一、Project创建
通过项目,可以配置对应用程序的访问控制策略。例如,可以指定哪些用户或团队有权在特定命名空间或集群中进行部署操作。提供了资源隔离的功能,确保不同项目之间的资源不会互相干扰。这有助于维护不同团队或应用程序之间的清晰界限。
最佳实践应该是为每个gitlab group在argoCD中创建对应的Project,便于各个组之间权限资源相互隔离。1.1webUI创建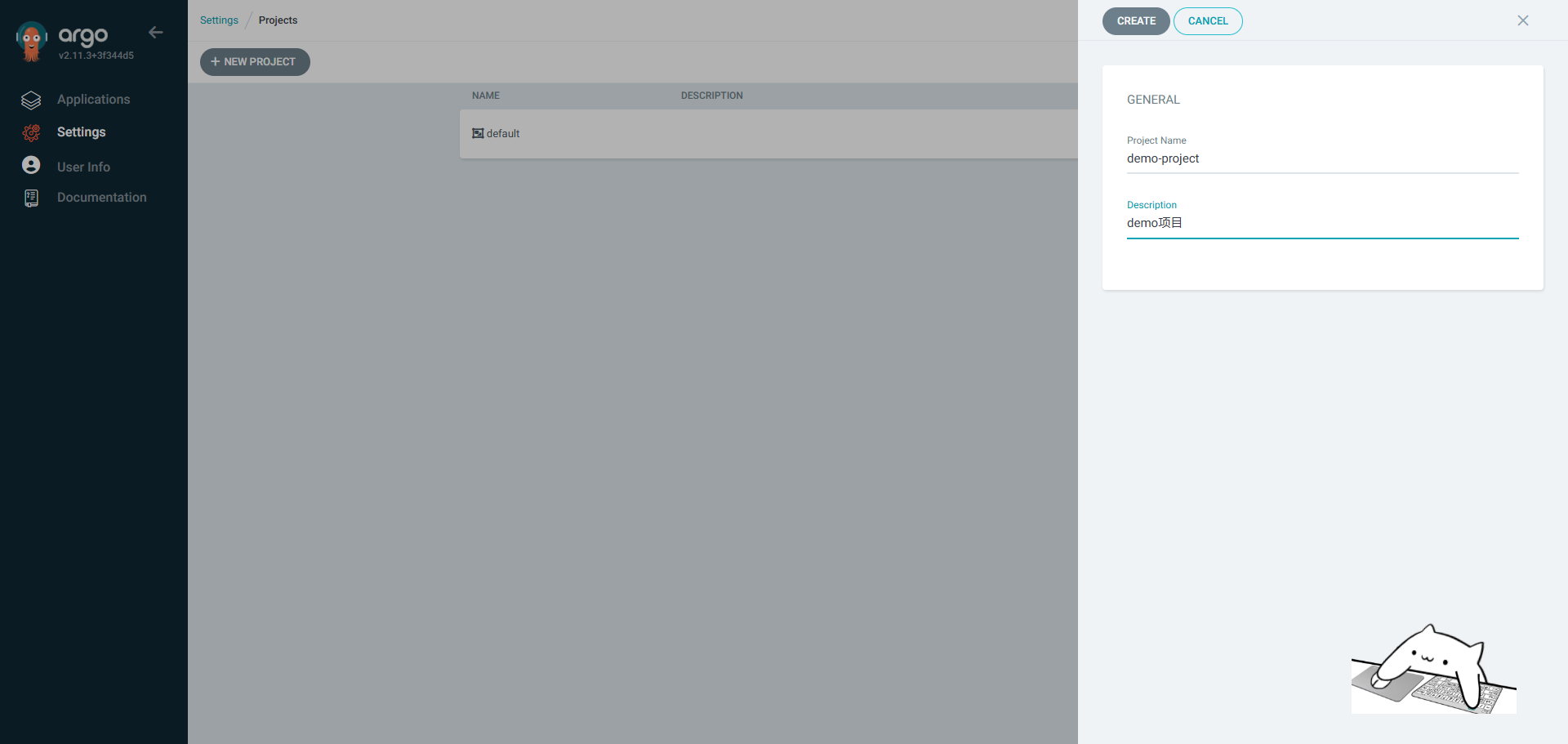
1.2CLI创建
## argocd CLI
# login
argocd login argocd.idevops.site
# list
argocd proj list
# remove
argocd proj remove dev1
# create
argocd proj create --help
argocd proj create dev2
argocd proj list
argocd proj add-source dev2 http://github.com/dev2/app.git1.3yaml创建
示例文档: https://argo-cd.readthedocs.io/en/stable/operator-manual/project.yamlapiVersion: argoproj.io/v1alpha1
kind: AppProject
metadata:
name: dev3
namespace: argocd
finalizers:
- resources-finalizer.argocd.argoproj.io
spec:
description: Example Project
sourceRepos:
- 'https://github.com/dev3/app.git'
destinations:
- namespace: dev3
server: https://kubernetes.default.svc
name: in-cluster
# Deny all cluster-scoped resources from being created, except for Namespace
clusterResourceWhitelist:
- group: ''
kind: Namespace
# Allow all namespaced-scoped resources to be created, except for ResourceQuota, LimitRange, NetworkPolicy
namespaceResourceBlacklist:
- group: ''
kind: ResourceQuota
- group: ''
kind: LimitRange
- group: ''
kind: NetworkPolicy
# Deny all namespaced-scoped resources from being created, except for Deployment and StatefulSet
namespaceResourceWhitelist:
- group: 'apps'
kind: Deployment
- group: 'apps'
kind: StatefulSet二、project配置
2.1webUI配置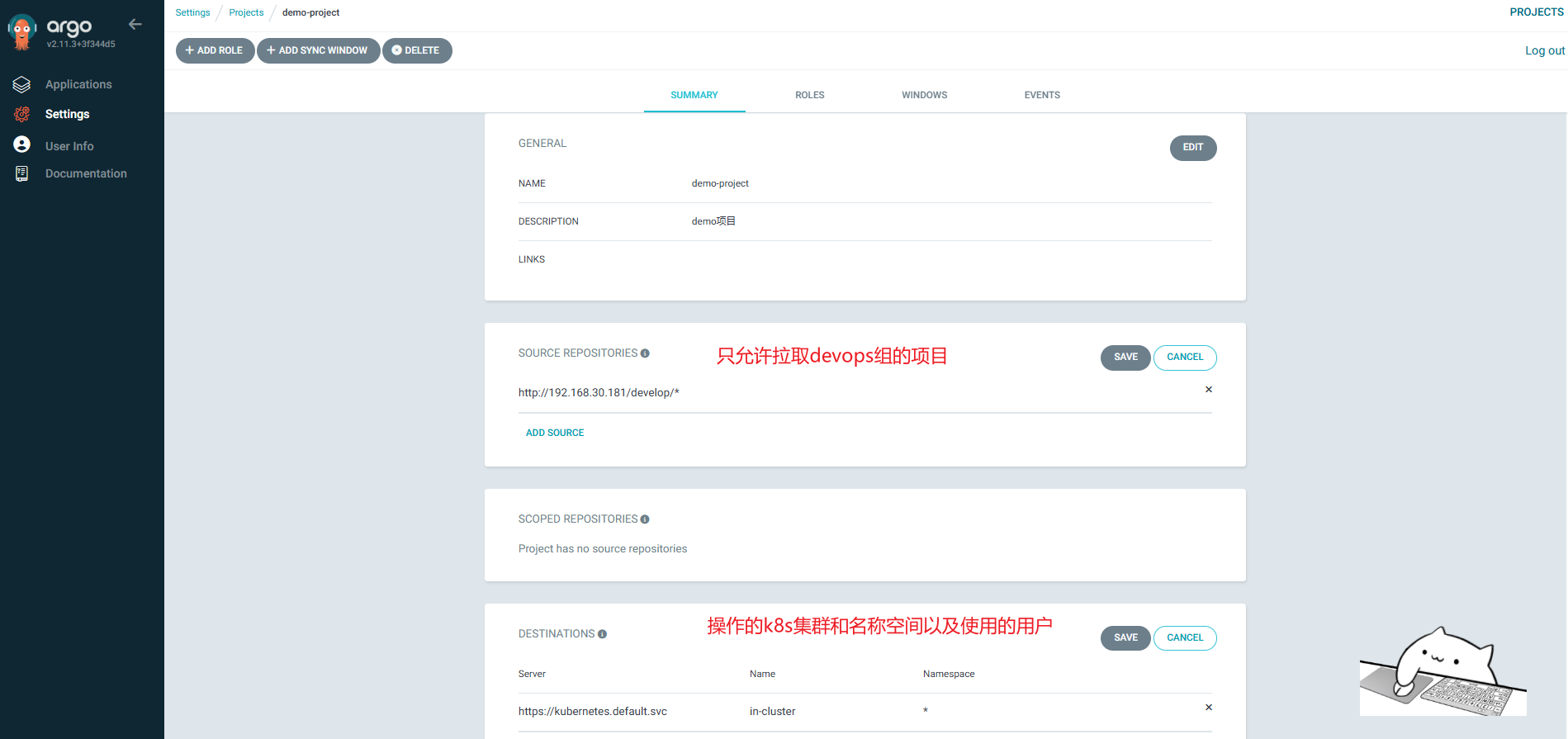
2.2yaml配置
apiVersion: argoproj.io/v1alpha1
kind: AppProject
metadata:
name: dev1
namespace: argocd
spec:
clusterResourceBlacklist:
- group: ""
kind: ""
clusterResourceWhitelist:
- group: ""
kind: Namespace
description: dev1 group
destinations:
- name: in-cluster
namespace: dev1
server: https://kubernetes.default.svc
namespaceResourceWhitelist:
- group: '*'
kind: '*'
roles:
- jwtTokens:
- iat: 1684030305
id: 12764563-0582-4d2d-afbc-ab2712c5c47e
name: dev1-role
policies:
- p, proj:dev1:dev1-role, applications, get, dev1/*, allow
- p, proj:dev1:dev1-role, applications, sync, dev1/*, allow
- p, proj:dev1:dev1-role, applications, delete, dev1/*, deny
sourceRepos:
- http://gitlab.local.com/devops/** ## 根据项目组配置,允许该组下的所有repo
- ""三、ProjectRole
ProjectRole 是一种用于定义在特定项目 (Project) 范围内的访问控制策略的资源。它允许你对项目中的资源进行细粒度的权限管理,指定哪些用户或服务账户可以执行哪些操作。ProjectRole 主要用于增强安全性和隔离性,确保只有被授权的用户或系统组件可以对项目内的应用程序和资源进行特定操作。3.1创建role
我们在demo项目下创建名为dev的角色,配置权限为:允许get sync操作权限,不允许delete操作。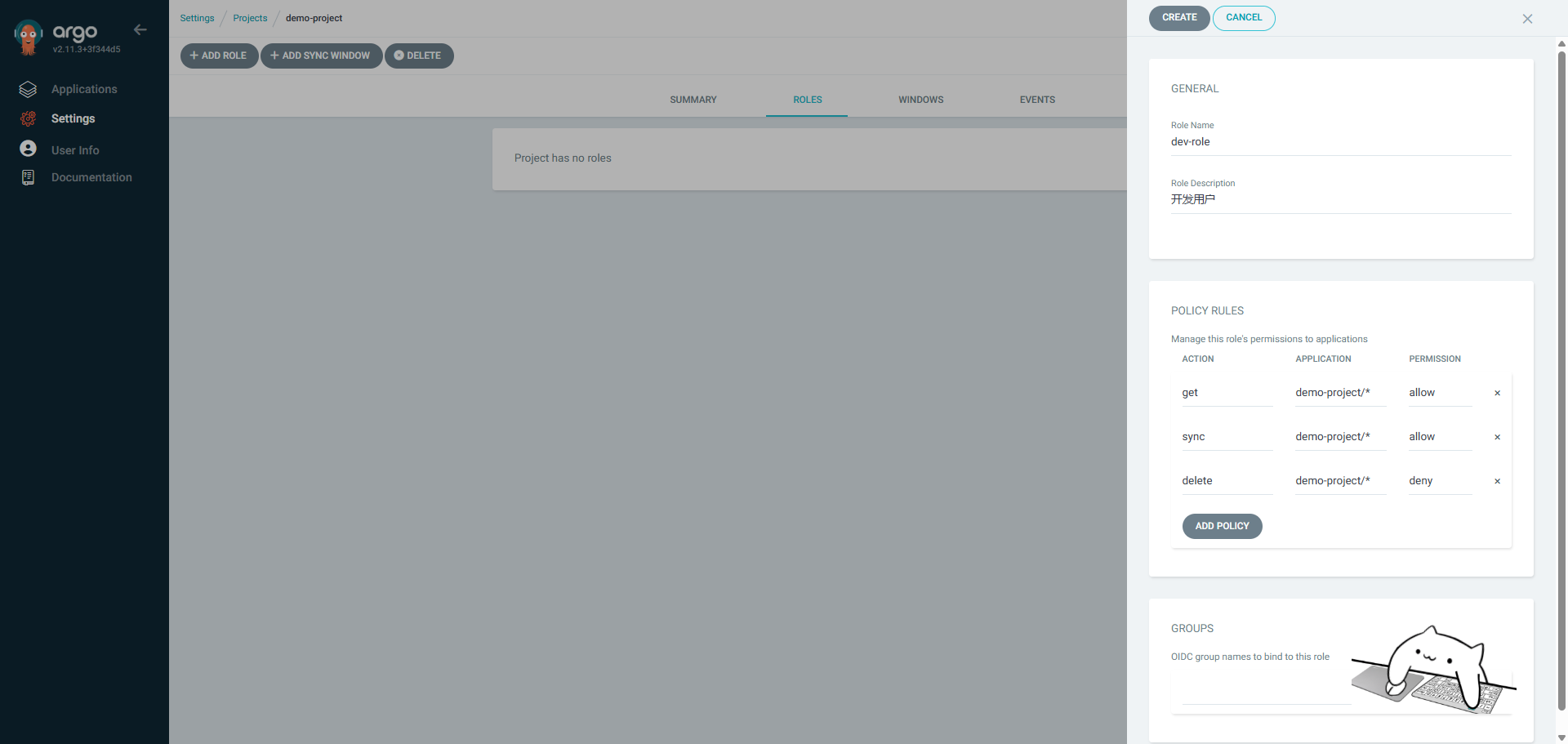
3.2创建JWT Token
root@k8s-01:~/argocd# argocd proj role create-token demo-project dev-role
WARN[0000] Failed to invoke grpc call. Use flag --grpc-web in grpc calls. To avoid this warning message, use flag --grpc-web.
Create token succeeded for proj:demo-project:dev-role.
ID: 9c150b55-848f-436c-88db-fe61e95874fc
Issued At: 2025-08-19T06:31:59Z
Expires At: Never
Token: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJhcmdvY2QiLCJzdWIiOiJwcm9qOmRlbW8tcHJvamVjdDpkZXYtcm9sZSIsIm5iZiI6MTc1NTU4NTExOSwiaWF0IjoxNzU1NTg1MTE5LCJqdGkiOiI5YzE1MGI1NS04NDhmLTQzNmMtODhkYi1mZTYxZTk1ODc0ZmMifQ.54fvz4OOOIo-wsK_hwclCmW0oSIJO1vz2Xgv4Axl08s3.3验证测试
# 注销之前登录的admin账号
[root@tiaoban ~]# argocd logout argocd.local.com
Logged out from 'argocd.local.com'
# 使用token查看app列表
[root@tiaoban ~]# argocd app list --auth-token eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJhcmdvY2QiLCJzdWIiOiJwcm9qOmRlbW8tcHJvamVjdDpkZXYtcm9sZSIsIm5iZiI6MTcxOTExNTk0OSwiaWF0IjoxNzE5MTE1OTQ5LCJqdGkiOiI5MDg5OTc0OC1mYjg2LTRlZjktYjNmMC03MWY4MjBjZjEwZDYifQ.RCLx7U-2RdQ_BD5z8sBW3Ghh5RA6DnwU9VHvmU8EgQM
WARN[0000] Failed to invoke grpc call. Use flag --grpc-web in grpc calls. To avoid this warning message, use flag --grpc-web.
NAME CLUSTER NAMESPACE PROJECT STATUS HEALTH SYNCPOLICY CONDITIONS REPO PATH TARGET
argocd/demo https://kubernetes.default.svc demo-project Synced Healthy Auto <none> http://gitlab.local.com/devops/argo-demo.git manifests HEAD
# 使用token执行sync操作
[root@tiaoban ~]# argocd app sync argocd/demo --auth-token eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJhcmdvY2QiLCJzdWIiOiJwcm9qOmRlbW8tcHJvamVjdDpkZXYtcm9sZSIsIm5iZiI6MTcxOTExNTk0OSwiaWF0IjoxNzE5MTE1OTQ5LCJqdGkiOiI5MDg5OTc0OC1mYjg2LTRlZjktYjNmMC03MWY4MjBjZjEwZDYifQ.RCLx7U-2RdQ_BD5z8sBW3Ghh5RA6DnwU9VHvmU8EgQM
WARN[0000] Failed to invoke grpc call. Use flag --grpc-web in grpc calls. To avoid this warning message, use flag --grpc-web.
TIMESTAMP GROUP KIND NAMESPACE NAME STATUS HEALTH HOOK MESSAGE
2024-06-23T12:20:07+08:00 Service default myapp Synced Healthy
2024-06-23T12:20:07+08:00 apps Deployment default myapp Synced Healthy
2024-06-23T12:20:07+08:00 traefik.containo.us IngressRoute default myapp Synced
2024-06-23T12:20:07+08:00 traefik.containo.us IngressRoute default myapp Synced ingressroute.traefik.containo.us/myapp unchanged
2024-06-23T12:20:07+08:00 Service default myapp Synced Healthy service/myapp unchanged
2024-06-23T12:20:07+08:00 apps Deployment default myapp Synced Healthy deployment.apps/myapp unchanged
Name: argocd/demo
Project: demo-project
Server: https://kubernetes.default.svc
Namespace:
URL: https://argocd.local.com/applications/argocd/demo
Source:
- Repo: http://gitlab.local.com/devops/argo-demo.git
Target: HEAD
Path: manifests
SyncWindow: Sync Allowed
Sync Policy: Automated
Sync Status: Synced to HEAD (0ea8019)
Health Status: Healthy
Operation: Sync
Sync Revision: 0ea801988a54f0ad73808454f2fce5030d3e28ef
Phase: Succeeded
Start: 2024-06-23 12:20:07 +0800 CST
Finished: 2024-06-23 12:20:07 +0800 CST
Duration: 0s
Message: successfully synced (all tasks run)
GROUP KIND NAMESPACE NAME STATUS HEALTH HOOK MESSAGE
Service default myapp Synced Healthy service/myapp unchanged
apps Deployment default myapp Synced Healthy deployment.apps/myapp unchanged
traefik.containo.us IngressRoute default myapp Synced ingressroute.traefik.containo.us/myapp unchanged
# 使用token删除应用,提示权限拒绝
[root@tiaoban ~]# argocd app delete argocd/demo --auth-token eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJhcmdvY2QiLCJzdWIiOiJwcm9qOmRlbW8tcHJvamVjdDpkZXYtcm9sZSIsIm5iZiI6MTcxOTExNTk0OSwiaWF0IjoxNzE5MTE1OTQ5LCJqdGkiOiI5MDg5OTc0OC1mYjg2LTRlZjktYjNmMC03MWY4MjBjZjEwZDYifQ.RCLx7U-2RdQ_BD5z8sBW3Ghh5RA6DnwU9VHvmU8EgQM
WARN[0000] Failed to invoke grpc call. Use flag --grpc-web in grpc calls. To avoid this warning message, use flag --grpc-web.
Are you sure you want to delete 'argocd/demo' and all its resources? [y/n] y
FATA[0001] rpc error: code = PermissionDenied desc = permission denied: applications, delete, demo-project/demo, sub: proj:demo-project:dev-role, iat: 2024-06-23T04:12:29Z

评论 (0)