一、储备知识:
ingress有3种部署方案(到底用k8s中的哪种控制器资源来进行管理有何区别)
按照是否需要为ingress的pod创建svc来区分,可以分为两大方案
1、需要创建(非hostNetwork网络模式)
depoyment来部署ingress的pod(pod的网络不是hostNetwork) + svc(type为LoadBalancer)
depoyment来部署ingress的pod(pod的网络不是hostNetwork) + svc(type为NodePort)
2、不需要创建(用hostNetwork网络模式)转发路径更短,效率更高
Daemonset来部署ingress的pod(pod的网络就是hostNetwork)二、先部署depoyment来部署ingress的pod(pod的网络不是hostNetwork) + svc(type为NodePort)
先部署ingress
apiVersion: v1
kind: Namespace
metadata:
labels:
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
name: ingress-nginx
---
apiVersion: v1
automountServiceAccountToken: true
kind: ServiceAccount
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx
namespace: ingress-nginx
---
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx-admission
namespace: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx
namespace: ingress-nginx
rules:
- apiGroups:
- ""
resources:
- namespaces
verbs:
- get
- apiGroups:
- ""
resources:
- configmaps
- pods
- secrets
- endpoints
verbs:
- get
- list
- watch
- apiGroups:
- ""
resources:
- services
verbs:
- get
- list
- watch
- apiGroups:
- networking.k8s.io
resources:
- ingresses
verbs:
- get
- list
- watch
- apiGroups:
- networking.k8s.io
resources:
- ingresses/status
verbs:
- update
- apiGroups:
- networking.k8s.io
resources:
- ingressclasses
verbs:
- get
- list
- watch
- apiGroups:
- coordination.k8s.io
resourceNames:
- ingress-nginx-leader
resources:
- leases
verbs:
- get
- update
- apiGroups:
- coordination.k8s.io
resources:
- leases
verbs:
- create
- apiGroups:
- ""
resources:
- events
verbs:
- create
- patch
- apiGroups:
- discovery.k8s.io
resources:
- endpointslices
verbs:
- list
- watch
- get
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx-admission
namespace: ingress-nginx
rules:
- apiGroups:
- ""
resources:
- secrets
verbs:
- get
- create
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
labels:
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx
rules:
- apiGroups:
- ""
resources:
- configmaps
- endpoints
- nodes
- pods
- secrets
- namespaces
verbs:
- list
- watch
- apiGroups:
- coordination.k8s.io
resources:
- leases
verbs:
- list
- watch
- apiGroups:
- ""
resources:
- nodes
verbs:
- get
- apiGroups:
- ""
resources:
- services
verbs:
- get
- list
- watch
- apiGroups:
- networking.k8s.io
resources:
- ingresses
verbs:
- get
- list
- watch
- apiGroups:
- ""
resources:
- events
verbs:
- create
- patch
- apiGroups:
- networking.k8s.io
resources:
- ingresses/status
verbs:
- update
- apiGroups:
- networking.k8s.io
resources:
- ingressclasses
verbs:
- get
- list
- watch
- apiGroups:
- discovery.k8s.io
resources:
- endpointslices
verbs:
- list
- watch
- get
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx-admission
rules:
- apiGroups:
- admissionregistration.k8s.io
resources:
- validatingwebhookconfigurations
verbs:
- get
- update
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx
namespace: ingress-nginx
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: ingress-nginx
subjects:
- kind: ServiceAccount
name: ingress-nginx
namespace: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx-admission
namespace: ingress-nginx
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: ingress-nginx-admission
subjects:
- kind: ServiceAccount
name: ingress-nginx-admission
namespace: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
labels:
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: ingress-nginx
subjects:
- kind: ServiceAccount
name: ingress-nginx
namespace: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx-admission
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: ingress-nginx-admission
subjects:
- kind: ServiceAccount
name: ingress-nginx-admission
namespace: ingress-nginx
---
apiVersion: v1
data:
allow-snippet-annotations: "false"
kind: ConfigMap
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx-controller
namespace: ingress-nginx
---
apiVersion: v1
kind: Service
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx-controller
namespace: ingress-nginx
spec:
ipFamilies:
- IPv4
ipFamilyPolicy: SingleStack
ports:
- appProtocol: http
name: http
port: 80
protocol: TCP
targetPort: http
- appProtocol: https
name: https
port: 443
protocol: TCP
targetPort: https
selector:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
type: NodePort
---
apiVersion: v1
kind: Service
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx-controller-admission
namespace: ingress-nginx
spec:
ports:
- appProtocol: https
name: https-webhook
port: 443
targetPort: webhook
selector:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
type: ClusterIP
---
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx-controller
namespace: ingress-nginx
spec:
minReadySeconds: 0
revisionHistoryLimit: 10
selector:
matchLabels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
strategy:
rollingUpdate:
maxUnavailable: 1
type: RollingUpdate
template:
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
spec:
containers:
- args:
- /nginx-ingress-controller
- --election-id=ingress-nginx-leader
- --controller-class=k8s.io/ingress-nginx
- --ingress-class=nginx
- --configmap=$(POD_NAMESPACE)/ingress-nginx-controller
- --validating-webhook=:8443
- --validating-webhook-certificate=/usr/local/certificates/cert
- --validating-webhook-key=/usr/local/certificates/key
- --enable-metrics=false
env:
- name: POD_NAME
valueFrom:
fieldRef:
fieldPath: metadata.name
- name: POD_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
- name: LD_PRELOAD
value: /usr/local/lib/libmimalloc.so
image: registry.cn-qingdao.aliyuncs.com/egon-k8s-test/ingress-controller:v1.10.1
imagePullPolicy: IfNotPresent
lifecycle:
preStop:
exec:
command:
- /wait-shutdown
livenessProbe:
failureThreshold: 5
httpGet:
path: /healthz
port: 10254
scheme: HTTP
initialDelaySeconds: 10
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 1
name: controller
ports:
- containerPort: 80
name: http
protocol: TCP
- containerPort: 443
name: https
protocol: TCP
- containerPort: 8443
name: webhook
protocol: TCP
readinessProbe:
failureThreshold: 3
httpGet:
path: /healthz
port: 10254
scheme: HTTP
initialDelaySeconds: 10
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 1
resources:
requests:
cpu: 100m
memory: 90Mi
securityContext:
allowPrivilegeEscalation: false
capabilities:
add:
- NET_BIND_SERVICE
drop:
- ALL
readOnlyRootFilesystem: false
runAsNonRoot: true
runAsUser: 101
seccompProfile:
type: RuntimeDefault
volumeMounts:
- mountPath: /usr/local/certificates/
name: webhook-cert
readOnly: true
dnsPolicy: ClusterFirst
nodeSelector:
kubernetes.io/os: linux
serviceAccountName: ingress-nginx
terminationGracePeriodSeconds: 300
volumes:
- name: webhook-cert
secret:
secretName: ingress-nginx-admission
---
apiVersion: batch/v1
kind: Job
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx-admission-create
namespace: ingress-nginx
spec:
template:
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx-admission-create
spec:
containers:
- args:
- create
- --host=ingress-nginx-controller-admission,ingress-nginx-controller-admission.$(POD_NAMESPACE).svc
- --namespace=$(POD_NAMESPACE)
- --secret-name=ingress-nginx-admission
env:
- name: POD_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
image: registry.cn-qingdao.aliyuncs.com/egon-k8s-test/kube-webhook-certgen:v1.4.1
imagePullPolicy: IfNotPresent
name: create
securityContext:
allowPrivilegeEscalation: false
capabilities:
drop:
- ALL
readOnlyRootFilesystem: true
runAsNonRoot: true
runAsUser: 65532
seccompProfile:
type: RuntimeDefault
nodeSelector:
kubernetes.io/os: linux
restartPolicy: OnFailure
serviceAccountName: ingress-nginx-admission
---
apiVersion: batch/v1
kind: Job
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx-admission-patch
namespace: ingress-nginx
spec:
template:
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx-admission-patch
spec:
containers:
- args:
- patch
- --webhook-name=ingress-nginx-admission
- --namespace=$(POD_NAMESPACE)
- --patch-mutating=false
- --secret-name=ingress-nginx-admission
- --patch-failure-policy=Fail
env:
- name: POD_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
image: registry.cn-qingdao.aliyuncs.com/egon-k8s-test/kube-webhook-certgen:v1.4.1
imagePullPolicy: IfNotPresent
name: patch
securityContext:
allowPrivilegeEscalation: false
capabilities:
drop:
- ALL
readOnlyRootFilesystem: true
runAsNonRoot: true
runAsUser: 65532
seccompProfile:
type: RuntimeDefault
nodeSelector:
kubernetes.io/os: linux
restartPolicy: OnFailure
serviceAccountName: ingress-nginx-admission
---
apiVersion: networking.k8s.io/v1
kind: IngressClass
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: nginx
spec:
controller: k8s.io/ingress-nginx
---
apiVersion: admissionregistration.k8s.io/v1
kind: ValidatingWebhookConfiguration
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx-admission
webhooks:
- admissionReviewVersions:
- v1
clientConfig:
service:
name: ingress-nginx-controller-admission
namespace: ingress-nginx
path: /networking/v1/ingresses
failurePolicy: Fail
matchPolicy: Equivalent
name: validate.nginx.ingress.kubernetes.io
rules:
- apiGroups:
- networking.k8s.io
apiVersions:
- v1
operations:
- CREATE
- UPDATE
resources:
- ingresses
sideEffects: None
{/collapse-item}
{collapse-item label="kubectl apply -f deploy.yaml"}
折叠内容二
namespace/ingress-nginx created
serviceaccount/ingress-nginx created
serviceaccount/ingress-nginx-admission created
role.rbac.authorization.k8s.io/ingress-nginx created
role.rbac.authorization.k8s.io/ingress-nginx-admission created
clusterrole.rbac.authorization.k8s.io/ingress-nginx created
clusterrole.rbac.authorization.k8s.io/ingress-nginx-admission created
rolebinding.rbac.authorization.k8s.io/ingress-nginx created
rolebinding.rbac.authorization.k8s.io/ingress-nginx-admission created
clusterrolebinding.rbac.authorization.k8s.io/ingress-nginx created
clusterrolebinding.rbac.authorization.k8s.io/ingress-nginx-admission created
configmap/ingress-nginx-controller created
service/ingress-nginx-controller created
service/ingress-nginx-controller-admission created
deployment.apps/ingress-nginx-controller created
job.batch/ingress-nginx-admission-create created
job.batch/ingress-nginx-admission-patch created
ingressclass.networking.k8s.io/nginx created
validatingwebhookconfiguration.admissionregistration.k8s.io/ingress-nginx-admission created
[root@k8s-master-01 test2]# grep -i imge deploy.yaml
[root@k8s-master-01 test2]# grep -i image deploy.yaml
image: registry.cn-qingdao.aliyuncs.com/egon-k8s-test/ingress-controller:v1.10.1
imagePullPolicy: IfNotPresent
image: registry.cn-qingdao.aliyuncs.com/egon-k8s-test/kube-webhook-certgen:v1.4.1
imagePullPolicy: IfNotPresent
image: registry.cn-qingdao.aliyuncs.com/egon-k8s-test/kube-webhook-certgen:v1.4.1
imagePullPolicy: IfNotPresent{/collapse-item}
查看部署好的ingress
[root@k8s-master-01 test2]# kubectl -n ingress-nginx get pods
NAME READY STATUS RESTARTS AGE
ingress-nginx-admission-create-2pz6l 0/1 Completed 0 90s
ingress-nginx-admission-patch-m7zkg 0/1 Completed 0 90s
ingress-nginx-controller-8698cc7676-2lth6 1/1 Running 0 90s
[root@k8s-master-01 test2]# kubectl -n ingress-nginx get deployments.apps
NAME READY UP-TO-DATE AVAILABLE AGE
ingress-nginx-controller 1/1 1 1 2m7s
[root@k8s-master-01 test2]# kubectl -n ingress-nginx get svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
ingress-nginx-controller NodePort 10.111.188.71 <none> 80:32593/TCP,443:32318/TCP 4m46s
ingress-nginx-controller-admission ClusterIP 10.108.110.90 <none> 443/TCP 创建微服务和对应的svc
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
app: gowebhost
name: gowebhost
spec:
replicas: 2
selector:
matchLabels:
app: gowebhost
strategy: {}
template:
metadata:
labels:
app: gowebhost
spec:
containers:
- image: nginx:1.18
name: nginx
---
apiVersion: v1
kind: Service
metadata:
creationTimestamp: null
labels:
app: gowebhost
name: gowebhost
spec:
ports:
- port: 9999
protocol: TCP
targetPort: 80
selector:
app: gowebhost
type: ClusterIP
status:
loadBalancer: {}{/collapse-item}
{collapse-item label="cat gowebip-svc.yaml"}
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
app: gowebip
name: gowebip
spec:
replicas: 2
selector:
matchLabels:
app: gowebip
strategy: {}
template:
metadata:
labels:
app: gowebip
spec:
containers:
- image: nginx:1.18
name: nginx
---
apiVersion: v1
kind: Service
metadata:
creationTimestamp: null
labels:
app: gowebip
name: gowebip
spec:
ports:
- port: 8888
protocol: TCP
targetPort: 80
selector:
app: gowebip
type: ClusterIP
status:
loadBalancer: {}
{/collapse-item}
[root@k8s-master-01 test2]# kubectl apply -f gowebip-svc.yaml
deployment.apps/gowebip created
service/gowebip created
[root@k8s-master-01 test2]# kubectl apply -f gowebhost-svc.yaml
deployment.apps/gowebhost created
service/gowebhost created
[root@k8s-master-01 test2]# kubectl get pods
NAME READY STATUS RESTARTS AGE
busybox1 1/1 Running 3 (20m ago) 7h56m
busybox2 1/1 Running 3 (20m ago) 7h56m
gowebhost-5d6cf777b6-f2h9f 1/1 Running 0 10s
gowebhost-5d6cf777b6-trdt6 1/1 Running 0 10s
gowebip-f647fbd59-25dnc 1/1 Running 0 14s
gowebip-f647fbd59-4xp9r 1/1 Running 0 14s3. 部署ingress的pods
apiVersion: networking.k8s.io/v1 # kubectl explain ingress.apiVersion
kind: Ingress
metadata:
name: ingress-test
namespace: default
annotations:
#kubernetes.io/ingress.class: "nginx"
# 开启use-regex,启用path的正则匹配
nginx.ingress.kubernetes.io/use-regex: "true"
spec:
ingressClassName: nginx
rules:
# 定义域名
- host: test.ingress.com
http:
paths:
# 不同path转发到不同端口
- path: /ip
pathType: Prefix
backend:
service:
name: gowebip
port:
number: 8888
- path: /host
pathType: Prefix
backend:
service:
name: gowebhost
port:
number: 9999[root@k8s-master-01 test2]# kubectl get ingress
No resources found in default namespace.
[root@k8s-master-01 test2]# kubectl apply -f ingress-test1.yaml
ingress.networking.k8s.io/ingress-test created
[root@k8s-master-01 test2]# kubectl get ingress
NAME CLASS HOSTS ADDRESS PORTS AGE
ingress-test nginx test.ingress.com 80 2s
[root@k8s-master-01 test2]# kubectl get ingress -w
NAME CLASS HOSTS ADDRESS PORTS AGE
ingress-test nginx test.ingress.com 80 6s
^C[root@k8s-master-01 test2]# ^C
[root@k8s-master-01 test2]# kubectl get ingress
NAME CLASS HOSTS ADDRESS PORTS AGE
ingress-test nginx test.ingress.com 80 44s
[root@k8s-master-01 test2]# kubectl get ingress -w
NAME CLASS HOSTS ADDRESS PORTS AGE
ingress-test nginx test.ingress.com 80 46s
ingress-test nginx test.ingress.com 192.168.110.213 80 47s4. 查看
[root@k8s-master-01 test2]# curl 10.244.2.144
<!DOCTYPE html>
<html>
<head>
<title>Welcome to nginx!</title>
<style>
body {
width: 35em;
margin: 0 auto;
font-family: Tahoma, Verdana, Arial, sans-serif;
}
</style>
</head>
<body>
<h1>Welcome to nginx!</h1>
<p>If you see this page, the nginx web server is successfully installed and
working. Further configuration is required.</p>
<p>For online documentation and support please refer to
<a href="http://nginx.org/">nginx.org</a>.<br/>
Commercial support is available at
<a href="http://nginx.com/">nginx.com</a>.</p>
<p><em>Thank you for using nginx.</em></p>
</body>
</html>
[root@k8s-master-01 test2]# kubectl -n ingress-nginx get svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
ingress-nginx-controller NodePort 10.111.188.71 <none> 80:32593/TCP,443:32318/TCP 118m
ingress-nginx-controller-admission ClusterIP 10.108.110.90 <none> 443/TCP 118m
[root@k8s-master-01 test2]# ipvsadm -Ln
IP Virtual Server version 1.2.1 (size=4096)
Prot LocalAddress:Port Scheduler Flags
-> RemoteAddress:Port Forward Weight ActiveConn InActConn
TCP 192.168.110.97:32318 rr
-> 10.244.1.188:443 Masq 1 0 0
TCP 192.168.110.97:32593 rr
-> 10.244.1.188:80 Masq 1 0 1
TCP 10.96.0.1:443 rr
-> 192.168.110.97:6443 Masq 1 2 0
TCP 10.96.0.10:53 rr
-> 10.244.0.28:53 Masq 1 0 0
-> 10.244.1.171:53 Masq 1 0 0
TCP 10.96.0.10:9153 rr
-> 10.244.0.28:9153 Masq 1 0 0
-> 10.244.1.171:9153 Masq 1 0 0
TCP 10.98.113.34:443 rr
-> 10.244.2.132:10250 Masq 1 0 0
TCP 10.108.110.90:443 rr
-> 10.244.1.188:8443 Masq 1 0 0
TCP 10.110.213.242:9999 rr
-> 10.244.1.190:80 Masq 1 0 0
-> 10.244.2.144:80 Masq 1 0 0
TCP 10.110.238.126:8888 rr
-> 10.244.1.189:80 Masq 1 0 0
-> 10.244.2.143:80 Masq 1 0 0
TCP 10.111.188.71:80 rr
-> 10.244.1.188:80 Masq 1 0 0
TCP 10.111.188.71:443 rr
-> 10.244.1.188:443 Masq 1 0 0
TCP 10.244.0.0:32318 rr
-> 10.244.1.188:443 Masq 1 0 0
TCP 10.244.0.0:32593 rr
-> 10.244.1.188:80 Masq 1 0 0
TCP 10.244.0.1:32318 rr
-> 10.244.1.188:443 Masq 1 0 0
TCP 10.244.0.1:32593 rr
-> 10.244.1.188:80 Masq 1 0 0
UDP 10.96.0.10:53 rr
-> 10.244.0.28:53 Masq 1 0 0
-> 10.244.1.171:53 Masq 1 0 0
[root@k8s-master-01 test2]#
[root@k8s-master-01 test2]#
[root@k8s-master-01 test2]# kubectl -n ingress-nginx get pods -o wide(这里只有一个pod可以修改yaml文件扩成3个)
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
ingress-nginx-admission-create-2pz6l 0/1 Completed 0 126m 10.244.1.187 k8s-node-01 <none> <none>
ingress-nginx-admission-patch-m7zkg 0/1 Completed 0 126m 10.244.2.142 k8s-node-02 <none> <none>
ingress-nginx-controller-8698cc7676-2lth6 1/1 Running 0 126m 10.244.1.188 k8s-node-01 <none> 5. 给微服务里面添加内容然后curl测试
[root@k8s-master-01 test2]kubectl exec -it gowebip-f647fbd59-4xp9r -- /bin/sh -c "mkdir -p /usr/share/nginx/html/ip && echo 111112222 > /usr/share/nginx/html/ip/test.html"
[root@k8s-master-01 test2]kubectl exec -it gowebip-f647fbd59-25dnc -- /bin/sh -c "mkdir -p /usr/share/nginx/html/ip && echo 11111 > /usr/share/nginx/html/ip/test.html"
[root@k8s-master-01 test2]curl 10.244.2.143/ip/test.html
111116. 在集群外部访问
host文件改好 win路径 C:\Windows\System32\drivers\etc
192.168.110.97 test.ingress.com
C:\Users\MIKU>curl http://test.ingress.com:32593/ip/test.html
11111
C:\Users\MIKU>curl http://test.ingress.com:32593/ip/test.html
11111
C:\Users\MIKU>curl http://test.ingress.com:32593/ip/test.html
111112222222
C:\Users\MIKU>curl http://test.ingress.com:32593/ip/test.html
111112222222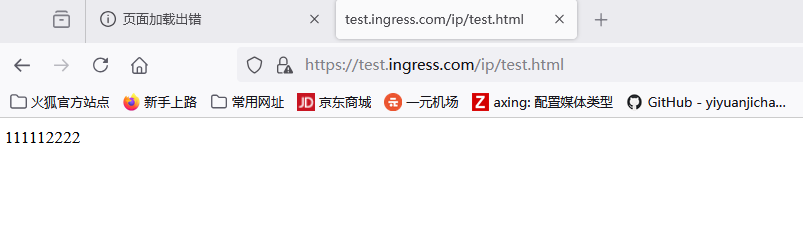
7. 不需要创建(用hostNetwork网络模式)转发路径更短,效率更高
Daemonset来部署ingress的pod(pod的网络就是hostNetwork)
如果是上面那个实验做过的,这里要先把之前的deploy.yaml文件删了
kubectl delete -f deploy.yamlapiVersion: v1
kind: Namespace
metadata:
labels:
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
name: ingress-nginx
---
apiVersion: v1
automountServiceAccountToken: true
kind: ServiceAccount
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx
namespace: ingress-nginx
---
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx-admission
namespace: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx
namespace: ingress-nginx
rules:
- apiGroups:
- ""
resources:
- namespaces
verbs:
- get
- apiGroups:
- ""
resources:
- configmaps
- pods
- secrets
- endpoints
verbs:
- get
- list
- watch
- apiGroups:
- ""
resources:
- services
verbs:
- get
- list
- watch
- apiGroups:
- networking.k8s.io
resources:
- ingresses
verbs:
- get
- list
- watch
- apiGroups:
- networking.k8s.io
resources:
- ingresses/status
verbs:
- update
- apiGroups:
- networking.k8s.io
resources:
- ingressclasses
verbs:
- get
- list
- watch
- apiGroups:
- coordination.k8s.io
resourceNames:
- ingress-nginx-leader
resources:
- leases
verbs:
- get
- update
- apiGroups:
- coordination.k8s.io
resources:
- leases
verbs:
- create
- apiGroups:
- ""
resources:
- events
verbs:
- create
- patch
- apiGroups:
- discovery.k8s.io
resources:
- endpointslices
verbs:
- list
- watch
- get
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx-admission
namespace: ingress-nginx
rules:
- apiGroups:
- ""
resources:
- secrets
verbs:
- get
- create
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
labels:
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx
rules:
- apiGroups:
- ""
resources:
- configmaps
- endpoints
- nodes
- pods
- secrets
- namespaces
verbs:
- list
- watch
- apiGroups:
- coordination.k8s.io
resources:
- leases
verbs:
- list
- watch
- apiGroups:
- ""
resources:
- nodes
verbs:
- get
- apiGroups:
- ""
resources:
- services
verbs:
- get
- list
- watch
- apiGroups:
- networking.k8s.io
resources:
- ingresses
verbs:
- get
- list
- watch
- apiGroups:
- ""
resources:
- events
verbs:
- create
- patch
- apiGroups:
- networking.k8s.io
resources:
- ingresses/status
verbs:
- update
- apiGroups:
- networking.k8s.io
resources:
- ingressclasses
verbs:
- get
- list
- watch
- apiGroups:
- discovery.k8s.io
resources:
- endpointslices
verbs:
- list
- watch
- get
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx-admission
rules:
- apiGroups:
- admissionregistration.k8s.io
resources:
- validatingwebhookconfigurations
verbs:
- get
- update
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx
namespace: ingress-nginx
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: ingress-nginx
subjects:
- kind: ServiceAccount
name: ingress-nginx
namespace: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx-admission
namespace: ingress-nginx
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: ingress-nginx-admission
subjects:
- kind: ServiceAccount
name: ingress-nginx-admission
namespace: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
labels:
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: ingress-nginx
subjects:
- kind: ServiceAccount
name: ingress-nginx
namespace: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx-admission
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: ingress-nginx-admission
subjects:
- kind: ServiceAccount
name: ingress-nginx-admission
namespace: ingress-nginx
---
apiVersion: v1
data:
allow-snippet-annotations: "false"
kind: ConfigMap
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx-controller
namespace: ingress-nginx
---
apiVersion: v1
kind: Service
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx-controller-admission
namespace: ingress-nginx
spec:
ports:
- appProtocol: https
name: https-webhook
port: 443
targetPort: webhook
selector:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
type: ClusterIP
---
apiVersion: apps/v1
kind: DaemonSet
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx-controller
namespace: ingress-nginx
spec:
minReadySeconds: 0
revisionHistoryLimit: 10
selector:
matchLabels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
template:
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
spec:
hostNetwork: true
containers:
- args:
- /nginx-ingress-controller
- --election-id=ingress-nginx-leader
- --controller-class=k8s.io/ingress-nginx
- --ingress-class=nginx
- --configmap=$(POD_NAMESPACE)/ingress-nginx-controller
- --validating-webhook=:8443
- --validating-webhook-certificate=/usr/local/certificates/cert
- --validating-webhook-key=/usr/local/certificates/key
- --enable-metrics=false
env:
- name: POD_NAME
valueFrom:
fieldRef:
fieldPath: metadata.name
- name: POD_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
- name: LD_PRELOAD
value: /usr/local/lib/libmimalloc.so
image: registry.cn-qingdao.aliyuncs.com/egon-k8s-test/ingress-controller:v1.10.1
imagePullPolicy: IfNotPresent
lifecycle:
preStop:
exec:
command:
- /wait-shutdown
livenessProbe:
failureThreshold: 5
httpGet:
path: /healthz
port: 10254
scheme: HTTP
initialDelaySeconds: 10
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 1
name: controller
ports:
- containerPort: 80
name: http
protocol: TCP
- containerPort: 443
name: https
protocol: TCP
- containerPort: 8443
name: webhook
protocol: TCP
readinessProbe:
failureThreshold: 3
httpGet:
path: /healthz
port: 10254
scheme: HTTP
initialDelaySeconds: 10
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 1
resources:
requests:
cpu: 100m
memory: 90Mi
securityContext:
allowPrivilegeEscalation: false
capabilities:
add:
- NET_BIND_SERVICE
drop:
- ALL
readOnlyRootFilesystem: false
runAsNonRoot: true
runAsUser: 101
seccompProfile:
type: RuntimeDefault
volumeMounts:
- mountPath: /usr/local/certificates/
name: webhook-cert
readOnly: true
dnsPolicy: ClusterFirst
nodeSelector:
kubernetes.io/os: linux
serviceAccountName: ingress-nginx
terminationGracePeriodSeconds: 300
volumes:
- name: webhook-cert
secret:
secretName: ingress-nginx-admission
---
apiVersion: batch/v1
kind: Job
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx-admission-create
namespace: ingress-nginx
spec:
template:
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx-admission-create
spec:
containers:
- args:
- create
- --host=ingress-nginx-controller-admission,ingress-nginx-controller-admission.$(POD_NAMESPACE).svc
- --namespace=$(POD_NAMESPACE)
- --secret-name=ingress-nginx-admission
env:
- name: POD_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
image: registry.cn-qingdao.aliyuncs.com/egon-k8s-test/kube-webhook-certgen:v1.4.1
imagePullPolicy: IfNotPresent
name: create
securityContext:
allowPrivilegeEscalation: false
capabilities:
drop:
- ALL
readOnlyRootFilesystem: true
runAsNonRoot: true
runAsUser: 65532
seccompProfile:
type: RuntimeDefault
nodeSelector:
kubernetes.io/os: linux
restartPolicy: OnFailure
serviceAccountName: ingress-nginx-admission
---
apiVersion: batch/v1
kind: Job
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx-admission-patch
namespace: ingress-nginx
spec:
template:
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx-admission-patch
spec:
containers:
- args:
- patch
- --webhook-name=ingress-nginx-admission
- --namespace=$(POD_NAMESPACE)
- --patch-mutating=false
- --secret-name=ingress-nginx-admission
- --patch-failure-policy=Fail
env:
- name: POD_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
image: registry.cn-qingdao.aliyuncs.com/egon-k8s-test/kube-webhook-certgen:v1.4.1
imagePullPolicy: IfNotPresent
name: patch
securityContext:
allowPrivilegeEscalation: false
capabilities:
drop:
- ALL
readOnlyRootFilesystem: true
runAsNonRoot: true
runAsUser: 65532
seccompProfile:
type: RuntimeDefault
nodeSelector:
kubernetes.io/os: linux
restartPolicy: OnFailure
serviceAccountName: ingress-nginx-admission
---
apiVersion: networking.k8s.io/v1
kind: IngressClass
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: nginx
spec:
controller: k8s.io/ingress-nginx
---
apiVersion: admissionregistration.k8s.io/v1
kind: ValidatingWebhookConfiguration
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.10.1
name: ingress-nginx-admission
webhooks:
- admissionReviewVersions:
- v1
clientConfig:
service:
name: ingress-nginx-controller-admission
namespace: ingress-nginx
path: /networking/v1/ingresses
failurePolicy: Fail
matchPolicy: Equivalent
name: validate.nginx.ingress.kubernetes.io
rules:
- apiGroups:
- networking.k8s.io
apiVersions:
- v1
operations:
- CREATE
- UPDATE
resources:
- ingresses
sideEffects: None
kubectl apply -f daemonset.yaml部署ingress的规则可以ssl连接
cat ingress-test1-ssl.yamlapiVersion: networking.k8s.io/v1 # kubectl explain ingress.apiVersion
kind: Ingress
metadata:
name: ingress-test
namespace: default
annotations:
#kubernetes.io/ingress.class: "nginx"
# 开启use-regex,启用path的正则匹配
nginx.ingress.kubernetes.io/use-regex: "true"
spec:
tls:
- hosts:
- test.ingress.com
secretName: ingress-tls
ingressClassName: nginx
rules:
# 定义域名
- host: test.ingress.com
http:
paths:
# 不同path转发到不同端口
- path: /ip
pathType: Prefix
backend:
service:
name: gowebip
port:
number: 8888
- path: /host
pathType: Prefix
backend:
service:
name: gowebhost
port:
number: 9999#可以把之前残留的给删了
kubectl delete -f ingress-test.yaml8. 查看端口
[root@k8s-master-01 test2]# netstat -an |grep 80
tcp 0 0 192.168.110.97:2380 0.0.0.0:* LISTEN
tcp 0 0 10.244.0.1:48756 10.244.0.29:8080 TIME_WAIT
tcp 0 0 127.0.0.1:36480 127.0.0.1:2379 ESTABLISHED
tcp 0 0 127.0.0.1:2379 127.0.0.1:36380 ESTABLISHED
tcp 0 0 127.0.0.1:2379 127.0.0.1:36480 ESTABLISHED
tcp 0 0 127.0.0.1:36380 127.0.0.1:2379 ESTABLISHED
tcp 0 0 10.244.0.1:50044 10.244.0.29:8080 TIME_WAIT
unix 2 [ ACC ] STREAM LISTENING 24356 /run/containerd/s/c259f4f33d1f76cfc9d27ea0ff86080e5d837adbeb3f2836dd63df79a862f5c3
unix 2 [ ACC ] STREAM LISTENING 24360 /run/containerd/s/0f8e770aec32fad8b31af9ccee9b8e7875778093b9418014071d704e81f5e24f
unix 3 [ ] STREAM CONNECTED 25883 /run/containerd/s/c259f4f33d1f76cfc9d27ea0ff86080e5d837adbeb3f2836dd63df79a862f5c3
unix 3 [ ] STREAM CONNECTED 25865 /run/containerd/s/0f8e770aec32fad8b31af9ccee9b8e7875778093b9418014071d704e81f5e24f
unix 3 [ ] STREAM CONNECTED 28039 /run/containerd/containerd.sock.ttrpc
unix 3 [ ] STREAM CONNECTED 24802
unix 3 [ ] STREAM CONNECTED 28038
unix 3 [ ] STREAM CONNECTED 28032
unix 3 [ ] STREAM CONNECTED 23411 /run/containerd/s/0f8e770aec32fad8b31af9ccee9b8e7875778093b9418014071d704e81f5e24f
unix 3 [ ] STREAM CONNECTED 23407 /run/containerd/s/c259f4f33d1f76cfc9d27ea0ff86080e5d837adbeb3f2836dd63df79a862f5c3
unix 3 [ ] STREAM CONNECTED 22680 /run/systemd/journal/stdout
unix 3 [ ] STREAM CONNECTED 28064 /run/containerd/s/f7d5f17994654e129e8b4fee26256945ccd2a09eb22254e4cdd5bcea83781192
unix 3 [ ] STREAM CONNECTED 25809
[root@k8s-master-01 test2]# kubectl -n ingress-nginx get pods -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
ingress-nginx-controller-78pdk 0/1 Terminating 0 5m9s 192.168.110.97 k8s-master-01 <none> <none>
[root@k8s-master-01 test2]# kubectl -n ingress-nginx get pods -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
ingress-nginx-admission-create-ttrj5 0/1 Completed 0 9s 10.244.1.199 k8s-node-01 <none> <none>
ingress-nginx-admission-patch-bgrp8 0/1 Completed 1 9s 10.244.1.200 k8s-node-01 <none> <none>
ingress-nginx-controller-2h2dt 0/1 Running 0 9s 192.168.110.2 k8s-node-02 <none> <none>
ingress-nginx-controller-cjwtb 0/1 Running 0 9s 192.168.110.213 k8s-node-01 <none> <none>
ingress-nginx-controller-jxwkf 0/1 Running 0 9s 192.168.110.97 k8s-master-01 <none> <none>
[root@k8s-master-01 test2]# kubectl -n ingress-nginx get pods -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
ingress-nginx-admission-create-ttrj5 0/1 Completed 0 46m 10.244.1.199 k8s-node-01 <none> <none>
ingress-nginx-admission-patch-bgrp8 0/1 Completed 1 46m 10.244.1.200 k8s-node-01 <none> <none>
ingress-nginx-controller-2h2dt 1/1 Running 0 46m 192.168.110.2 k8s-node-02 <none> <none>
ingress-nginx-controller-cjwtb 1/1 Running 0 46m 192.168.110.213 k8s-node-01 <none> <none>
ingress-nginx-controller-jxwkf 1/1 Running 0 46m 192.168.110.97 k8s-master-01 <none> <none>
9. 生成证书
openssl genrsa -out tls.key 2048
openssl req -x509 -key tls.key -out tls.crt -subj "/C=CN/ST=ShangHai/L=ShangHai/O=Ingress/CN=test.ingress.com"
kubectl -n default create secret tls ingress-tls --cert=tls.crt --key=tls.key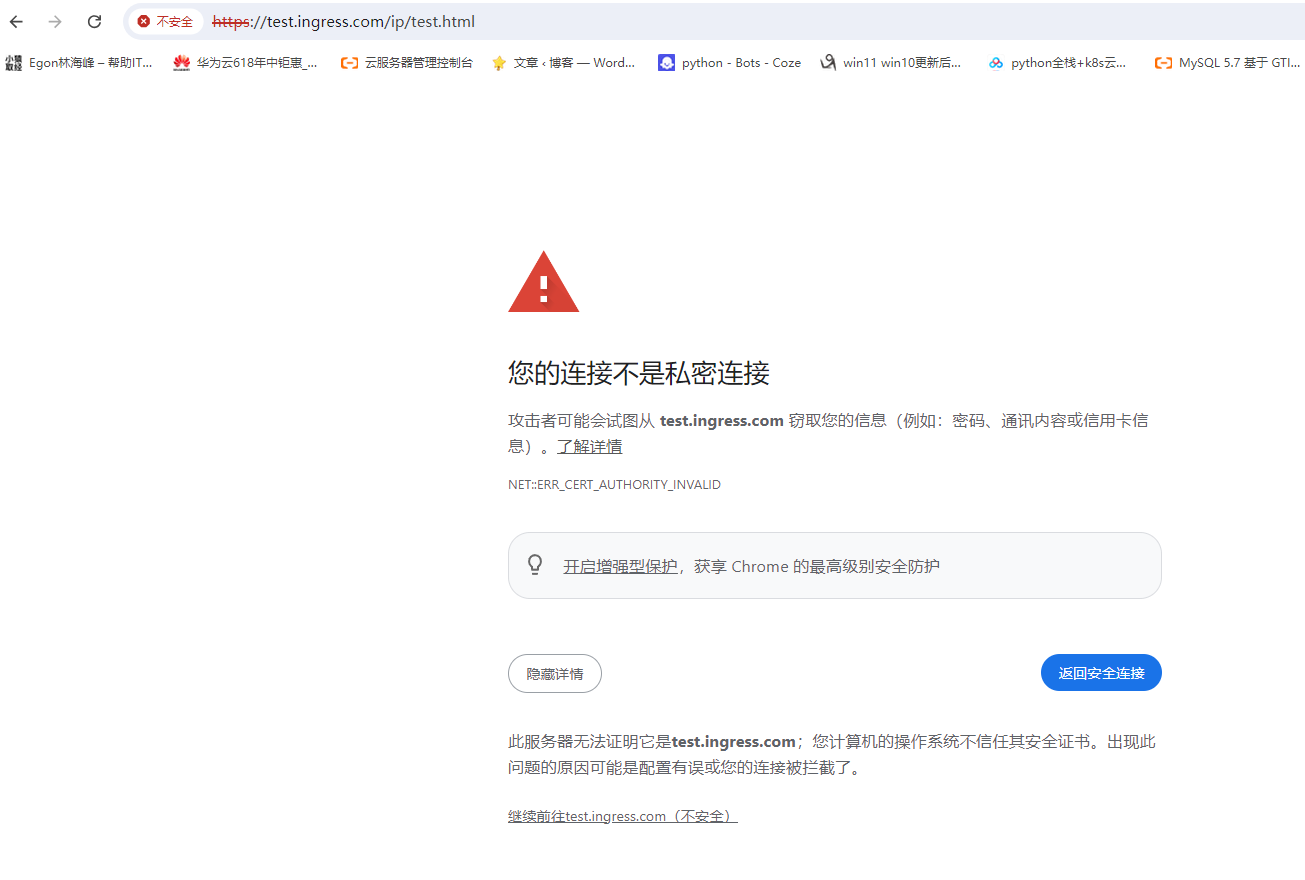
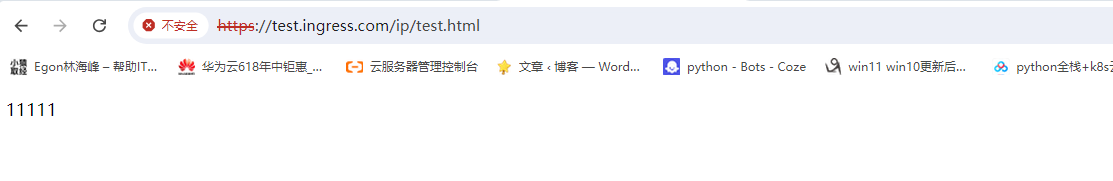
10. 一些查询
[root@k8s-master-01 test2]kubectl get svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
gowebhost ClusterIP 10.99.181.85 <none> 9999/TCP 5m12s
gowebip ClusterIP 10.100.100.184 <none> 8888/TCP 4m59s
kubernetes ClusterIP 10.96.0.1 <none> 443/TCP 16d
my-service ExternalName <none> www.baidu.com <none> 19h
mysql-k8s ClusterIP None <none> 13306/TCP 19h
[root@k8s-master-01 test2]kubectl get ingress
NAME CLASS HOSTS ADDRESS PORTS AGE
ingress-test nginx test.ingress.com 80 5m21s
kubectl get secrets #查看证书
kubectl get deployments
kubectl delete deployment <deployment-name>
kubectl delete service <service-name>
[root@k8s-master-01 test2]kubectl get svc -n ingress-nginx
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
ingress-nginx-controller NodePort 10.100.138.120 <none> 80:31220/TCP,443:30969/TCP 34m
ingress-nginx-controller-admission ClusterIP 10.97.181.161 <none> 443/TCP 34m
删除限制
[root@k8s-master-01 test2]kubectl describe node k8s-master-01 | grep Taints
Taints: node-role.kubernetes.io/control-plane:NoSchedule
[root@k8s-master-01 test2]kubectl describe node k8s-master-01 | grep Taints
Taints: <none>


评论 (0)