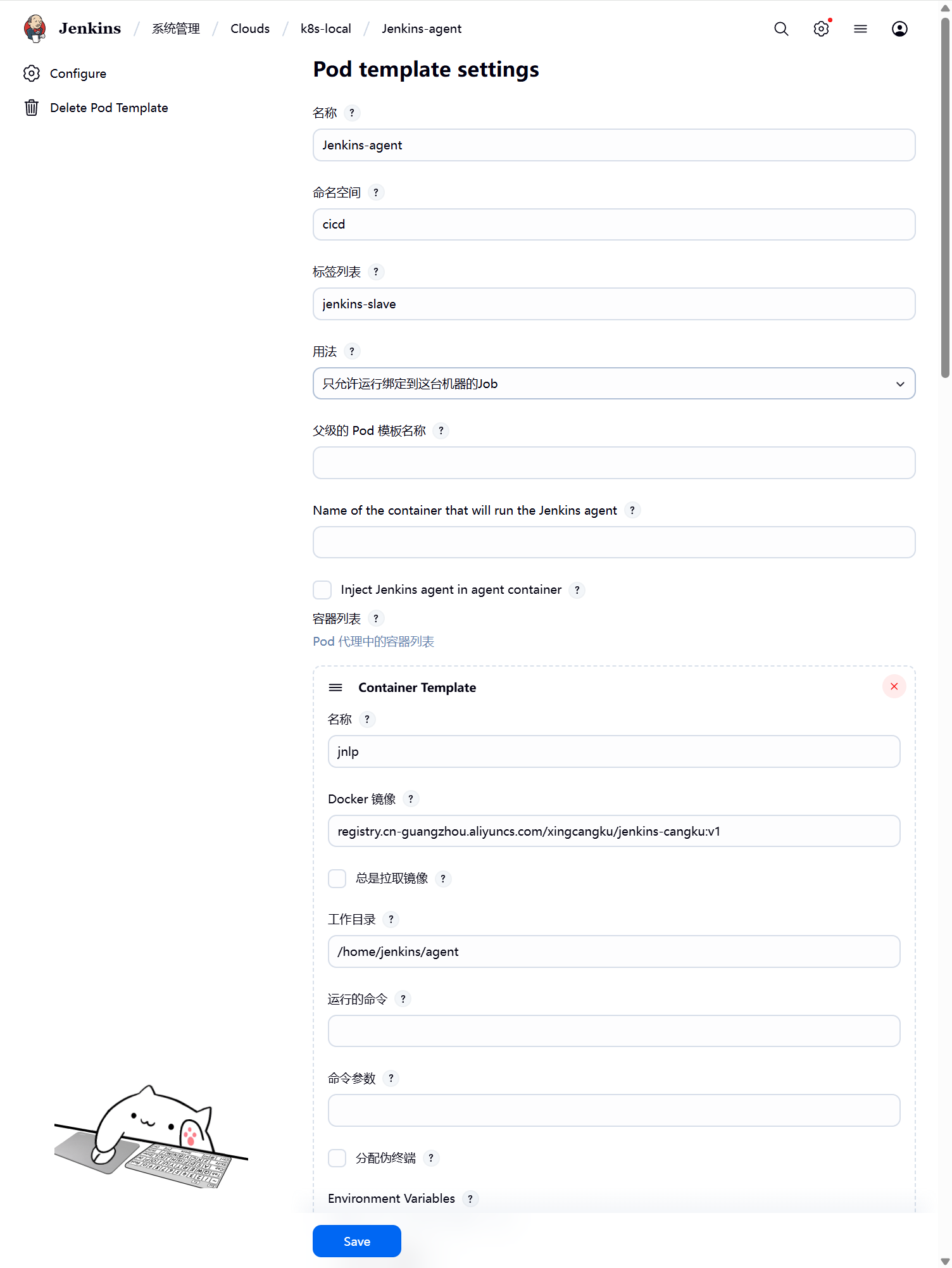
另外需要注意我们这里需要在下面挂载三个目录
/run/containerd/containerd.sock:该文件是用于 Pod 中的容器能够共享宿主机的Container,用于管理container镜像。
/root/.kube:将之前创建的kube-config资源挂载到容器的/root/.kube目录下,这样能够在 Pod 的容器中能够使用 kubectl 工具来访问我们的 Kubernetes 集群,方便我们后面在 Slave Pod 部署 Kubernetes 应用
/run/buildkit:该文件是用于 Pod 中的容器能够共享buildkit进程,用于构建container镜像。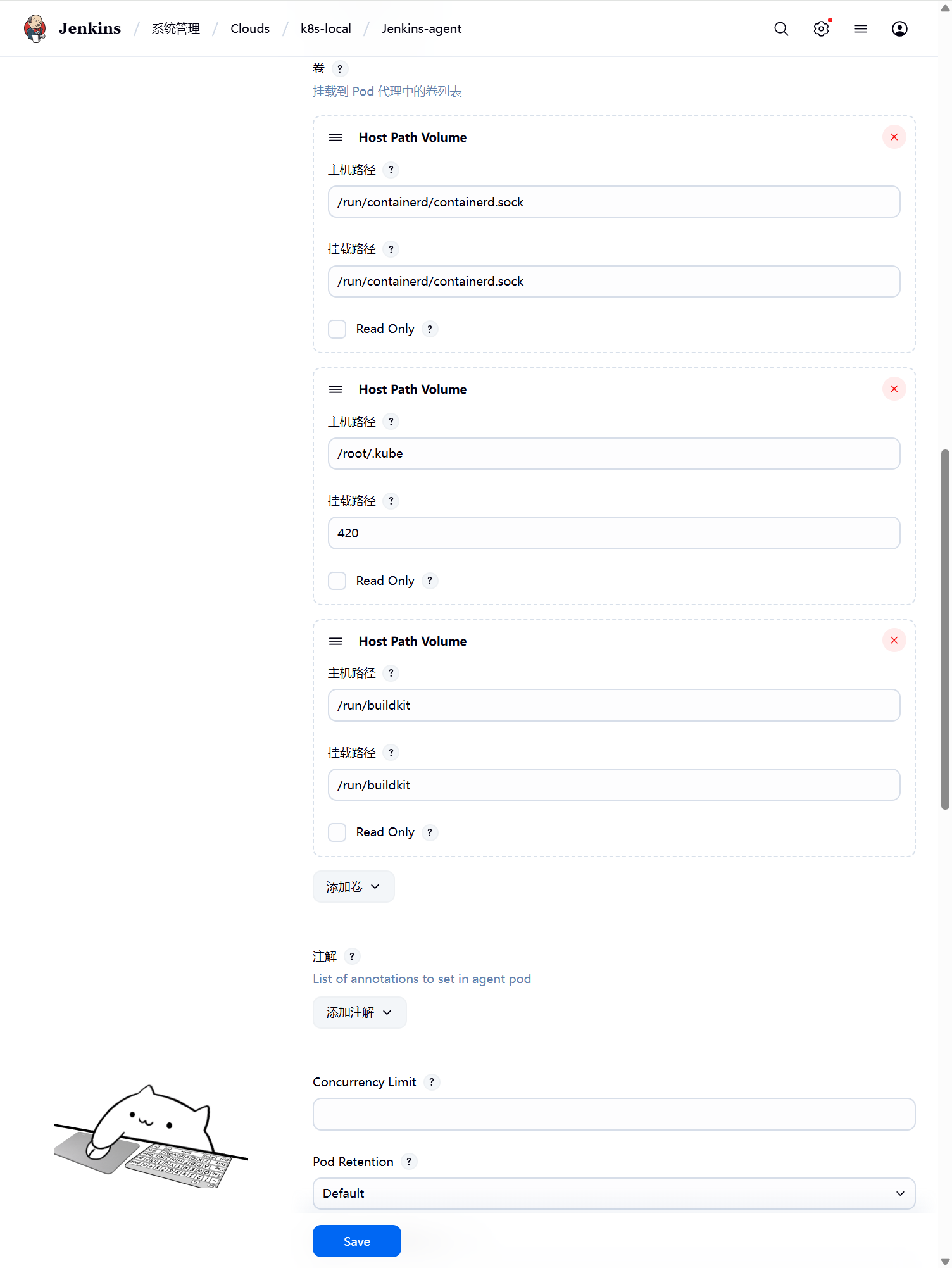
同时指定Service Accoun为之前创建的jenkins-admin
除了在页面配置pod Template外,我们也可以通过pipeline配置。六、测试
Kubernetes 插件的配置工作完成了,接下来我们就来添加一个 Job 任务,看是否能够在 Slave Pod 中执行,任务执行完成后看 Pod 是否会被销毁。6.1自由流水线测试
创建自由流水线任务,勾选限制项目的运行节点,标签表达式填写我们配置的 Slave Pod 中的 Label,这两个地方必须保持一致。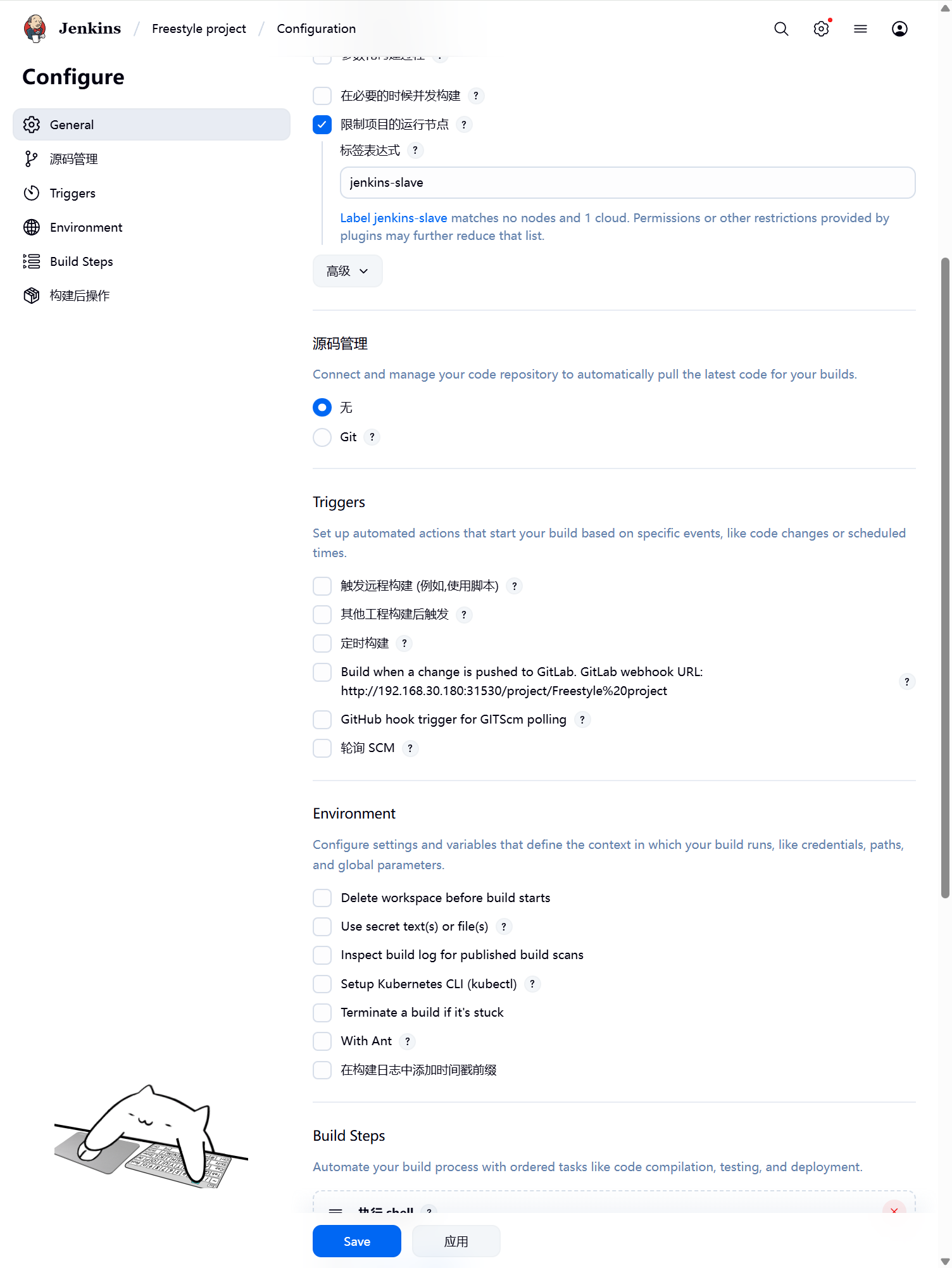
然后往下拉,在 Build 区域选择Execute shellecho "Hello Kubernetes"
echo "测试获取Kubernetes信息"
kubectl get node
echo "测试获取container信息"
nerdctl ns ls
echo "测试buildkitd构建镜像"
echo "FROM registry.cn-guangzhou.aliyuncs.com/xingcangku/busybox-latest:latest" > Dockerfile
echo 'CMD ["echo","hello","container"]' >> Dockerfile
nerdctl build -t buildkitd-test:v1 .
nerdctl images | grep buildkitd-test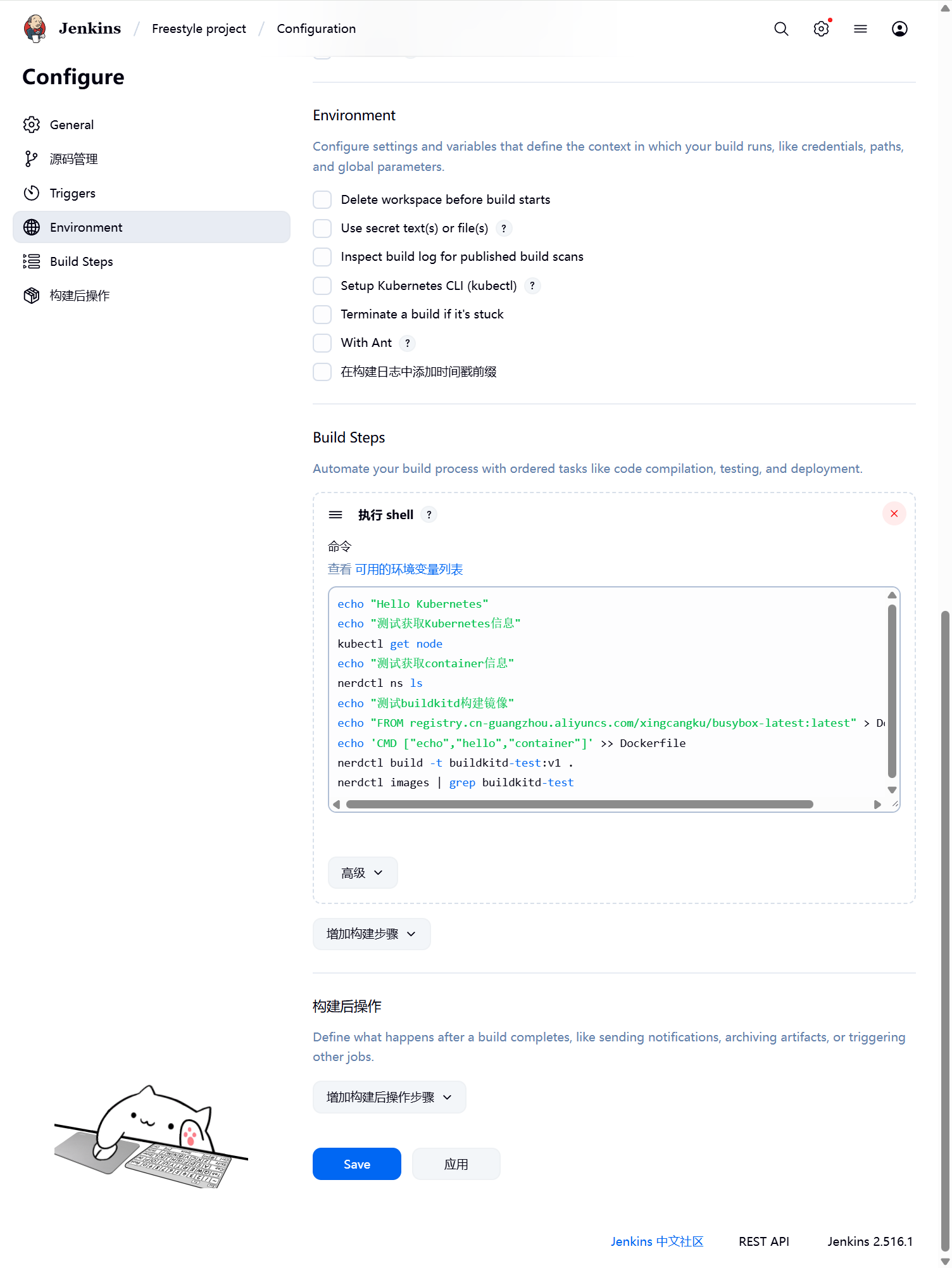
现在我们直接在页面点击做成的 Build now (立即构建)触发构建即可,然后观察 Kubernetes 集群中 Pod 的变化root@k8s-03:~/bin# kubectl get pods -n cicd -o wide -w
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
jenkins-7d65887794-s4vhr 1/1 Running 0 9h 10.244.2.104 k8s-03 <none> <none>
jenkins-agent-8x3mn 0/1 Pending 0 0s <none> <none> <none> <none>
jenkins-agent-8x3mn 0/1 Pending 0 0s <none> k8s-03 <none> <none>
jenkins-agent-8x3mn 0/1 ContainerCreating 0 0s <none> k8s-03 <none> <none>
jenkins-agent-8x3mn 1/1 Running 0 1s 10.244.2.116 k8s-03 <none> <none>
jenkins-agent-8x3mn 1/1 Terminating 0 13s 10.244.2.116 k8s-03 <none> <none>
jenkins-agent-8x3mn 0/1 Terminating 0 13s <none> k8s-03 <none> <none>
jenkins-agent-8x3mn 0/1 Terminating 0 14s 10.244.2.116 k8s-03 <none> <none>
jenkins-agent-8x3mn 0/1 Terminating 0 14s 10.244.2.116 k8s-03 <none> <none>
jenkins-agent-8x3mn 0/1 Terminating 0 14s 10.244.2.116 k8s-03 <none> <none>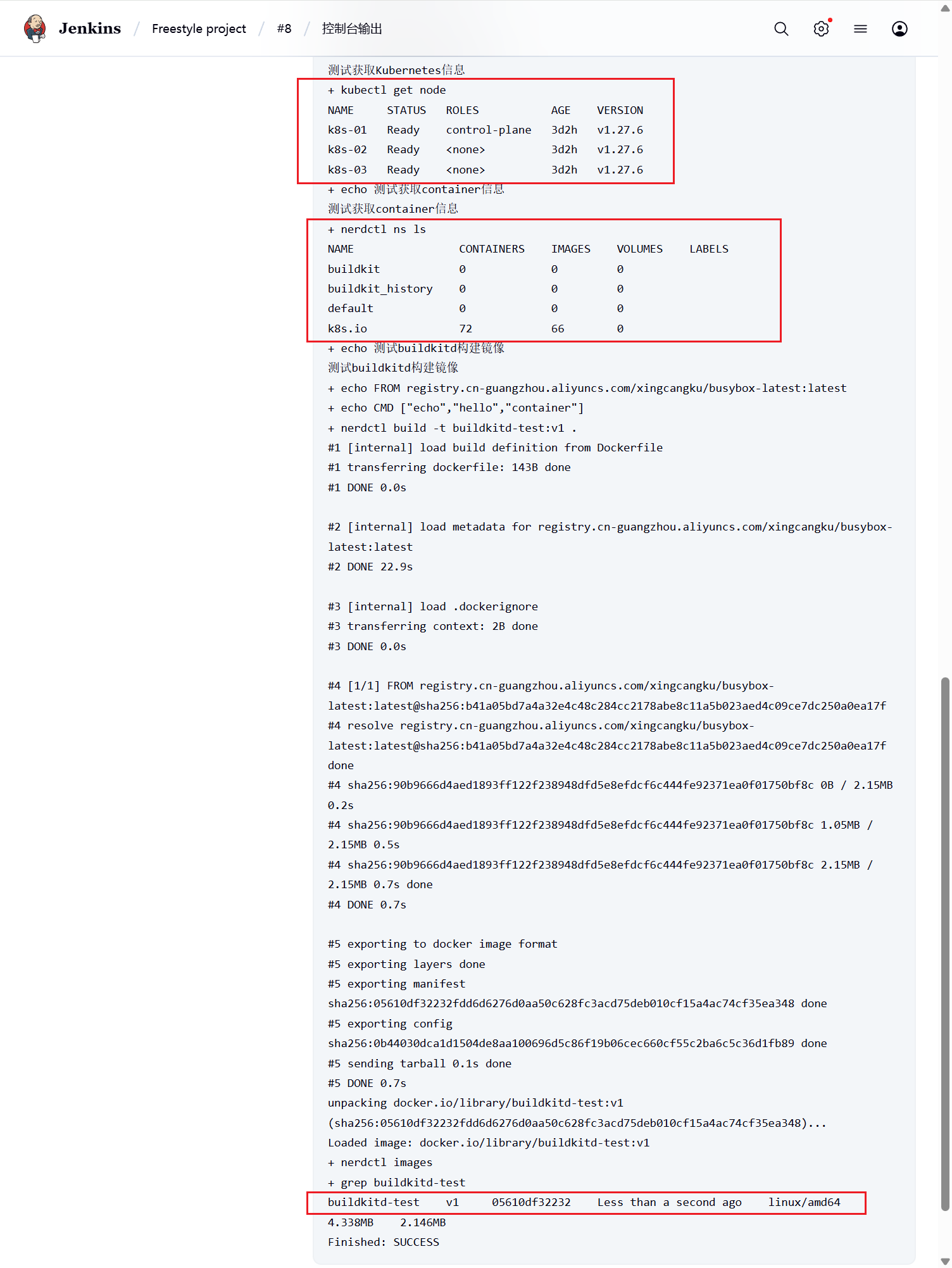
6.2pipeline-使用pod Template
在流水线中指定pipeline脚本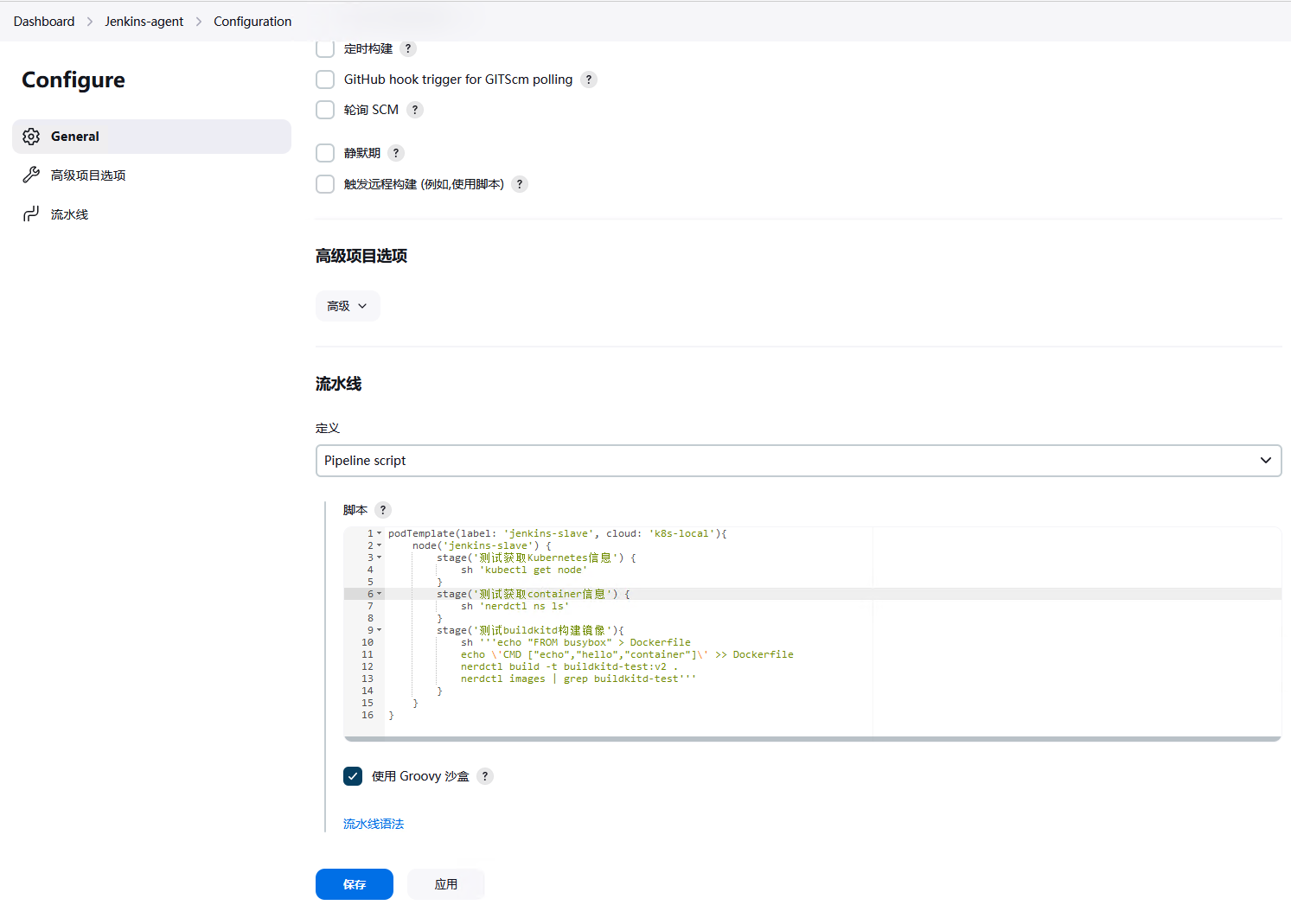
pipeline脚本如下:podTemplate(label: 'jenkins-slave', inheritFrom: 'jenkins-agent', cloud: 'k8s-local'){
node('jenkins-slave') {
stage('测试获取Kubernetes信息') {
sh 'kubectl get node'
}
stage('测试获取container信息') {
sh 'nerdctl ns ls'
}
stage('测试buildkitd构建镜像'){
sh '''echo "FROM busybox" > Dockerfile
echo \'CMD ["echo","hello","container"]\' >> Dockerfile
nerdctl build -t buildkitd-test:v2 .
nerdctl images | grep buildkitd-test'''
}
}
}点击立即构建,查看控制台输出。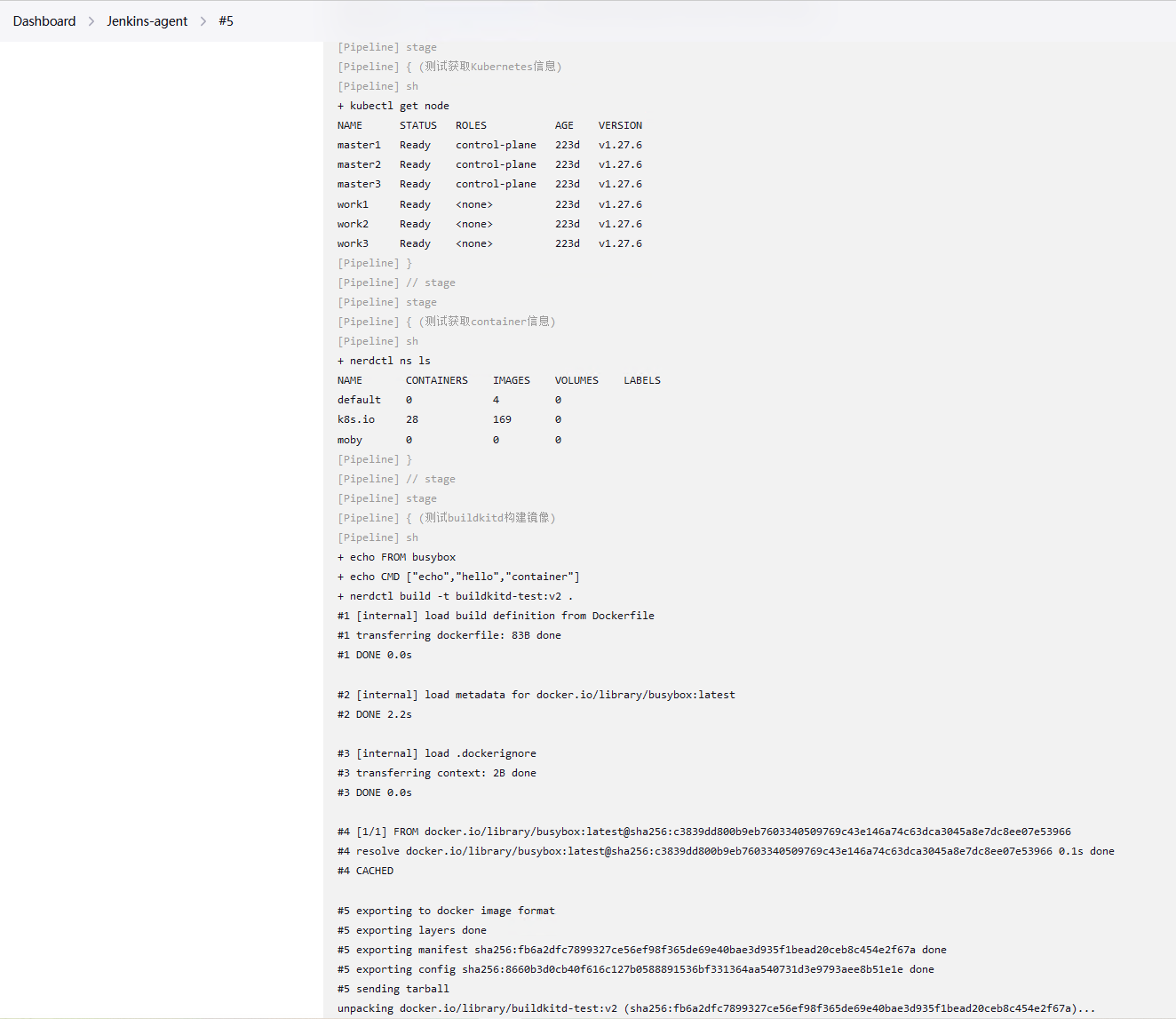
6.3pipeline-自定义pod Template
//创建一个Pod的模板,label为jenkins-agent
podTemplate(label: 'jenkins-agent', cloud: 'k8s-local', containers: [
containerTemplate(
name: 'jnlp',
image: "harbor.local.com/cicd/jenkins-agent:v3",
workingDir: '/home/jenkins/agent'
),
containerTemplate(
name: 'buildkitd',
image: "harbor.local.com/cicd/buildkit:v0.13.2",
privileged: true
)],
volumes:[
hostPathVolume(mountPath: '/run/containerd/containerd.sock', hostPath:'/run/containerd/containerd.sock'),
secretVolume(mountPath: '/root/.kube/', secretName: 'kube-config', defaultMode: '420'),
hostPathVolume(mountPath: '/run/buildkit',hostPath: '/run/buildkit')
]
)
// 使用上文创建的pod模板
{
node('jenkins-agent'){
stage('测试获取Kubernetes信息') {
sh 'kubectl get node'
}
stage('测试获取container信息') {
sh 'nerdctl ns ls'
}
stage('测试buildkitd构建镜像'){
sh '''echo "FROM busybox" > Dockerfile
echo 'CMD ["echo","hello","container"]' >> Dockerfile
nerdctl build -t buildkitd-test:v2 .
nerdctl images | grep buildkitd-test'''
}
}
}运行结果与上文一致。


评论 (0)