搜索到
17
篇与
的结果
-
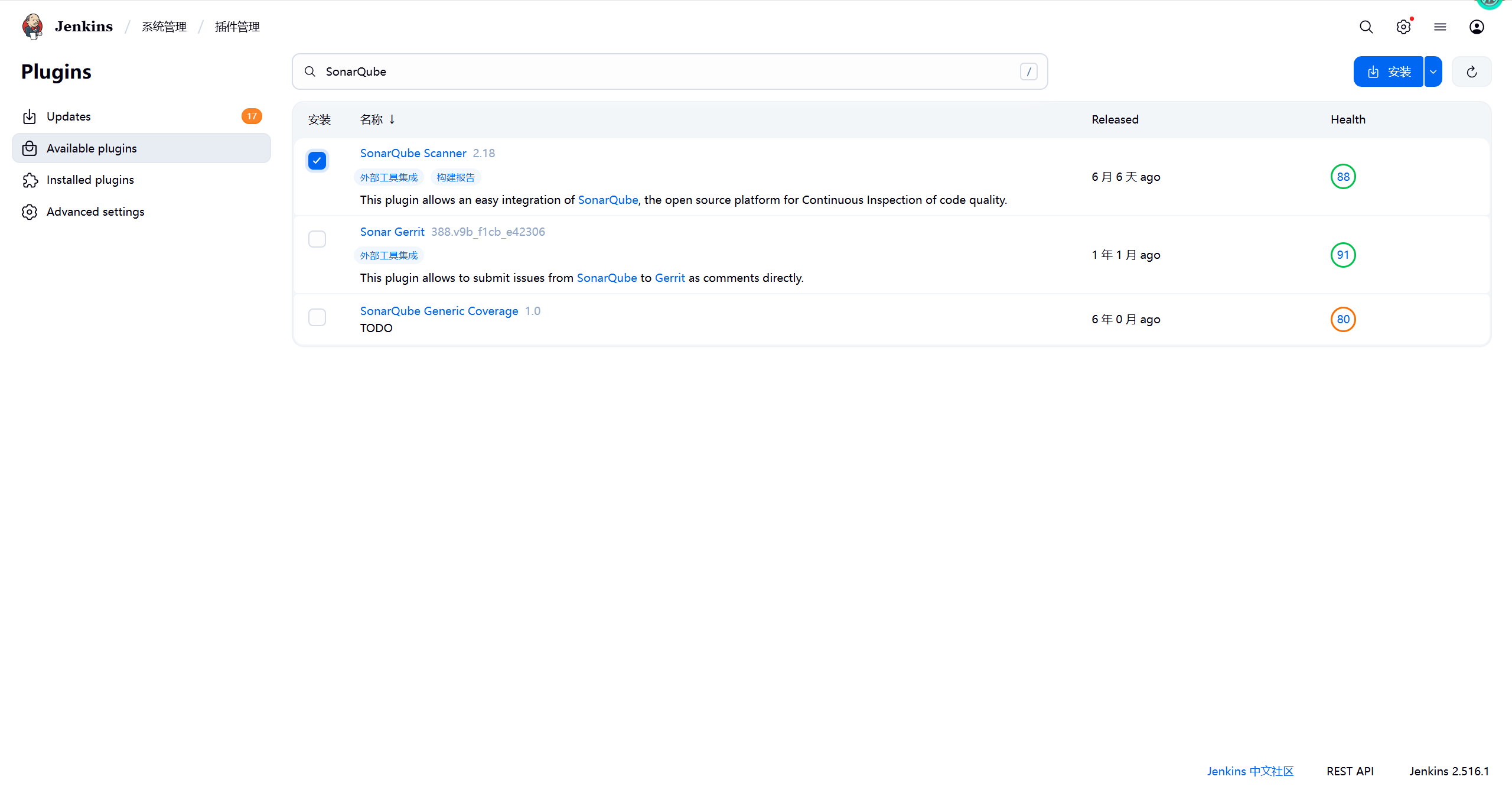
 jenkins与SonarQube连接 一、jenkins安装插件 1.1下载SonarQube插件进入Jenkins的系统管理->插件管理->可选插件,搜索框输入sonarqube,安装重启。1.2启用SonarQubeJenkins的系统管理->系统配置,添加SonarQube服务。二、SonarQube配置 2.1禁用审查结果上传到SCM功能2.2生成token添加jenkin用户 token:squ_4bc173eb520dd35c176104baa1b899a992e88c88三、jenkins配置 3.1添加令牌Jenkins的系统管理->系统配置->添加token类型切换成Secret text,粘贴token,点击添加。选上刚刚添加的令牌凭证,点击应用保存。3.2SonarQube Scanner 安装进入Jenkins的系统管理->全局工具配置,下滑找到图片里的地方,点击新增SonarQube Scanner,我们选择自动安装并选择最新的版本。四、非流水线项目添加代码审查 4.1添加构建步骤编辑之前的自由风格构建的demo项目,在构建阶段新增步骤。analysis properties参数如下# 项目名称id,全局唯一 sonar.projectKey=sprint_boot_demo # 项目名称 sonar.projectName=sprint_boot_demo sonar.projectVersion=1.0 # 扫描路径,当前项目根目录 sonar.sources=./src # 排除目录 sonar.exclusions=**/test/**,**/target/** # jdk版本 sonar.java.source=1.17 sonar.java.target=1.17 # 字符编码 sonar.sourceEncoding=UTF-8 # binaries路径 sonar.java.binaries=target/classes4.2构建并查看结果jenkins点击立即构建,查看构建结果查看SonarQube扫描结果五、流水线项目添加代码审查 5.1创建sonar-project.properties文件项目根目录下,创建sonar-project.properties文件,内容如下# 项目名称id,全局唯一 sonar.projectKey=sprint_boot_demo # 项目名称 sonar.projectName=sprint_boot_demo sonar.projectVersion=1.0 # 扫描路径,当前项目根目录 sonar.sources=./src # 排除目录 sonar.exclusions=**/test/**,**/target/** # jdk版本 sonar.java.source=1.17 sonar.java.target=1.17 # 字符编码 sonar.sourceEncoding=UTF-8 # binaries路径 sonar.java.binaries=target/classes5.2修改Jenkinsfile加入SonarQube代码审查阶段pipeline { agent any stages { stage('拉取代码') { steps { echo '开始拉取代码' checkout([$class: 'GitSCM', branches: [[name: '*/master']], userRemoteConfigs: [[url: 'https://gitee.com/axzys/sprint_boot_demo.git']]]) echo '拉取代码完成' } } stage('打包编译') { steps { echo '开始打包编译' sh 'mvn clean package' echo '打包编译完成' } } stage('代码审查') { steps { echo '开始代码审查' script { // 引入SonarQube scanner,名称与jenkins 全局工具SonarQube Scanner的name保持一致 def scannerHome = tool 'SonarQube' // 引入SonarQube Server,名称与jenkins 系统配置SonarQube servers的name保持一致 withSonarQubeEnv('SonarQube') { sh "${scannerHome}/bin/sonar-scanner" } } echo '代码审查完成' } } stage('部署项目') { steps { echo '开始部署项目' echo '部署项目完成' } } } } 5.3构建测试
jenkins与SonarQube连接 一、jenkins安装插件 1.1下载SonarQube插件进入Jenkins的系统管理->插件管理->可选插件,搜索框输入sonarqube,安装重启。1.2启用SonarQubeJenkins的系统管理->系统配置,添加SonarQube服务。二、SonarQube配置 2.1禁用审查结果上传到SCM功能2.2生成token添加jenkin用户 token:squ_4bc173eb520dd35c176104baa1b899a992e88c88三、jenkins配置 3.1添加令牌Jenkins的系统管理->系统配置->添加token类型切换成Secret text,粘贴token,点击添加。选上刚刚添加的令牌凭证,点击应用保存。3.2SonarQube Scanner 安装进入Jenkins的系统管理->全局工具配置,下滑找到图片里的地方,点击新增SonarQube Scanner,我们选择自动安装并选择最新的版本。四、非流水线项目添加代码审查 4.1添加构建步骤编辑之前的自由风格构建的demo项目,在构建阶段新增步骤。analysis properties参数如下# 项目名称id,全局唯一 sonar.projectKey=sprint_boot_demo # 项目名称 sonar.projectName=sprint_boot_demo sonar.projectVersion=1.0 # 扫描路径,当前项目根目录 sonar.sources=./src # 排除目录 sonar.exclusions=**/test/**,**/target/** # jdk版本 sonar.java.source=1.17 sonar.java.target=1.17 # 字符编码 sonar.sourceEncoding=UTF-8 # binaries路径 sonar.java.binaries=target/classes4.2构建并查看结果jenkins点击立即构建,查看构建结果查看SonarQube扫描结果五、流水线项目添加代码审查 5.1创建sonar-project.properties文件项目根目录下,创建sonar-project.properties文件,内容如下# 项目名称id,全局唯一 sonar.projectKey=sprint_boot_demo # 项目名称 sonar.projectName=sprint_boot_demo sonar.projectVersion=1.0 # 扫描路径,当前项目根目录 sonar.sources=./src # 排除目录 sonar.exclusions=**/test/**,**/target/** # jdk版本 sonar.java.source=1.17 sonar.java.target=1.17 # 字符编码 sonar.sourceEncoding=UTF-8 # binaries路径 sonar.java.binaries=target/classes5.2修改Jenkinsfile加入SonarQube代码审查阶段pipeline { agent any stages { stage('拉取代码') { steps { echo '开始拉取代码' checkout([$class: 'GitSCM', branches: [[name: '*/master']], userRemoteConfigs: [[url: 'https://gitee.com/axzys/sprint_boot_demo.git']]]) echo '拉取代码完成' } } stage('打包编译') { steps { echo '开始打包编译' sh 'mvn clean package' echo '打包编译完成' } } stage('代码审查') { steps { echo '开始代码审查' script { // 引入SonarQube scanner,名称与jenkins 全局工具SonarQube Scanner的name保持一致 def scannerHome = tool 'SonarQube' // 引入SonarQube Server,名称与jenkins 系统配置SonarQube servers的name保持一致 withSonarQubeEnv('SonarQube') { sh "${scannerHome}/bin/sonar-scanner" } } echo '代码审查完成' } } stage('部署项目') { steps { echo '开始部署项目' echo '部署项目完成' } } } } 5.3构建测试 -
 jenkins与k8s连接 一、安装kubernetes插件在Jenkins的插件管理中安装Kubernetes插件 jenkins——>系统管理——>插件管理——>avaliable plugins二、本集群连接 2.1创建sa账号如果jenkins在k8s集群中部署,直接创建sa账号,并进行rbac授权即可,yaml文件参考前面文章。2.2创建cloud资源然后在jenkins——>系统管理——>Clouds——>New cloud——>输入cloud name并勾选类型为kubernetesroot@k8s-01:~/jenkins# cat deployment.yaml apiVersion: apps/v1 kind: Deployment metadata: name: jenkins namespace: cicd spec: replicas: 1 selector: matchLabels: app: jenkins template: metadata: labels: app: jenkins spec: securityContext: fsGroup: 1000 # 确保 Jenkins 用户有存储写入权限 serviceAccountName: jenkins-admin automountServiceAccountToken: true # 新增节点选择器,将 Pod 固定在 k8s-03 节点 nodeSelector: kubernetes.io/hostname: k8s-03 containers: - name: jenkins image: registry.cn-guangzhou.aliyuncs.com/xingcangku/jenkins-jenkins-lts-jdk17:lts-jdk17 imagePullPolicy: IfNotPresent ports: - containerPort: 8080 - containerPort: 50000 # 新增环境变量(可选) env: - name: JAVA_HOME value: "/usr/lib/jvm/amazon-corretto-17.0.16.8.1-linux-x64" volumeMounts: - name: jenkins-data mountPath: /var/jenkins_home # ============ 新增挂载 ============ - name: host-jvm mountPath: /usr/lib/jvm - name: maven-data mountPath: /usr/local/maven resources: limits: cpu: "1" memory: "3Gi" requests: cpu: "0.5" memory: "1Gi" livenessProbe: httpGet: path: /login port: 8080 initialDelaySeconds: 90 periodSeconds: 10 volumes: - name: jenkins-data persistentVolumeClaim: claimName: jenkins-pvc # ============ 新增的卷配置 ============ - name: host-jvm hostPath: path: /usr/lib/jvm type: Directory - name: maven-data hostPath: path: /usr/local/maven type: Directoryroot@k8s-01:~/jenkins# cat new-rbac.yaml apiVersion: v1 kind: ServiceAccount metadata: name: jenkins-admin namespace: cicd --- # 创建自定义 ClusterRole apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: jenkins-clusterrole rules: - apiGroups: [""] resources: ["pods", "pods/log", "services"] verbs: ["get", "list", "watch", "create", "update", "delete"] - apiGroups: ["apps"] resources: ["deployments"] verbs: ["*"] --- # 绑定 ServiceAccount 到 ClusterRole apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: jenkins-crb roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: jenkins-clusterrole subjects: - kind: ServiceAccount name: jenkins-admin namespace: cicdk8s1.24版本以后,行为变更:从 Kubernetes v1.24 开始,不再自动为 ServiceAccount 创建 Secret(令牌不再存储在 Secret 中) TokenRequest API:现在需要使用 TokenRequest API 获取令牌 root@k8s-01:~/jenkins# cat jenkins-secret.yaml apiVersion: v1 kind: Secret metadata: name: jenkins-admin-token namespace: cicd annotations: kubernetes.io/service-account.name: jenkins-admin type: kubernetes.io/service-account-token root@k8s-01:~/jenkins# kubectl apply -n cicd -f jenkins-secret.yaml secret/jenkins-admin-token created root@k8s-01:~/jenkins# kubectl describe sa jenkins-admin -n cicd Name: jenkins-admin Namespace: cicd Labels: <none> Annotations: <none> Image pull secrets: <none> Mountable secrets: <none> Tokens: jenkins-admin-token Events: <none> root@k8s-01:~/jenkins# kubectl get secret jenkins-admin-token -n cicd -o jsonpath='{.data.token}' | base64 -d eyJhbGciOiJSUzI1NiIsImtpZCI6IjJ0MTFFdDhfdnFBYkNuTnBSSXlyOFIzN1B0MW13cVVJNlFwZDV1VzR1WXcifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJjaWNkIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImplbmtpbnMtYWRtaW4tdG9rZW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiamVua2lucy1hZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjRkY2ViZjg1LTI0NzEtNGJjYi04Yzg5LWQ0MWI0NjAzN2RkZSIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpjaWNkOmplbmtpbnMtYWRtaW4ifQ.qvBiSwdCVbfMDnP0ElhnMcn__q65HDqidWw2JDQbrn7zrgNX2jjXlDxhA8RQFQaHhrTPGrOuP60vzfz4WgvJxwJvwIHaqqAbK8r3t-eTBpXNKltY3GEFEqxyjVlTd8q0DLW0OWZHUVZJrWhYT00Xa1ZViJgwQ2X0ogpAphSlvR351ZEDmDDxwxk4WwioZpmU22_weFamlU0g9SQVW5kBYGw06Tq_dPNL7cB0CDdPy0mSYckquEtG4xh-EIddPs9cGd1_OGurjwEkwX2-HvlfCXfoFkgo42lrOCaouWE4I4e21OXUCg5erFONSWSPKhhmhiLsjikByweCE0qaA2ZIUw#还要另外创建serviceAccount root@k8s-01:~/jenkins# cat jenkins-secret.yaml rbac.yaml apiVersion: v1 kind: Secret metadata: name: jenkins-admin-token namespace: cicd annotations: kubernetes.io/service-account.name: jenkins-admin type: kubernetes.io/service-account-token # rbac.yaml apiVersion: v1 kind: ServiceAccount metadata: name: jenkins-admin namespace: cicd --- kind: ClusterRoleBinding apiVersion: rbac.authorization.k8s.io/v1 metadata: name: jenkins-admin-crb roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: edit # 授予命名空间内管理权限 subjects: - kind: ServiceAccount name: jenkins-admin namespace: cicd#Kubernetes 服务证书 key root@k8s-01:~/jenkins# kubectl get secret jenkins-admin-token -n cicd -o jsonpath='{.data.ca\.crt}' | base64 -d -----BEGIN CERTIFICATE----- MIIDBTCCAe2gAwIBAgIIUTF7Qh3Q+fowDQYJKoZIhvcNAQELBQAwFTETMBEGA1UE AxMKa3ViZXJuZXRlczAeFw0yNTA3MzAxMjU3MDdaFw0zNTA3MjgxMzAyMDdaMBUx EzARBgNVBAMTCmt1YmVybmV0ZXMwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEK AoIBAQCv6lpzywPfjhKfl0HCNA/onj3MJyWI4z1JUwDlukI2j7ygm+kM2rWLpRYY wjNrvzq7R4ZD2SfiFbN/Lo/EV0zM0MXdcsI8hkR6txlKXjRkrC5crCihd9idk2UR Ov25k7bE3JpvG/zVswNMuliHx38gNsv1tfSv75lfCKyiyO3rrnj3LR9iYFvArgzY a1F5FXNjw0HVRVIPeH060i75G3YhKDVAQoZVdMoJfW7wwZDDHnh1/GB16a9Jws+r MjIQVD0YtxhQdg7WeV2nfCs0L8yXInKXwX6MGv+/HRPw140TihZwnC9gYFPisRJ5 EtUV+uq78w3Vj7Y2ANlTTQbN/F1bAgMBAAGjWTBXMA4GA1UdDwEB/wQEAwICpDAP BgNVHRMBAf8EBTADAQH/MB0GA1UdDgQWBBSvRW0owjCv5rHXwOgsyrI2QC0CxDAV BgNVHREEDjAMggprdWJlcm5ldGVzMA0GCSqGSIb3DQEBCwUAA4IBAQBL7BDL9wKu TTZ4Lx8aGAIjuEP1slw8FnDuFY2V2M8cu2wX1tlqYKJkIbwwc/dr59j6LhLgTZaP p02lQJXNRG6vR4zydgzXgsTMDXK1ANI6+7/jYgCwixGgBs/IafISCFkm1IkQ70Cw rgibN4MvybWewmucS21F62HQzO1xvrHGL8YVxvFvaUyhL9+7VhYeIX2MF3E2jLl5 kzT74Awv0O+4zBcULKrYQqNEErf5fpRLi+y9SaKA2e85DWexkhkIb6y1lZScLjRp q1lkgXqcriE653t78WrE1dSaCJY8QI94jYr4B2u7S1sbNJ9vPCDHQfFfl0DgRI/e K8+av0Qro/aA -----END CERTIFICATE-----点击kubernetes cloud details填写cloud详细信息 - Kubernetes地址:在集群内部暴露的k8s service名称https://kubernetes.default.svc - Kubernetes命名空间:jenkins sa所属的名称空间cicd - Jenkins地址:jenkins svc的名称:8080端口http://jenkins.cicd.svc:8080 使用刚刚获取的令牌在 Jenkins 中创建凭据: 凭据类型:Secret text Secret:粘贴上面的令牌值 ID:k8s-service-account-token 配置完成后点击连接测试,显示k8s集群版本,证明配置无误。三、跨集群连接在某些情况下,jenkins部署在k8s集群外,通过二进制或者docker方式部署,如果想要连接k8s集群实现资源自动创建。或者当前jenkins部署在k8s集群A中,需要通过jenkins实现集群B资源的自动创建发布,使用此方式连接。3.1配置思路jenkins要想连接并操作k8s集群,需要配置授权,请求k8s集群的kube apiserver的请求,可以和kubectl一样利用config文件用作请求的鉴权,默认在~/.kube/config下,也可以单独严格指定权限细节,生成一个jenkins专用的config文件。 在jenkins中能够识别的证书文件为PKCS#12 certificate,因此需要先将kubeconfig文件中的证书转换生成PKCS#12格式的pfx证书文件3.2生成证书我们可以使用yq命令行工具解析yaml,并提取相关的内容,然后通过base 64解码,最后生成文件 安装yq工具,仓库地址:https://github.com/mikefarah/yq [root@k8s-master ~]# wget https://github.com/mikefarah/yq/releases/download/v4.34.1/yq_linux_amd64.tar.gz [root@k8s-master ~]# tar -zxvf yq_linux_amd64.tar.gz [root@k8s-master ~]# mv yq_linux_amd64 /usr/bin/yq [root@k8s-master ~]# yq --version yq (https://github.com/mikefarah/yq/) version v4.34.1 [root@k8s-master ~]# mkdir -p /opt/jenkins-crt/certificate-authority-data——>base 64解码——>ca.crt client-certificate-data——>base 64解码——>client.crt client-key-data——>base 64解码——>client.key[root@k8s-master ~]# yq e '.clusters[0].cluster.certificate-authority-data' /root/.kube/config | base64 -d > /opt/jenkins-crt/ca.crt [root@k8s-master ~]# yq e '.users[0].user.client-certificate-data' /root/.kube/config | base64 -d > /opt/jenkins-crt/client.crt [root@k8s-master ~]# yq e '.users[0].user.client-key-data' /root/.kube/config | base64 -d > /opt/jenkins-crt/client.key [root@k8s-master ~]# cd /opt/jenkins-crt/ [root@k8s-master jenkins-crt]# ls -la 总用量 12 drwxr-xr-x 2 root root 56 6月 10 20:54 . drwxr-xr-x. 6 root root 65 6月 10 20:37 .. -rw-r--r-- 1 root root 1099 6月 10 20:53 ca.crt -rw-r--r-- 1 root root 1147 6月 10 20:53 client.crt -rw-r--r-- 1 root root 1675 6月 10 20:54 client.key3.3转换证书通过openssl进行证书格式的转换,生成Client P12认证文件cert.pfx,输入两次密码并牢记密码。[root@k8s-master jenkins-crt]# openssl pkcs12 -export -out cert.pfx -inkey client.key -in client.crt -certfile ca.crt Enter Export Password: Verifying - Enter Export Password: [root@k8s-master jenkins-crt]# ls -la 总用量 16 drwxr-xr-x 2 root root 72 6月 10 20:55 . drwxr-xr-x. 6 root root 65 6月 10 20:37 .. -rw-r--r-- 1 root root 1099 6月 10 20:53 ca.crt -rw------- 1 root root 3221 6月 10 20:55 cert.pfx -rw-r--r-- 1 root root 1147 6月 10 20:53 client.crt -rw-r--r-- 1 root root 1675 6月 10 20:54 client.key3.4导入证书打开jenkins的web界面,系统管理——>Credentials——>添加全局凭据 凭据的类型选择Certificate,证书上传刚才生成的cert.pfx证书文件,输入通过openssl生成证书文件时输入的密码3.5配置远程k8s集群地址jenkins——>系统管理——>Clouds——>New cloud——>输入cloud name并勾选类型为kubernetes 填写cloud详细信息 - Kubernetes地址:/root/.kube/config文件中cluster部分中server的内容 - Kubernetes命名空间:/root/.kube/config文件中cluster部分中name的内容 - Jenkins地址:jenkins服务的地址 - kubernetes服务证书key:ca.crt内容 - 凭据:选择刚刚创建的Certificate凭据配置完成后点击连接测试,显示k8s集群版本,证明配置无误。四、动态slave介绍 4.1为什么需要动态slave目前大多公司都采用 Jenkins 集群来搭建符合需求的 CI/CD 流程,然而传统的 Jenkins Slave 一主多从方式会存在一些痛点,比如: - 主 Master 发生单点故障时,整个流程都不可用了 - 每个 Slave 的配置环境不一样,来完成不同语言的编译打包等操作,但是这些差异化的配置导致管理起来非常不方便,维护起来也是比较费劲 - 资源分配不均衡,有的 Slave 要运行的 job 出现排队等待,而有的 Slave 处于空闲状态 - 资源有浪费,每台 Slave 可能是物理机或者虚拟机,当 Slave 处于空闲状态时,也不会完全释放掉资源。 正因为上面的这些种种痛点,我们渴望一种更高效更可靠的方式来完成这个 CI/CD 流程,而 Docker虚拟化容器技术能很好的解决这个痛点,又特别是在 Kubernetes 集群环境下面能够更好来解决上面的问题,下图是基于 Kubernetes 搭建 Jenkins 集群的简单示意图:从图上可以看到 Jenkins Master 和 Jenkins Slave 以 Pod 形式运行在 Kubernetes 集群的 Node 上,Master 运行在其中一个节点,并且将其配置数据存储到一个 Volume 上去,Slave 运行在各个节点上,并且它不是一直处于运行状态,它会按照需求动态的创建并自动删除。 这种方式的工作流程大致为:当 Jenkins Master 接受到 Build 请求时,会根据配置的 Label 动态创建一个运行在 Pod 中的 Jenkins Slave 并注册到 Master 上,当运行完 Job 后,这个 Slave 会被注销并且这个 Pod 也会自动删除,恢复到最初状态。4.2Jenkins Slave好处- 服务高可用,当 Jenkins Master 出现故障时,Kubernetes 会自动创建一个新的 Jenkins Master 容器,并且将 Volume 分配给新创建的容器,保证数据不丢失,从而达到集群服务高可用(这是k8s带来的资源控制器带来的优势) - 动态伸缩,合理使用资源,每次运行 Job 时,会自动创建一个 Jenkins Slave,Job 完成后,Slave 自动注销并删除容器,资源自动释放,而且 Kubernetes 会根据每个资源的使用情况,动态分配 Slave 到空闲的节点上创建,降低出现因某节点资源利用率高,还排队等待在该节点的情况。 - 扩展性好,当 Kubernetes 集群的资源严重不足而导致 Job 排队等待时,可以很容易的添加一个 Kubernetes Node 到集群中,从而实现扩展。五、动态slave配置 5.1制作slave镜像slave镜像应该包含以下功能: - 运行jenkins-agent服务 - 使用kubectl命令操作k8s集群 - 使用nerdctl工具管理container镜像 - 使用buildctl构建container镜像。#获取文件 root@k8s-01:~/jenkins/work# cp /usr/bin/kubectl . root@k8s-01:~/jenkins/work# cp /usr/bin/nerdctl . root@k8s-01:~/jenkins/work# cp /usr/local/bin/buildctl . root@k8s-01:~/jenkins/work# ls buildctl Dockerfile kubectl nerdctl#构建镜像 #在构建镜像过程中基于inbound-agent镜像,因为其中已经包含了jenkins-agent服务相关组件,再添加kubectl工具用于操作k8s,nerdctl和buildctl工具用于构建和管理container镜像。 root@k8s-01:~/jenkins/work# cat Dockerfile FROM jenkins/inbound-agent:latest-jdk17 USER root COPY kubectl /usr/bin/kubectl COPY nerdctl /usr/bin/nerdctl COPY buildctl /usr/bin/buildctl root@k8s-01:~/jenkins/work# docker build -t jenkins-agent:v1 . [+] Building 714.4s (9/9) FINISHED docker:default => [internal] load build definition from Dockerfile 0.0s => => transferring dockerfile: 181B 0.0s => [internal] load metadata for docker.io/jenkins/inbound-agent:latest-jdk17 4.1s => [internal] load .dockerignore 0.0s => => transferring context: 2B 0.0s => [1/4] FROM docker.io/jenkins/inbound-agent:latest-jdk17@sha256:591ba0391e1dc47af64432198be00a9e457c74d215970c4f1af592a21 709.8s => => resolve docker.io/jenkins/inbound-agent:latest-jdk17@sha256:591ba0391e1dc47af64432198be00a9e457c74d215970c4f1af592a210a 0.0s => => sha256:a90156da31f7db1823e946282d3743d1f917b9622d122a1d45818ef43c6f5dc9 8.35kB / 8.35kB 0.0s => => sha256:59e22667830bf04fb35e15ed9c70023e9d121719bb87f0db7f3159ee7c7e0b8d 28.23MB / 28.23MB 327.6s => => sha256:9ac051fdbd99f7d8c9e496724860b8ae3373f24d6f8a54f1d9096526df425d3c 43.12MB / 43.12MB 581.2s => => sha256:85a4e35755fb1aa44b91602297dc8d9f10eb8ad3f32baab32094cebc0eda41a4 3.32kB / 3.32kB 0.8s => => sha256:591ba0391e1dc47af64432198be00a9e457c74d215970c4f1af592a210a6c37b 3.14kB / 3.14kB 0.0s => => sha256:7eddb97bde91ed86d7e82e7fa5f23370b33e87882aafdbcfb2782fdec95f6231 2.19kB / 2.19kB 0.0s => => sha256:cef14de45bb7cc343e593f80531764848fe724db9084ae4a3cabacc7a7e24083 1.24MB / 1.24MB 14.3s => => sha256:28f95146d6851ca39a2ce18612cb5e5b19845ef85e4bb95bfa3095193fdf5777 1.24MB / 1.24MB 28.5s => => sha256:68a03bb16ee6a2c356d2e354bab5ec566dd7ef1e4e6daee52c1f87aa9d0cd139 62.99MB / 62.99MB 709.1s => => extracting sha256:59e22667830bf04fb35e15ed9c70023e9d121719bb87f0db7f3159ee7c7e0b8d 2.1s => => sha256:1c55318e78a1d3f438c6ca3cf6532d365a86fabbf7e3ecd14140e455f1489991 161B / 161B 328.8s => => sha256:4f4fb700ef54461cfa02571ae0db9a0dc1e0cdb5577484a6d75e68dc38e8acc1 32B / 32B 329.5s => => sha256:392ad068a4827c711e9af3956bd5d3bcac7e8d66b3dd35bb0a9fae60de47f80d 2.37kB / 2.37kB 330.2s => => extracting sha256:85a4e35755fb1aa44b91602297dc8d9f10eb8ad3f32baab32094cebc0eda41a4 0.0s => => sha256:65375761a96d26587431452e982c657d479c41c41027a7f0acf37a6a21fd1112 180B / 180B 330.9s => => extracting sha256:9ac051fdbd99f7d8c9e496724860b8ae3373f24d6f8a54f1d9096526df425d3c 2.3s => => extracting sha256:cef14de45bb7cc343e593f80531764848fe724db9084ae4a3cabacc7a7e24083 0.0s => => extracting sha256:28f95146d6851ca39a2ce18612cb5e5b19845ef85e4bb95bfa3095193fdf5777 0.0s => => extracting sha256:68a03bb16ee6a2c356d2e354bab5ec566dd7ef1e4e6daee52c1f87aa9d0cd139 0.6s => => extracting sha256:1c55318e78a1d3f438c6ca3cf6532d365a86fabbf7e3ecd14140e455f1489991 0.0s => => extracting sha256:4f4fb700ef54461cfa02571ae0db9a0dc1e0cdb5577484a6d75e68dc38e8acc1 0.0s => => extracting sha256:392ad068a4827c711e9af3956bd5d3bcac7e8d66b3dd35bb0a9fae60de47f80d 0.0s => => extracting sha256:65375761a96d26587431452e982c657d479c41c41027a7f0acf37a6a21fd1112 0.0s => [internal] load build context 0.7s => => transferring context: 107.93MB 0.7s => [2/4] COPY kubectl /usr/bin/kubectl 0.2s => [3/4] COPY nerdctl /usr/bin/nerdctl 0.1s => [4/4] COPY buildctl /usr/bin/buildctl 0.1s => exporting to image 0.1s => => exporting layers 0.1s => => writing image sha256:ad852c7e884a5f9f6e87fcb6112fbe0c616b601a69ae5cf74ba09f2456d4e578 0.0s => => naming to docker.io/library/jenkins-agent:v1 0.0s root@k8s-01:~/jenkins# docker login --username=aliyun3891595718 registry.cn-guangzhou.aliyuncs.com Password: WARNING! Your credentials are stored unencrypted in '/root/.docker/config.json'. Configure a credential helper to remove this warning. See https://docs.docker.com/go/credential-store/ Login Succeeded root@k8s-01:~/jenkins# docker push registry.cn-guangzhou.aliyuncs.com/xingcangku/jenkins-cangku:v1 The push refers to repository [registry.cn-guangzhou.aliyuncs.com/xingcangku/jenkins-cangku] 2de7e3a095aa: Pushed 235bf2aaf23c: Pushed 9c18f60b53bc: Pushed ec380c7051cf: Pushed 0c3e60359c38: Pushed 5f70bf18a086: Pushed 433332898d75: Pushed b2c56f1e2ab9: Pushed 1411e4580b87: Pushed df5f57ff732b: Pushed 3f360379e3d1: Pushed f03c3dd333b7: Pushed 7cc7fe68eff6: Pushed v1: digest: sha256:b3e519ae85d0f05ff170778c8ffae494879397d9881ca8bc905bc889da82fc07 size: 30475.2创建kube-config资源为了能让slave容器中能够使用 kubectl 工具来访问我们的 Kubernetes 集群,需要将其添加为secret资源,并挂载到pod中。root@k8s-01:~/jenkins/work# kubectl create secret generic -n cicd kube-config --from-file=/root/.kube/config secret/kube-config created5.2.1测试创建一个自由风格的流水线 下面是配置截图正常的日志显示,会起一个pod来执行的命令结束以后就会销毁5.3节点开启buildkit服务(可选)container容器运行时仅能运行容器,如果需要在CICD阶段构建镜像,则需要在执行构建镜像的节点手动安装buildkit服务并启用,具体步骤可参考文档:https://axzys.cn/index.php/archives/536/ 也可以在slave pod中新增一个container,运行buildkit服务。5.4配置Pod Template(可选)配置 Pod Template,就是配置 Jenkins Slave 运行的 Pod 模板,命名空间我们同样是用cicd,Labels设置为jenkins-slave,对于后面执行 Job 的时候需要用到该值,容器名称填写jnlp,这样可以替换默认的agent容器。镜像使用的是刚刚我们制作的slave镜像,加入了 kubectl 等一些实用的工具。 运行命令和命令参数为空。另外需要注意我们这里需要在下面挂载三个目录 /run/containerd/containerd.sock:该文件是用于 Pod 中的容器能够共享宿主机的Container,用于管理container镜像。 /root/.kube:将之前创建的kube-config资源挂载到容器的/root/.kube目录下,这样能够在 Pod 的容器中能够使用 kubectl 工具来访问我们的 Kubernetes 集群,方便我们后面在 Slave Pod 部署 Kubernetes 应用 /run/buildkit:该文件是用于 Pod 中的容器能够共享buildkit进程,用于构建container镜像。同时指定Service Accoun为之前创建的jenkins-admin除了在页面配置pod Template外,我们也可以通过pipeline配置。六、测试Kubernetes 插件的配置工作完成了,接下来我们就来添加一个 Job 任务,看是否能够在 Slave Pod 中执行,任务执行完成后看 Pod 是否会被销毁。6.1自由流水线测试创建自由流水线任务,勾选限制项目的运行节点,标签表达式填写我们配置的 Slave Pod 中的 Label,这两个地方必须保持一致。然后往下拉,在 Build 区域选择Execute shellecho "Hello Kubernetes" echo "测试获取Kubernetes信息" kubectl get node echo "测试获取container信息" nerdctl ns ls echo "测试buildkitd构建镜像" echo "FROM registry.cn-guangzhou.aliyuncs.com/xingcangku/busybox-latest:latest" > Dockerfile echo 'CMD ["echo","hello","container"]' >> Dockerfile nerdctl build -t buildkitd-test:v1 . nerdctl images | grep buildkitd-test现在我们直接在页面点击做成的 Build now (立即构建)触发构建即可,然后观察 Kubernetes 集群中 Pod 的变化root@k8s-03:~/bin# kubectl get pods -n cicd -o wide -w NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES jenkins-7d65887794-s4vhr 1/1 Running 0 9h 10.244.2.104 k8s-03 <none> <none> jenkins-agent-8x3mn 0/1 Pending 0 0s <none> <none> <none> <none> jenkins-agent-8x3mn 0/1 Pending 0 0s <none> k8s-03 <none> <none> jenkins-agent-8x3mn 0/1 ContainerCreating 0 0s <none> k8s-03 <none> <none> jenkins-agent-8x3mn 1/1 Running 0 1s 10.244.2.116 k8s-03 <none> <none> jenkins-agent-8x3mn 1/1 Terminating 0 13s 10.244.2.116 k8s-03 <none> <none> jenkins-agent-8x3mn 0/1 Terminating 0 13s <none> k8s-03 <none> <none> jenkins-agent-8x3mn 0/1 Terminating 0 14s 10.244.2.116 k8s-03 <none> <none> jenkins-agent-8x3mn 0/1 Terminating 0 14s 10.244.2.116 k8s-03 <none> <none> jenkins-agent-8x3mn 0/1 Terminating 0 14s 10.244.2.116 k8s-03 <none> <none>6.2pipeline-使用pod Template在流水线中指定pipeline脚本pipeline脚本如下:podTemplate(label: 'jenkins-slave', inheritFrom: 'jenkins-agent', cloud: 'k8s-local'){ node('jenkins-slave') { stage('测试获取Kubernetes信息') { sh 'kubectl get node' } stage('测试获取container信息') { sh 'nerdctl ns ls' } stage('测试buildkitd构建镜像'){ sh '''echo "FROM busybox" > Dockerfile echo \'CMD ["echo","hello","container"]\' >> Dockerfile nerdctl build -t buildkitd-test:v2 . nerdctl images | grep buildkitd-test''' } } }点击立即构建,查看控制台输出。6.3pipeline-自定义pod Template//创建一个Pod的模板,label为jenkins-agent podTemplate(label: 'jenkins-agent', cloud: 'k8s-local', containers: [ containerTemplate( name: 'jnlp', image: "harbor.local.com/cicd/jenkins-agent:v3", workingDir: '/home/jenkins/agent' ), containerTemplate( name: 'buildkitd', image: "harbor.local.com/cicd/buildkit:v0.13.2", privileged: true )], volumes:[ hostPathVolume(mountPath: '/run/containerd/containerd.sock', hostPath:'/run/containerd/containerd.sock'), secretVolume(mountPath: '/root/.kube/', secretName: 'kube-config', defaultMode: '420'), hostPathVolume(mountPath: '/run/buildkit',hostPath: '/run/buildkit') ] ) // 使用上文创建的pod模板 { node('jenkins-agent'){ stage('测试获取Kubernetes信息') { sh 'kubectl get node' } stage('测试获取container信息') { sh 'nerdctl ns ls' } stage('测试buildkitd构建镜像'){ sh '''echo "FROM busybox" > Dockerfile echo 'CMD ["echo","hello","container"]' >> Dockerfile nerdctl build -t buildkitd-test:v2 . nerdctl images | grep buildkitd-test''' } } }运行结果与上文一致。
jenkins与k8s连接 一、安装kubernetes插件在Jenkins的插件管理中安装Kubernetes插件 jenkins——>系统管理——>插件管理——>avaliable plugins二、本集群连接 2.1创建sa账号如果jenkins在k8s集群中部署,直接创建sa账号,并进行rbac授权即可,yaml文件参考前面文章。2.2创建cloud资源然后在jenkins——>系统管理——>Clouds——>New cloud——>输入cloud name并勾选类型为kubernetesroot@k8s-01:~/jenkins# cat deployment.yaml apiVersion: apps/v1 kind: Deployment metadata: name: jenkins namespace: cicd spec: replicas: 1 selector: matchLabels: app: jenkins template: metadata: labels: app: jenkins spec: securityContext: fsGroup: 1000 # 确保 Jenkins 用户有存储写入权限 serviceAccountName: jenkins-admin automountServiceAccountToken: true # 新增节点选择器,将 Pod 固定在 k8s-03 节点 nodeSelector: kubernetes.io/hostname: k8s-03 containers: - name: jenkins image: registry.cn-guangzhou.aliyuncs.com/xingcangku/jenkins-jenkins-lts-jdk17:lts-jdk17 imagePullPolicy: IfNotPresent ports: - containerPort: 8080 - containerPort: 50000 # 新增环境变量(可选) env: - name: JAVA_HOME value: "/usr/lib/jvm/amazon-corretto-17.0.16.8.1-linux-x64" volumeMounts: - name: jenkins-data mountPath: /var/jenkins_home # ============ 新增挂载 ============ - name: host-jvm mountPath: /usr/lib/jvm - name: maven-data mountPath: /usr/local/maven resources: limits: cpu: "1" memory: "3Gi" requests: cpu: "0.5" memory: "1Gi" livenessProbe: httpGet: path: /login port: 8080 initialDelaySeconds: 90 periodSeconds: 10 volumes: - name: jenkins-data persistentVolumeClaim: claimName: jenkins-pvc # ============ 新增的卷配置 ============ - name: host-jvm hostPath: path: /usr/lib/jvm type: Directory - name: maven-data hostPath: path: /usr/local/maven type: Directoryroot@k8s-01:~/jenkins# cat new-rbac.yaml apiVersion: v1 kind: ServiceAccount metadata: name: jenkins-admin namespace: cicd --- # 创建自定义 ClusterRole apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: jenkins-clusterrole rules: - apiGroups: [""] resources: ["pods", "pods/log", "services"] verbs: ["get", "list", "watch", "create", "update", "delete"] - apiGroups: ["apps"] resources: ["deployments"] verbs: ["*"] --- # 绑定 ServiceAccount 到 ClusterRole apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: jenkins-crb roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: jenkins-clusterrole subjects: - kind: ServiceAccount name: jenkins-admin namespace: cicdk8s1.24版本以后,行为变更:从 Kubernetes v1.24 开始,不再自动为 ServiceAccount 创建 Secret(令牌不再存储在 Secret 中) TokenRequest API:现在需要使用 TokenRequest API 获取令牌 root@k8s-01:~/jenkins# cat jenkins-secret.yaml apiVersion: v1 kind: Secret metadata: name: jenkins-admin-token namespace: cicd annotations: kubernetes.io/service-account.name: jenkins-admin type: kubernetes.io/service-account-token root@k8s-01:~/jenkins# kubectl apply -n cicd -f jenkins-secret.yaml secret/jenkins-admin-token created root@k8s-01:~/jenkins# kubectl describe sa jenkins-admin -n cicd Name: jenkins-admin Namespace: cicd Labels: <none> Annotations: <none> Image pull secrets: <none> Mountable secrets: <none> Tokens: jenkins-admin-token Events: <none> root@k8s-01:~/jenkins# kubectl get secret jenkins-admin-token -n cicd -o jsonpath='{.data.token}' | base64 -d eyJhbGciOiJSUzI1NiIsImtpZCI6IjJ0MTFFdDhfdnFBYkNuTnBSSXlyOFIzN1B0MW13cVVJNlFwZDV1VzR1WXcifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJjaWNkIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImplbmtpbnMtYWRtaW4tdG9rZW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiamVua2lucy1hZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjRkY2ViZjg1LTI0NzEtNGJjYi04Yzg5LWQ0MWI0NjAzN2RkZSIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpjaWNkOmplbmtpbnMtYWRtaW4ifQ.qvBiSwdCVbfMDnP0ElhnMcn__q65HDqidWw2JDQbrn7zrgNX2jjXlDxhA8RQFQaHhrTPGrOuP60vzfz4WgvJxwJvwIHaqqAbK8r3t-eTBpXNKltY3GEFEqxyjVlTd8q0DLW0OWZHUVZJrWhYT00Xa1ZViJgwQ2X0ogpAphSlvR351ZEDmDDxwxk4WwioZpmU22_weFamlU0g9SQVW5kBYGw06Tq_dPNL7cB0CDdPy0mSYckquEtG4xh-EIddPs9cGd1_OGurjwEkwX2-HvlfCXfoFkgo42lrOCaouWE4I4e21OXUCg5erFONSWSPKhhmhiLsjikByweCE0qaA2ZIUw#还要另外创建serviceAccount root@k8s-01:~/jenkins# cat jenkins-secret.yaml rbac.yaml apiVersion: v1 kind: Secret metadata: name: jenkins-admin-token namespace: cicd annotations: kubernetes.io/service-account.name: jenkins-admin type: kubernetes.io/service-account-token # rbac.yaml apiVersion: v1 kind: ServiceAccount metadata: name: jenkins-admin namespace: cicd --- kind: ClusterRoleBinding apiVersion: rbac.authorization.k8s.io/v1 metadata: name: jenkins-admin-crb roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: edit # 授予命名空间内管理权限 subjects: - kind: ServiceAccount name: jenkins-admin namespace: cicd#Kubernetes 服务证书 key root@k8s-01:~/jenkins# kubectl get secret jenkins-admin-token -n cicd -o jsonpath='{.data.ca\.crt}' | base64 -d -----BEGIN CERTIFICATE----- MIIDBTCCAe2gAwIBAgIIUTF7Qh3Q+fowDQYJKoZIhvcNAQELBQAwFTETMBEGA1UE AxMKa3ViZXJuZXRlczAeFw0yNTA3MzAxMjU3MDdaFw0zNTA3MjgxMzAyMDdaMBUx EzARBgNVBAMTCmt1YmVybmV0ZXMwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEK AoIBAQCv6lpzywPfjhKfl0HCNA/onj3MJyWI4z1JUwDlukI2j7ygm+kM2rWLpRYY wjNrvzq7R4ZD2SfiFbN/Lo/EV0zM0MXdcsI8hkR6txlKXjRkrC5crCihd9idk2UR Ov25k7bE3JpvG/zVswNMuliHx38gNsv1tfSv75lfCKyiyO3rrnj3LR9iYFvArgzY a1F5FXNjw0HVRVIPeH060i75G3YhKDVAQoZVdMoJfW7wwZDDHnh1/GB16a9Jws+r MjIQVD0YtxhQdg7WeV2nfCs0L8yXInKXwX6MGv+/HRPw140TihZwnC9gYFPisRJ5 EtUV+uq78w3Vj7Y2ANlTTQbN/F1bAgMBAAGjWTBXMA4GA1UdDwEB/wQEAwICpDAP BgNVHRMBAf8EBTADAQH/MB0GA1UdDgQWBBSvRW0owjCv5rHXwOgsyrI2QC0CxDAV BgNVHREEDjAMggprdWJlcm5ldGVzMA0GCSqGSIb3DQEBCwUAA4IBAQBL7BDL9wKu TTZ4Lx8aGAIjuEP1slw8FnDuFY2V2M8cu2wX1tlqYKJkIbwwc/dr59j6LhLgTZaP p02lQJXNRG6vR4zydgzXgsTMDXK1ANI6+7/jYgCwixGgBs/IafISCFkm1IkQ70Cw rgibN4MvybWewmucS21F62HQzO1xvrHGL8YVxvFvaUyhL9+7VhYeIX2MF3E2jLl5 kzT74Awv0O+4zBcULKrYQqNEErf5fpRLi+y9SaKA2e85DWexkhkIb6y1lZScLjRp q1lkgXqcriE653t78WrE1dSaCJY8QI94jYr4B2u7S1sbNJ9vPCDHQfFfl0DgRI/e K8+av0Qro/aA -----END CERTIFICATE-----点击kubernetes cloud details填写cloud详细信息 - Kubernetes地址:在集群内部暴露的k8s service名称https://kubernetes.default.svc - Kubernetes命名空间:jenkins sa所属的名称空间cicd - Jenkins地址:jenkins svc的名称:8080端口http://jenkins.cicd.svc:8080 使用刚刚获取的令牌在 Jenkins 中创建凭据: 凭据类型:Secret text Secret:粘贴上面的令牌值 ID:k8s-service-account-token 配置完成后点击连接测试,显示k8s集群版本,证明配置无误。三、跨集群连接在某些情况下,jenkins部署在k8s集群外,通过二进制或者docker方式部署,如果想要连接k8s集群实现资源自动创建。或者当前jenkins部署在k8s集群A中,需要通过jenkins实现集群B资源的自动创建发布,使用此方式连接。3.1配置思路jenkins要想连接并操作k8s集群,需要配置授权,请求k8s集群的kube apiserver的请求,可以和kubectl一样利用config文件用作请求的鉴权,默认在~/.kube/config下,也可以单独严格指定权限细节,生成一个jenkins专用的config文件。 在jenkins中能够识别的证书文件为PKCS#12 certificate,因此需要先将kubeconfig文件中的证书转换生成PKCS#12格式的pfx证书文件3.2生成证书我们可以使用yq命令行工具解析yaml,并提取相关的内容,然后通过base 64解码,最后生成文件 安装yq工具,仓库地址:https://github.com/mikefarah/yq [root@k8s-master ~]# wget https://github.com/mikefarah/yq/releases/download/v4.34.1/yq_linux_amd64.tar.gz [root@k8s-master ~]# tar -zxvf yq_linux_amd64.tar.gz [root@k8s-master ~]# mv yq_linux_amd64 /usr/bin/yq [root@k8s-master ~]# yq --version yq (https://github.com/mikefarah/yq/) version v4.34.1 [root@k8s-master ~]# mkdir -p /opt/jenkins-crt/certificate-authority-data——>base 64解码——>ca.crt client-certificate-data——>base 64解码——>client.crt client-key-data——>base 64解码——>client.key[root@k8s-master ~]# yq e '.clusters[0].cluster.certificate-authority-data' /root/.kube/config | base64 -d > /opt/jenkins-crt/ca.crt [root@k8s-master ~]# yq e '.users[0].user.client-certificate-data' /root/.kube/config | base64 -d > /opt/jenkins-crt/client.crt [root@k8s-master ~]# yq e '.users[0].user.client-key-data' /root/.kube/config | base64 -d > /opt/jenkins-crt/client.key [root@k8s-master ~]# cd /opt/jenkins-crt/ [root@k8s-master jenkins-crt]# ls -la 总用量 12 drwxr-xr-x 2 root root 56 6月 10 20:54 . drwxr-xr-x. 6 root root 65 6月 10 20:37 .. -rw-r--r-- 1 root root 1099 6月 10 20:53 ca.crt -rw-r--r-- 1 root root 1147 6月 10 20:53 client.crt -rw-r--r-- 1 root root 1675 6月 10 20:54 client.key3.3转换证书通过openssl进行证书格式的转换,生成Client P12认证文件cert.pfx,输入两次密码并牢记密码。[root@k8s-master jenkins-crt]# openssl pkcs12 -export -out cert.pfx -inkey client.key -in client.crt -certfile ca.crt Enter Export Password: Verifying - Enter Export Password: [root@k8s-master jenkins-crt]# ls -la 总用量 16 drwxr-xr-x 2 root root 72 6月 10 20:55 . drwxr-xr-x. 6 root root 65 6月 10 20:37 .. -rw-r--r-- 1 root root 1099 6月 10 20:53 ca.crt -rw------- 1 root root 3221 6月 10 20:55 cert.pfx -rw-r--r-- 1 root root 1147 6月 10 20:53 client.crt -rw-r--r-- 1 root root 1675 6月 10 20:54 client.key3.4导入证书打开jenkins的web界面,系统管理——>Credentials——>添加全局凭据 凭据的类型选择Certificate,证书上传刚才生成的cert.pfx证书文件,输入通过openssl生成证书文件时输入的密码3.5配置远程k8s集群地址jenkins——>系统管理——>Clouds——>New cloud——>输入cloud name并勾选类型为kubernetes 填写cloud详细信息 - Kubernetes地址:/root/.kube/config文件中cluster部分中server的内容 - Kubernetes命名空间:/root/.kube/config文件中cluster部分中name的内容 - Jenkins地址:jenkins服务的地址 - kubernetes服务证书key:ca.crt内容 - 凭据:选择刚刚创建的Certificate凭据配置完成后点击连接测试,显示k8s集群版本,证明配置无误。四、动态slave介绍 4.1为什么需要动态slave目前大多公司都采用 Jenkins 集群来搭建符合需求的 CI/CD 流程,然而传统的 Jenkins Slave 一主多从方式会存在一些痛点,比如: - 主 Master 发生单点故障时,整个流程都不可用了 - 每个 Slave 的配置环境不一样,来完成不同语言的编译打包等操作,但是这些差异化的配置导致管理起来非常不方便,维护起来也是比较费劲 - 资源分配不均衡,有的 Slave 要运行的 job 出现排队等待,而有的 Slave 处于空闲状态 - 资源有浪费,每台 Slave 可能是物理机或者虚拟机,当 Slave 处于空闲状态时,也不会完全释放掉资源。 正因为上面的这些种种痛点,我们渴望一种更高效更可靠的方式来完成这个 CI/CD 流程,而 Docker虚拟化容器技术能很好的解决这个痛点,又特别是在 Kubernetes 集群环境下面能够更好来解决上面的问题,下图是基于 Kubernetes 搭建 Jenkins 集群的简单示意图:从图上可以看到 Jenkins Master 和 Jenkins Slave 以 Pod 形式运行在 Kubernetes 集群的 Node 上,Master 运行在其中一个节点,并且将其配置数据存储到一个 Volume 上去,Slave 运行在各个节点上,并且它不是一直处于运行状态,它会按照需求动态的创建并自动删除。 这种方式的工作流程大致为:当 Jenkins Master 接受到 Build 请求时,会根据配置的 Label 动态创建一个运行在 Pod 中的 Jenkins Slave 并注册到 Master 上,当运行完 Job 后,这个 Slave 会被注销并且这个 Pod 也会自动删除,恢复到最初状态。4.2Jenkins Slave好处- 服务高可用,当 Jenkins Master 出现故障时,Kubernetes 会自动创建一个新的 Jenkins Master 容器,并且将 Volume 分配给新创建的容器,保证数据不丢失,从而达到集群服务高可用(这是k8s带来的资源控制器带来的优势) - 动态伸缩,合理使用资源,每次运行 Job 时,会自动创建一个 Jenkins Slave,Job 完成后,Slave 自动注销并删除容器,资源自动释放,而且 Kubernetes 会根据每个资源的使用情况,动态分配 Slave 到空闲的节点上创建,降低出现因某节点资源利用率高,还排队等待在该节点的情况。 - 扩展性好,当 Kubernetes 集群的资源严重不足而导致 Job 排队等待时,可以很容易的添加一个 Kubernetes Node 到集群中,从而实现扩展。五、动态slave配置 5.1制作slave镜像slave镜像应该包含以下功能: - 运行jenkins-agent服务 - 使用kubectl命令操作k8s集群 - 使用nerdctl工具管理container镜像 - 使用buildctl构建container镜像。#获取文件 root@k8s-01:~/jenkins/work# cp /usr/bin/kubectl . root@k8s-01:~/jenkins/work# cp /usr/bin/nerdctl . root@k8s-01:~/jenkins/work# cp /usr/local/bin/buildctl . root@k8s-01:~/jenkins/work# ls buildctl Dockerfile kubectl nerdctl#构建镜像 #在构建镜像过程中基于inbound-agent镜像,因为其中已经包含了jenkins-agent服务相关组件,再添加kubectl工具用于操作k8s,nerdctl和buildctl工具用于构建和管理container镜像。 root@k8s-01:~/jenkins/work# cat Dockerfile FROM jenkins/inbound-agent:latest-jdk17 USER root COPY kubectl /usr/bin/kubectl COPY nerdctl /usr/bin/nerdctl COPY buildctl /usr/bin/buildctl root@k8s-01:~/jenkins/work# docker build -t jenkins-agent:v1 . [+] Building 714.4s (9/9) FINISHED docker:default => [internal] load build definition from Dockerfile 0.0s => => transferring dockerfile: 181B 0.0s => [internal] load metadata for docker.io/jenkins/inbound-agent:latest-jdk17 4.1s => [internal] load .dockerignore 0.0s => => transferring context: 2B 0.0s => [1/4] FROM docker.io/jenkins/inbound-agent:latest-jdk17@sha256:591ba0391e1dc47af64432198be00a9e457c74d215970c4f1af592a21 709.8s => => resolve docker.io/jenkins/inbound-agent:latest-jdk17@sha256:591ba0391e1dc47af64432198be00a9e457c74d215970c4f1af592a210a 0.0s => => sha256:a90156da31f7db1823e946282d3743d1f917b9622d122a1d45818ef43c6f5dc9 8.35kB / 8.35kB 0.0s => => sha256:59e22667830bf04fb35e15ed9c70023e9d121719bb87f0db7f3159ee7c7e0b8d 28.23MB / 28.23MB 327.6s => => sha256:9ac051fdbd99f7d8c9e496724860b8ae3373f24d6f8a54f1d9096526df425d3c 43.12MB / 43.12MB 581.2s => => sha256:85a4e35755fb1aa44b91602297dc8d9f10eb8ad3f32baab32094cebc0eda41a4 3.32kB / 3.32kB 0.8s => => sha256:591ba0391e1dc47af64432198be00a9e457c74d215970c4f1af592a210a6c37b 3.14kB / 3.14kB 0.0s => => sha256:7eddb97bde91ed86d7e82e7fa5f23370b33e87882aafdbcfb2782fdec95f6231 2.19kB / 2.19kB 0.0s => => sha256:cef14de45bb7cc343e593f80531764848fe724db9084ae4a3cabacc7a7e24083 1.24MB / 1.24MB 14.3s => => sha256:28f95146d6851ca39a2ce18612cb5e5b19845ef85e4bb95bfa3095193fdf5777 1.24MB / 1.24MB 28.5s => => sha256:68a03bb16ee6a2c356d2e354bab5ec566dd7ef1e4e6daee52c1f87aa9d0cd139 62.99MB / 62.99MB 709.1s => => extracting sha256:59e22667830bf04fb35e15ed9c70023e9d121719bb87f0db7f3159ee7c7e0b8d 2.1s => => sha256:1c55318e78a1d3f438c6ca3cf6532d365a86fabbf7e3ecd14140e455f1489991 161B / 161B 328.8s => => sha256:4f4fb700ef54461cfa02571ae0db9a0dc1e0cdb5577484a6d75e68dc38e8acc1 32B / 32B 329.5s => => sha256:392ad068a4827c711e9af3956bd5d3bcac7e8d66b3dd35bb0a9fae60de47f80d 2.37kB / 2.37kB 330.2s => => extracting sha256:85a4e35755fb1aa44b91602297dc8d9f10eb8ad3f32baab32094cebc0eda41a4 0.0s => => sha256:65375761a96d26587431452e982c657d479c41c41027a7f0acf37a6a21fd1112 180B / 180B 330.9s => => extracting sha256:9ac051fdbd99f7d8c9e496724860b8ae3373f24d6f8a54f1d9096526df425d3c 2.3s => => extracting sha256:cef14de45bb7cc343e593f80531764848fe724db9084ae4a3cabacc7a7e24083 0.0s => => extracting sha256:28f95146d6851ca39a2ce18612cb5e5b19845ef85e4bb95bfa3095193fdf5777 0.0s => => extracting sha256:68a03bb16ee6a2c356d2e354bab5ec566dd7ef1e4e6daee52c1f87aa9d0cd139 0.6s => => extracting sha256:1c55318e78a1d3f438c6ca3cf6532d365a86fabbf7e3ecd14140e455f1489991 0.0s => => extracting sha256:4f4fb700ef54461cfa02571ae0db9a0dc1e0cdb5577484a6d75e68dc38e8acc1 0.0s => => extracting sha256:392ad068a4827c711e9af3956bd5d3bcac7e8d66b3dd35bb0a9fae60de47f80d 0.0s => => extracting sha256:65375761a96d26587431452e982c657d479c41c41027a7f0acf37a6a21fd1112 0.0s => [internal] load build context 0.7s => => transferring context: 107.93MB 0.7s => [2/4] COPY kubectl /usr/bin/kubectl 0.2s => [3/4] COPY nerdctl /usr/bin/nerdctl 0.1s => [4/4] COPY buildctl /usr/bin/buildctl 0.1s => exporting to image 0.1s => => exporting layers 0.1s => => writing image sha256:ad852c7e884a5f9f6e87fcb6112fbe0c616b601a69ae5cf74ba09f2456d4e578 0.0s => => naming to docker.io/library/jenkins-agent:v1 0.0s root@k8s-01:~/jenkins# docker login --username=aliyun3891595718 registry.cn-guangzhou.aliyuncs.com Password: WARNING! Your credentials are stored unencrypted in '/root/.docker/config.json'. Configure a credential helper to remove this warning. See https://docs.docker.com/go/credential-store/ Login Succeeded root@k8s-01:~/jenkins# docker push registry.cn-guangzhou.aliyuncs.com/xingcangku/jenkins-cangku:v1 The push refers to repository [registry.cn-guangzhou.aliyuncs.com/xingcangku/jenkins-cangku] 2de7e3a095aa: Pushed 235bf2aaf23c: Pushed 9c18f60b53bc: Pushed ec380c7051cf: Pushed 0c3e60359c38: Pushed 5f70bf18a086: Pushed 433332898d75: Pushed b2c56f1e2ab9: Pushed 1411e4580b87: Pushed df5f57ff732b: Pushed 3f360379e3d1: Pushed f03c3dd333b7: Pushed 7cc7fe68eff6: Pushed v1: digest: sha256:b3e519ae85d0f05ff170778c8ffae494879397d9881ca8bc905bc889da82fc07 size: 30475.2创建kube-config资源为了能让slave容器中能够使用 kubectl 工具来访问我们的 Kubernetes 集群,需要将其添加为secret资源,并挂载到pod中。root@k8s-01:~/jenkins/work# kubectl create secret generic -n cicd kube-config --from-file=/root/.kube/config secret/kube-config created5.2.1测试创建一个自由风格的流水线 下面是配置截图正常的日志显示,会起一个pod来执行的命令结束以后就会销毁5.3节点开启buildkit服务(可选)container容器运行时仅能运行容器,如果需要在CICD阶段构建镜像,则需要在执行构建镜像的节点手动安装buildkit服务并启用,具体步骤可参考文档:https://axzys.cn/index.php/archives/536/ 也可以在slave pod中新增一个container,运行buildkit服务。5.4配置Pod Template(可选)配置 Pod Template,就是配置 Jenkins Slave 运行的 Pod 模板,命名空间我们同样是用cicd,Labels设置为jenkins-slave,对于后面执行 Job 的时候需要用到该值,容器名称填写jnlp,这样可以替换默认的agent容器。镜像使用的是刚刚我们制作的slave镜像,加入了 kubectl 等一些实用的工具。 运行命令和命令参数为空。另外需要注意我们这里需要在下面挂载三个目录 /run/containerd/containerd.sock:该文件是用于 Pod 中的容器能够共享宿主机的Container,用于管理container镜像。 /root/.kube:将之前创建的kube-config资源挂载到容器的/root/.kube目录下,这样能够在 Pod 的容器中能够使用 kubectl 工具来访问我们的 Kubernetes 集群,方便我们后面在 Slave Pod 部署 Kubernetes 应用 /run/buildkit:该文件是用于 Pod 中的容器能够共享buildkit进程,用于构建container镜像。同时指定Service Accoun为之前创建的jenkins-admin除了在页面配置pod Template外,我们也可以通过pipeline配置。六、测试Kubernetes 插件的配置工作完成了,接下来我们就来添加一个 Job 任务,看是否能够在 Slave Pod 中执行,任务执行完成后看 Pod 是否会被销毁。6.1自由流水线测试创建自由流水线任务,勾选限制项目的运行节点,标签表达式填写我们配置的 Slave Pod 中的 Label,这两个地方必须保持一致。然后往下拉,在 Build 区域选择Execute shellecho "Hello Kubernetes" echo "测试获取Kubernetes信息" kubectl get node echo "测试获取container信息" nerdctl ns ls echo "测试buildkitd构建镜像" echo "FROM registry.cn-guangzhou.aliyuncs.com/xingcangku/busybox-latest:latest" > Dockerfile echo 'CMD ["echo","hello","container"]' >> Dockerfile nerdctl build -t buildkitd-test:v1 . nerdctl images | grep buildkitd-test现在我们直接在页面点击做成的 Build now (立即构建)触发构建即可,然后观察 Kubernetes 集群中 Pod 的变化root@k8s-03:~/bin# kubectl get pods -n cicd -o wide -w NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES jenkins-7d65887794-s4vhr 1/1 Running 0 9h 10.244.2.104 k8s-03 <none> <none> jenkins-agent-8x3mn 0/1 Pending 0 0s <none> <none> <none> <none> jenkins-agent-8x3mn 0/1 Pending 0 0s <none> k8s-03 <none> <none> jenkins-agent-8x3mn 0/1 ContainerCreating 0 0s <none> k8s-03 <none> <none> jenkins-agent-8x3mn 1/1 Running 0 1s 10.244.2.116 k8s-03 <none> <none> jenkins-agent-8x3mn 1/1 Terminating 0 13s 10.244.2.116 k8s-03 <none> <none> jenkins-agent-8x3mn 0/1 Terminating 0 13s <none> k8s-03 <none> <none> jenkins-agent-8x3mn 0/1 Terminating 0 14s 10.244.2.116 k8s-03 <none> <none> jenkins-agent-8x3mn 0/1 Terminating 0 14s 10.244.2.116 k8s-03 <none> <none> jenkins-agent-8x3mn 0/1 Terminating 0 14s 10.244.2.116 k8s-03 <none> <none>6.2pipeline-使用pod Template在流水线中指定pipeline脚本pipeline脚本如下:podTemplate(label: 'jenkins-slave', inheritFrom: 'jenkins-agent', cloud: 'k8s-local'){ node('jenkins-slave') { stage('测试获取Kubernetes信息') { sh 'kubectl get node' } stage('测试获取container信息') { sh 'nerdctl ns ls' } stage('测试buildkitd构建镜像'){ sh '''echo "FROM busybox" > Dockerfile echo \'CMD ["echo","hello","container"]\' >> Dockerfile nerdctl build -t buildkitd-test:v2 . nerdctl images | grep buildkitd-test''' } } }点击立即构建,查看控制台输出。6.3pipeline-自定义pod Template//创建一个Pod的模板,label为jenkins-agent podTemplate(label: 'jenkins-agent', cloud: 'k8s-local', containers: [ containerTemplate( name: 'jnlp', image: "harbor.local.com/cicd/jenkins-agent:v3", workingDir: '/home/jenkins/agent' ), containerTemplate( name: 'buildkitd', image: "harbor.local.com/cicd/buildkit:v0.13.2", privileged: true )], volumes:[ hostPathVolume(mountPath: '/run/containerd/containerd.sock', hostPath:'/run/containerd/containerd.sock'), secretVolume(mountPath: '/root/.kube/', secretName: 'kube-config', defaultMode: '420'), hostPathVolume(mountPath: '/run/buildkit',hostPath: '/run/buildkit') ] ) // 使用上文创建的pod模板 { node('jenkins-agent'){ stage('测试获取Kubernetes信息') { sh 'kubectl get node' } stage('测试获取container信息') { sh 'nerdctl ns ls' } stage('测试buildkitd构建镜像'){ sh '''echo "FROM busybox" > Dockerfile echo 'CMD ["echo","hello","container"]' >> Dockerfile nerdctl build -t buildkitd-test:v2 . nerdctl images | grep buildkitd-test''' } } }运行结果与上文一致。 -
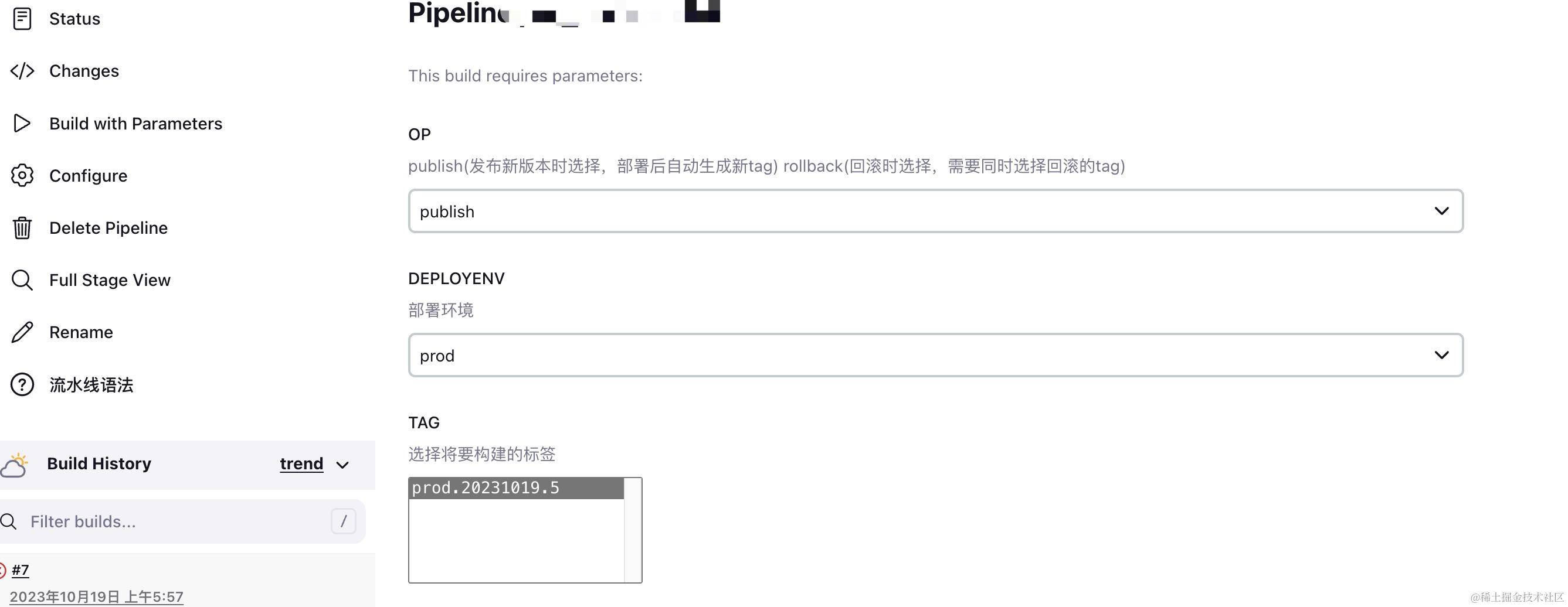
 jenkins根据tag构建 一、发布与回滚思路正常功能发布时,是基于master分支发布的,所以我在成功发布后,会将当时的master分支自动打上tag,当需要回滚时,则基于tag分支进行发布即可。二、安装配置Git Parameter 2.1安装插件要想出现tag模式的参数,需要安装git Parameter 插件,在Jenkins的Manage Jenkins→Plugins→Available Plugins 中安装2.2验证安装完成后在项目的配置页的This project is parameterized 中可以看到选项2.3仓库添加tag初始化仓库,添加tag并提交root@k8s-03:~/vue3_vite_element-plus# git config --global user.name "xing" root@k8s-03:~/vue3_vite_element-plus# git config --global user.email "7902731@qq.com" root@k8s-03:~/vue3_vite_element-plus# git config --global --list user.name=xing user.email=7902731@qq.com root@k8s-03:~/vue3_vite_element-plus# git tag -a v1.0 -m "1.0版本" root@k8s-03:~/vue3_vite_element-plus# git tag -l v1.0 root@k8s-03:~/vue3_vite_element-plus# git push origin v1.0 Username for 'http://192.168.30.181': xing Password for 'http://xing@192.168.30.181': Enumerating objects: 1, done. Counting objects: 100% (1/1), done. Writing objects: 100% (1/1), 160 bytes | 160.00 KiB/s, done. Total 1 (delta 0), reused 0 (delta 0), pack-reused 0 To http://192.168.30.181/xing/vue3_vite_element-plus.git * [new tag] v1.0 -> v1.0修改部分代码,并提交新版本。root@k8s-03:~/vue3_vite_element-plus# ls Dockerfile Jenkinsfile package.json README.md src vite.config.mjs index.html nginx.conf public screenshot test webstorm.config.js root@k8s-03:~/vue3_vite_element-plus# vi Dockerfile root@k8s-03:~/vue3_vite_element-plus# git commit -m "更新至v2" . [master 636d69b] 更新至v2 1 file changed, 2 insertions(+), 1 deletion(-) root@k8s-03:~/vue3_vite_element-plus# git tag -a v2.0 -m "2.0版本呢" root@k8s-03:~/vue3_vite_element-plus# git tag -l v1.0 v2.0 root@k8s-03:~/vue3_vite_element-plus# git push origin v2.0 Username for 'http://192.168.30.181': xing Password for 'http://xing@192.168.30.181': Enumerating objects: 6, done. Counting objects: 100% (6/6), done. Delta compression using up to 8 threads Compressing objects: 100% (4/4), done. Writing objects: 100% (4/4), 423 bytes | 423.00 KiB/s, done. Total 4 (delta 2), reused 0 (delta 0), pack-reused 0 To http://192.168.30.181/xing/vue3_vite_element-plus.git * [new tag] v2.0 -> v2.0 root@k8s-03:~/vue3_vite_element-plus# 查看gitlab tag信息,发现已经有v1.0,v2.0tag三、使用tag变量发布 3.1发布最新版本生成pipeline,指定分支为${tag} root@k8s-03:~/vue3_vite_element-plus# git ls-remote --tags origin Username for 'http://192.168.30.181': xing Password for 'http://xing@192.168.30.181': 3afadbd4e09f012ec0cb89e4cae667f8564ba5fa refs/tags/v1.0 a934816659500449a9413148e69d113faf5cccea refs/tags/v1.0^{} cf126d51958d9ed649b6b73e0f90929c6ac58694 refs/tags/v2.0 636d69bff7fb45b6732e977fdeee56c3628a2dcc refs/tags/v2.0^{}整体思路就是发布后就会有tar版本,如果有问题马上可以回滚到稳定的版本
jenkins根据tag构建 一、发布与回滚思路正常功能发布时,是基于master分支发布的,所以我在成功发布后,会将当时的master分支自动打上tag,当需要回滚时,则基于tag分支进行发布即可。二、安装配置Git Parameter 2.1安装插件要想出现tag模式的参数,需要安装git Parameter 插件,在Jenkins的Manage Jenkins→Plugins→Available Plugins 中安装2.2验证安装完成后在项目的配置页的This project is parameterized 中可以看到选项2.3仓库添加tag初始化仓库,添加tag并提交root@k8s-03:~/vue3_vite_element-plus# git config --global user.name "xing" root@k8s-03:~/vue3_vite_element-plus# git config --global user.email "7902731@qq.com" root@k8s-03:~/vue3_vite_element-plus# git config --global --list user.name=xing user.email=7902731@qq.com root@k8s-03:~/vue3_vite_element-plus# git tag -a v1.0 -m "1.0版本" root@k8s-03:~/vue3_vite_element-plus# git tag -l v1.0 root@k8s-03:~/vue3_vite_element-plus# git push origin v1.0 Username for 'http://192.168.30.181': xing Password for 'http://xing@192.168.30.181': Enumerating objects: 1, done. Counting objects: 100% (1/1), done. Writing objects: 100% (1/1), 160 bytes | 160.00 KiB/s, done. Total 1 (delta 0), reused 0 (delta 0), pack-reused 0 To http://192.168.30.181/xing/vue3_vite_element-plus.git * [new tag] v1.0 -> v1.0修改部分代码,并提交新版本。root@k8s-03:~/vue3_vite_element-plus# ls Dockerfile Jenkinsfile package.json README.md src vite.config.mjs index.html nginx.conf public screenshot test webstorm.config.js root@k8s-03:~/vue3_vite_element-plus# vi Dockerfile root@k8s-03:~/vue3_vite_element-plus# git commit -m "更新至v2" . [master 636d69b] 更新至v2 1 file changed, 2 insertions(+), 1 deletion(-) root@k8s-03:~/vue3_vite_element-plus# git tag -a v2.0 -m "2.0版本呢" root@k8s-03:~/vue3_vite_element-plus# git tag -l v1.0 v2.0 root@k8s-03:~/vue3_vite_element-plus# git push origin v2.0 Username for 'http://192.168.30.181': xing Password for 'http://xing@192.168.30.181': Enumerating objects: 6, done. Counting objects: 100% (6/6), done. Delta compression using up to 8 threads Compressing objects: 100% (4/4), done. Writing objects: 100% (4/4), 423 bytes | 423.00 KiB/s, done. Total 4 (delta 2), reused 0 (delta 0), pack-reused 0 To http://192.168.30.181/xing/vue3_vite_element-plus.git * [new tag] v2.0 -> v2.0 root@k8s-03:~/vue3_vite_element-plus# 查看gitlab tag信息,发现已经有v1.0,v2.0tag三、使用tag变量发布 3.1发布最新版本生成pipeline,指定分支为${tag} root@k8s-03:~/vue3_vite_element-plus# git ls-remote --tags origin Username for 'http://192.168.30.181': xing Password for 'http://xing@192.168.30.181': 3afadbd4e09f012ec0cb89e4cae667f8564ba5fa refs/tags/v1.0 a934816659500449a9413148e69d113faf5cccea refs/tags/v1.0^{} cf126d51958d9ed649b6b73e0f90929c6ac58694 refs/tags/v2.0 636d69bff7fb45b6732e977fdeee56c3628a2dcc refs/tags/v2.0^{}整体思路就是发布后就会有tar版本,如果有问题马上可以回滚到稳定的版本 -
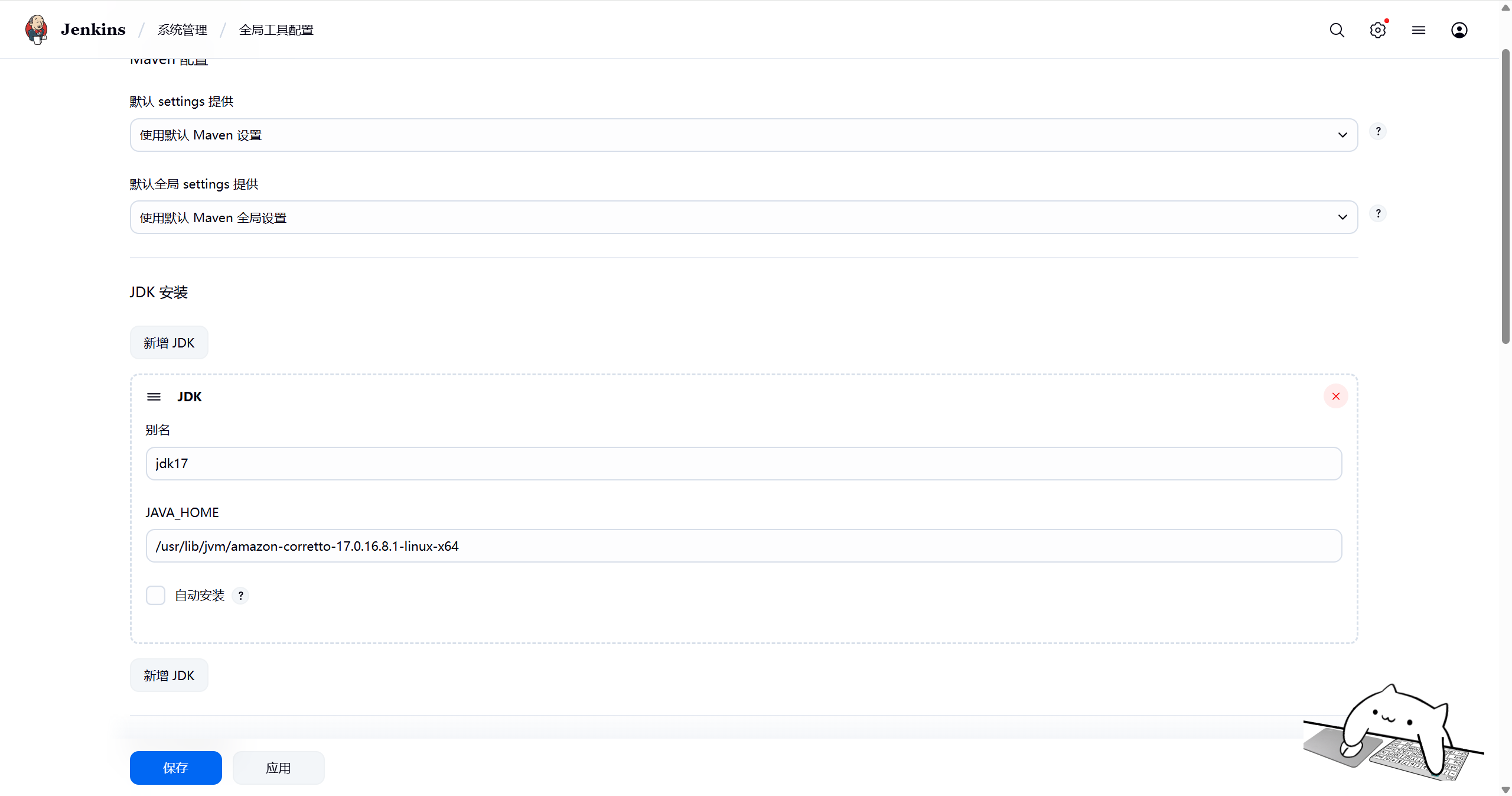
 jenkins与Maven集成 一、安装配置Maven此处以rpm包部署jenkins为例,以下操作在jenkins所在服务器执行。 maven下载地址:https://maven.apache.org/download.cgi1.1安装Maven[root@jenkins ~]# wget https://dlcdn.apache.org/maven/maven-3/3.9.6/binaries/apache-maven-3.9.6-bin.tar.gz [root@jenkins ~]# mkdir /usr/local/maven [root@jenkins ~]# tar -zxf apache-maven-3.9.6-bin.tar.gz -C /usr/local/maven/ [root@jenkins ~]# cd /usr/local/maven/apache-maven-3.9.6/ [root@jenkins apache-maven-3.9.3]# ls bin boot conf lib LICENSE NOTICE README.txt1.2设置maven的阿里云镜像[root@jenkins apache-maven-3.9.6]# vim conf/settings.xml # 在159行的标签为</mirrors>前添加如下阿里云镜像 <mirror> <id>alimaven</id> <name>aliyun maven</name> <url>http://maven.aliyun.com/nexus/content/groups/public/</url> <mirrorOf>central</mirrorOf> </mirror>1.3配置环境变量tar -zxvf amazon-corretto-17.0.16.8.1-linux-x64.tar.gz -C /usr/lib/jvm/ root@k8s-03:/usr/lib/jvm# ls amazon-corretto-17.0.16.8.1-linux-x64 root@k8s-03:/usr/lib/jvm# sudo chown -R root:root /usr/lib/jvm/amazon-corretto-17.0.16.8.1-linux-x64/ root@k8s-03:/usr/lib/jvm# export JAVA_HOME=/usr/lib/jvm/amazon-corretto-17.0.16.8.1-linux-x64/ root@k8s-03:/usr/lib/jvm# export PATH=$JAVA_HOME/bin:$PATH root@k8s-03:/usr/lib/jvm# java -version openjdk version "17.0.16" 2025-07-15 LTS OpenJDK Runtime Environment Corretto-17.0.16.8.1 (build 17.0.16+8-LTS) OpenJDK 64-Bit Server VM Corretto-17.0.16.8.1 (build 17.0.16+8-LTS, mixed mode, sharing) root@k8s-03:/usr/lib/jvm# javac -version javac 17.0.16 root@k8s-03:/usr/lib/jvm# vi /etc/profile root@k8s-03:/usr/lib/jvm# cat /etc/profile # /etc/profile: system-wide .profile file for the Bourne shell (sh(1)) # and Bourne compatible shells (bash(1), ksh(1), ash(1), ...). if [ "${PS1-}" ]; then if [ "${BASH-}" ] && [ "$BASH" != "/bin/sh" ]; then # The file bash.bashrc already sets the default PS1. # PS1='\h:\w\$ ' if [ -f /etc/bash.bashrc ]; then . /etc/bash.bashrc fi else if [ "$(id -u)" -eq 0 ]; then PS1='# ' else PS1='$ ' fi fi fi if [ -d /etc/profile.d ]; then for i in /etc/profile.d/*.sh; do if [ -r $i ]; then . $i fi done unset i fi export MAVEN_HOME=/usr/local/maven/apache-maven-3.9.9 export PATH=${MAVEN_HOME}/bin:${PATH} JAVA_HOME=/usr/lib/jvm/amazon-corretto-17.0.16.8.1-linux-x64 PATH=$JAVA_HOME/bin:$PATH export JAVA_HOME PATH root@k8s-03:/usr/lib/jvm# source /etc/profile root@k8s-03:/usr/lib/jvm# mvn -v Apache Maven 3.9.9 (8e8579a9e76f7d015ee5ec7bfcdc97d260186937) Maven home: /usr/local/maven/apache-maven-3.9.9 Java version: 17.0.16, vendor: Amazon.com Inc., runtime: /usr/lib/jvm/amazon-corretto-17.0.16.8.1-linux-x64 Default locale: en_US, platform encoding: UTF-8 OS name: "linux", version: "5.15.0-151-generic", arch: "amd64", family: "unix" 二、jenkins配置Maven 2.1全局工具配置关联jdk和mavenjenkis——>manage jenkins——>tools 如遇yum安装jdk无法识别,可尝试下载二进制openjdk安装2.2添加jenkins全局变量jenkis——>manage jenkins——>System 新增JAVA_HOME、M2_HOME、PATH+EXTRA三、拉取java项目 3.1创建项目此处以springboot项目为例,项目地址https://gitee.com/axzys/sprint_boot_demo3.2创建凭据依次点击jenkins——>系统管理——>Credentials——> Add Credentials,类型选择username with password四、创建任务 4.1创建流水线任务新建一个类型为自由风格的任务4.2配置git仓库信息gitee的主分支名称为master4.3构建测试点击立即构建,查看构建信息五、打包测试 5.1修改任务修改gitlab与gitee连接中配置的任务,新增构建步骤。配置如下5.2构建测试可以看到控制台成功打印了打包信息六、读取pom.xml参数在执行 Java 项目的流水线时,我们经常要动态获取项目中的属性,很多属性都配置在项目的 pom.xml 中,使用Pipeline Utility Steps 插件提供能够读取 pom.xml 的方法,pipeline如下stage('读取pom.xml参数阶段'){ // 读取 Pom.xml 参数 pom = readMavenPom file: './pom.xml' // 输出读取的参数 print "${pom.artifactId}" print = "${pom.version}" }
jenkins与Maven集成 一、安装配置Maven此处以rpm包部署jenkins为例,以下操作在jenkins所在服务器执行。 maven下载地址:https://maven.apache.org/download.cgi1.1安装Maven[root@jenkins ~]# wget https://dlcdn.apache.org/maven/maven-3/3.9.6/binaries/apache-maven-3.9.6-bin.tar.gz [root@jenkins ~]# mkdir /usr/local/maven [root@jenkins ~]# tar -zxf apache-maven-3.9.6-bin.tar.gz -C /usr/local/maven/ [root@jenkins ~]# cd /usr/local/maven/apache-maven-3.9.6/ [root@jenkins apache-maven-3.9.3]# ls bin boot conf lib LICENSE NOTICE README.txt1.2设置maven的阿里云镜像[root@jenkins apache-maven-3.9.6]# vim conf/settings.xml # 在159行的标签为</mirrors>前添加如下阿里云镜像 <mirror> <id>alimaven</id> <name>aliyun maven</name> <url>http://maven.aliyun.com/nexus/content/groups/public/</url> <mirrorOf>central</mirrorOf> </mirror>1.3配置环境变量tar -zxvf amazon-corretto-17.0.16.8.1-linux-x64.tar.gz -C /usr/lib/jvm/ root@k8s-03:/usr/lib/jvm# ls amazon-corretto-17.0.16.8.1-linux-x64 root@k8s-03:/usr/lib/jvm# sudo chown -R root:root /usr/lib/jvm/amazon-corretto-17.0.16.8.1-linux-x64/ root@k8s-03:/usr/lib/jvm# export JAVA_HOME=/usr/lib/jvm/amazon-corretto-17.0.16.8.1-linux-x64/ root@k8s-03:/usr/lib/jvm# export PATH=$JAVA_HOME/bin:$PATH root@k8s-03:/usr/lib/jvm# java -version openjdk version "17.0.16" 2025-07-15 LTS OpenJDK Runtime Environment Corretto-17.0.16.8.1 (build 17.0.16+8-LTS) OpenJDK 64-Bit Server VM Corretto-17.0.16.8.1 (build 17.0.16+8-LTS, mixed mode, sharing) root@k8s-03:/usr/lib/jvm# javac -version javac 17.0.16 root@k8s-03:/usr/lib/jvm# vi /etc/profile root@k8s-03:/usr/lib/jvm# cat /etc/profile # /etc/profile: system-wide .profile file for the Bourne shell (sh(1)) # and Bourne compatible shells (bash(1), ksh(1), ash(1), ...). if [ "${PS1-}" ]; then if [ "${BASH-}" ] && [ "$BASH" != "/bin/sh" ]; then # The file bash.bashrc already sets the default PS1. # PS1='\h:\w\$ ' if [ -f /etc/bash.bashrc ]; then . /etc/bash.bashrc fi else if [ "$(id -u)" -eq 0 ]; then PS1='# ' else PS1='$ ' fi fi fi if [ -d /etc/profile.d ]; then for i in /etc/profile.d/*.sh; do if [ -r $i ]; then . $i fi done unset i fi export MAVEN_HOME=/usr/local/maven/apache-maven-3.9.9 export PATH=${MAVEN_HOME}/bin:${PATH} JAVA_HOME=/usr/lib/jvm/amazon-corretto-17.0.16.8.1-linux-x64 PATH=$JAVA_HOME/bin:$PATH export JAVA_HOME PATH root@k8s-03:/usr/lib/jvm# source /etc/profile root@k8s-03:/usr/lib/jvm# mvn -v Apache Maven 3.9.9 (8e8579a9e76f7d015ee5ec7bfcdc97d260186937) Maven home: /usr/local/maven/apache-maven-3.9.9 Java version: 17.0.16, vendor: Amazon.com Inc., runtime: /usr/lib/jvm/amazon-corretto-17.0.16.8.1-linux-x64 Default locale: en_US, platform encoding: UTF-8 OS name: "linux", version: "5.15.0-151-generic", arch: "amd64", family: "unix" 二、jenkins配置Maven 2.1全局工具配置关联jdk和mavenjenkis——>manage jenkins——>tools 如遇yum安装jdk无法识别,可尝试下载二进制openjdk安装2.2添加jenkins全局变量jenkis——>manage jenkins——>System 新增JAVA_HOME、M2_HOME、PATH+EXTRA三、拉取java项目 3.1创建项目此处以springboot项目为例,项目地址https://gitee.com/axzys/sprint_boot_demo3.2创建凭据依次点击jenkins——>系统管理——>Credentials——> Add Credentials,类型选择username with password四、创建任务 4.1创建流水线任务新建一个类型为自由风格的任务4.2配置git仓库信息gitee的主分支名称为master4.3构建测试点击立即构建,查看构建信息五、打包测试 5.1修改任务修改gitlab与gitee连接中配置的任务,新增构建步骤。配置如下5.2构建测试可以看到控制台成功打印了打包信息六、读取pom.xml参数在执行 Java 项目的流水线时,我们经常要动态获取项目中的属性,很多属性都配置在项目的 pom.xml 中,使用Pipeline Utility Steps 插件提供能够读取 pom.xml 的方法,pipeline如下stage('读取pom.xml参数阶段'){ // 读取 Pom.xml 参数 pom = readMavenPom file: './pom.xml' // 输出读取的参数 print "${pom.artifactId}" print = "${pom.version}" } -
 gitlab和jenkins连接 一、gitlab配置 1.1 创建用户并登录1.2 导入项目需要管理员后台开启导入功能此处以Vue项目为例,项目地址:https://gitee.com/cuiliang0302/vue3_vite_element-plus.git二、jenkins配置 2.1 安装gitlab插件依次点击jenkins——>Manage Jenkins——>插件管理——>Plugins,在Jenkins的插件管理中安装GitLab插件三、连接测试 3.1 SSH验证#在容器中生成秘钥 root@k8s-01:~# kubectl get pods -n cicd NAME READY STATUS RESTARTS AGE jenkins-c884498c6-jt5rd 1/1 Running 4 (11m ago) 36h root@k8s-01:~# kubectl exec -it -n cicd jenkins-c884498c6-jt5rd -- /bin/sh $ ssh-keygen Generating public/private rsa key pair. Enter file in which to save the key (/var/jenkins_home/.ssh/id_rsa): Created directory '/var/jenkins_home/.ssh'. Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /var/jenkins_home/.ssh/id_rsa Your public key has been saved in /var/jenkins_home/.ssh/id_rsa.pub The key fingerprint is: SHA256:vslPYI4OboQAv+ClSj+l0s5BcOgWy71KoF3CFJnOKEM jenkins@jenkins-c884498c6-jt5rd The key's randomart image is: +---[RSA 3072]----+ | .o | |.E+. | |oO.. | |OoX. | |+O==. S | |+=+oo. = . | |+.+++ . o . | |o.o*oo . + | | .o+o . +.. | +----[SHA256]-----+ $ cat ~/.ssh/id_rsa.pub ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDAmjMVNkGL2gzFKQZDaC5jxOCXniZfBdkdYvqdralfhdVMTqxSgbQNbBX3E3S98L736/d0p7kgqZb/6FNGtNeAzHaQuWC2buPz1JAVw38dYuNbMazrpnsEcuoajbjACASwPSYfHhvq6zZ9xYMZMPqlgFgAgZGPmrC22cIgg1mFapwOIUyc56XqXViDOUZMGof5HQC+pNSV3iKfCt6agzPvDk6jXauis77n1T5gNiyeZixFDsXf9/6ORvd6XNUX0OfqZF2TUceIOWk+u1N/k5Y8CDjnHAJxftJJWFWtDwkANnqux1HA2BcUYCmZlvyPUNJHKTBWvQZ4Q7EbH0fX6YNN/n3doYovU4aA+OfpVlPv+4tzwUHSy5bauVUDT42Bg1KZtCwDIvf2rxrTmWCbb8ceNPti8/XzzccuZ8al382cE2yK0i6/PUjrI3Azk/NAKVdCERb/RgYpimALfWmUoduPdcLHNwZOsm3JjvxHuP88YxxvRG5JkzpU8bbg/a1RKeM= jenkins@jenkins-c884498c6-jt5rd在gitlab中添加ssh密钥信息获取jenkins容器用户名和私钥$ whoami jenkins $ cat ~/.ssh/id_rsa -----BEGIN OPENSSH PRIVATE KEY----- b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn NhAAAAAwEAAQAAAYEAwJozFTZBi9oMxSkGQ2guY8Tgl54mXwXZHWL6na2pX4XVTE6sUoG0 DWwV9xN0vfC+9+v3dKe5IKmW/+hTRrTXgMx2kLlgtm7j89SQFcN/HWLjWzGs66Z7BHLqGo 24wAgEsD0mHx4b6us2fcWDGTD6pYBYAIGRj5qwttnCIINZhWqcDiFMnOel6l1YgzlGTBqH +R0AvqTUld4inwremoMz7w5Oo12rorO+59U+YDYsnmYsRQ7F3/f+jkb3elzVF9Dn6mRdk1 HHiDlpPrtTf5OWPAg45xwCcX7SSVhVrQ8JADZ6rsdRwNgXFGApmZb8j1DSRykwVr0GeEOx Gx9H1+mDTf593aGKL1OGgPjn6VZT7/uLc8FB0suW2rlVA0+NgYNSmbQsAyL39q8a05lgm2 /HHjT7YvP1883HLmfGpd/NnBNsitIuvz1I6yNwM5PzQClXQhEW/0YGKYpgC31plKHbj3XC xzcGTrJtyY78R7j/PGMcb0RuSZM6VPG24P2tUSnjAAAFmDaXUJE2l1CRAAAAB3NzaC1yc2 EAAAGBAMCaMxU2QYvaDMUpBkNoLmPE4JeeJl8F2R1i+p2tqV+F1UxOrFKBtA1sFfcTdL3w vvfr93SnuSCplv/oU0a014DMdpC5YLZu4/PUkBXDfx1i41sxrOumewRy6hqNuMAIBLA9Jh 8eG+rrNn3Fgxkw+qWAWACBkY+asLbZwiCDWYVqnA4hTJznpepdWIM5Rkwah/kdAL6k1JXe Ip8K3pqDM+8OTqNdq6KzvufVPmA2LJ5mLEUOxd/3/o5G93pc1RfQ5+pkXZNRx4g5aT67U3 +TljwIOOccAnF+0klYVa0PCQA2eq7HUcDYFxRgKZmW/I9Q0kcpMFa9BnhDsRsfR9fpg03+ fd2hii9ThoD45+lWU+/7i3PBQdLLltq5VQNPjYGDUpm0LAMi9/avGtOZYJtvxx40+2Lz9f PNxy5nxqXfzZwTbIrSLr89SOsjcDOT80ApV0IRFv9GBimKYAt9aZSh2491wsc3Bk6ybcmO /Ee4/zxjHG9EbkmTOlTxtuD9rVEp4wAAAAMBAAEAAAGABpcgKVkmbAUli7eIJdVSRQqvDr EUKgs2ryk8XxnaolCfiFFm1xnmEdGBfOdXBsrOlggmewDkNkhnSNFnzBMTDq6wXeph80wf E7BRz9TVLCm+ktfDzXpwWioedZMk37lGg8tL2yO6G9M5lZslDb8dzHz0RewpEWtfIZqY6G jmLskDlv4vs2y/wiG4jiDvFVqRDYafCGb2eTxVHfEOxeW4aLUqHq/tWA9jeGZVEJC5/R+M 4z4Kqku/k5m9DRxRFFQLFEKxuWidau45/e3Kqx7RHSFQuKIyGo44KBCQed3XcVnEexS9SI UUdhvYNqBX3KdCiDQphFcYoG360/+Pt9NVQ4/yTpHp7A2qSXHgVtEtYtUCdEd3TdsOeir5 s3dRDjRb3Hp+gJPVNSJ2cZJG8pBrVWfwLqv4wl/vJwDS3E20jCY2a+roc21LAbVV52bmjS MjfMpzayKHTamoeDvWA7+9pyeW0X/s/PDgkXgHqMlLpUsDloF7Xn6bHgmHtu02m88BAAAA wQCt/X9vXe7SbvE9q/DyQpWWRLFNYhB+qTEiLqh5ndyoej9cCsrpj9BrudPS2uh2xMxfS9 JfpUqk++tSKQxJb6LXQBmFh5+gEXVql415iIWFCUhm28QeaJ5IxvYVdN6uAqNH81mWnpo7 K3pzKKp1oJfMMbToLrJFrxgwSnrPRhhegjA0Hb6CmfO7N+sBss0SAmbQx3SMfXL30Hxjqa 0DeSrzg4i4HArm8cd89wSQEfx6500yhUG+AARHzCxpcSeuTaYAAADBAOuBZ4LO9glbwUCV FulNeVvnbrlFpFbovu9eg1ROYxkB8yEMS3s6HtGyM/0c6QxT14Qam1siGuxLYR9UgGSvl5 EOpS/1aGbr5UYBVDXrGh3OdrfyD0OIZuxxyY5liZ7sRA+LC+6cR6qmOaShwS/8Afru8KdU 1CYGU9Ndit8gS156imT/jRJgci0m+pSgtP9ZsGbxbfZCGZyG1QOmgQTOHmFw/eXm/qPZ6t SuBzz3IprArOn+MaNKxlh/qGB6kSjzAQAAAMEA0Vz/hyPNJwErFfngA8DdAo4OZPw9thcM 3n0Kv6/jeDglDWQ4/FfSVp9PdQdZNKlk/Yp5wXxUV1SxtKCEDXLC8DofDhxoVh9UKTJkpU LnoD5mfr5oHsZ9BONixBS1OkX/NDdIe+pQ+oGX1TaxavQnGwXulI/Xu4x8GIulwgDEaXYd NbXSU1Wu1/mmVuGrCq2s6hXgOJF8xJ0DiX0JmdgH9yNPOteJiaQcoZbL90xmlOM76zWyv7 5AbWNqZ4UL8bDjAAAAH2plbmtpbnNAamVua2lucy1jODg0NDk4YzYtanQ1cmQBAgM= -----END OPENSSH PRIVATE KEY----- jenkins创建密钥凭据,类型选择ssh username with private key获取仓库git连接地址创建自由风格的软件项目在源码管理中添加仓库地址,需要注意的是默认地址为git@gitlab-559d798d49-hpcjt:cuiliang/vue3_vite_element-plus.git,修改为git@gitlab-svc.cicd.svc:cuiliang/vue3_vite_element-plus.git,并在jenkins容器中执行命令,添加远程仓库地址。 #上面是gitlab跑在k8s当中需要修改的 下面是gitlab裸部署 git@192.168.30.181:xing/vue3_vite_element-plus.git$ $ git ls-remote -h -- git@192.168.30.181:xing/vue3_vite_element-plus.git HEAD The authenticity of host '192.168.30.181 (192.168.30.181)' can't be established. ED25519 key fingerprint is SHA256:2awMz8VKsoMHs1ylz/z1bl11ATG3AcIVJEABqhR51p0. This key is not known by any other names. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '192.168.30.181' (ED25519) to the list of known hosts.点击立即构建,可以拉取代码并获取git commit信息。3.2 http/https连接添加jenkins凭据 在jenkins中添加凭据,账号为gitlab账户和密码。 jenkins——>系统管理——>Credentials——>添加类型为username with password的全局凭据获取项目克隆地址访问gitlab项目页,获取项目http克隆地址。 http://192.168.30.181/xing/vue3_vite_element-plus.git创建自由风格任务测试新建一个自由风格软件项目测试如果是gitlab是跑在k8s里面的在源码管理中填写http仓库地址,并选择账号密码凭据,需要注意的是仓库地址默认使用gitlab的pod名称,需要改为svc名称方式。即http://gitlab-svc.cicd.svc/cuiliang/vue3_vite_element-plus.git点击立即构建,查看控制台日志,已经可以正常拉取项目代码,获取到git commit信息。3.3Access Token验证登录gitlab,依次点击项目——>设置——>访问令牌。角色设置为guest,授予api权限即可。glpat-d2zMJyr9Z3u_1b-B43s1创建凭据,依次点击jenkins——>系统管理——>Credentials——> Add Credentials,类型选择gitlab api token配置gitlab信息 jenkins——>系统管理——>系统配置,找到gitlab配置区域, gitlab url填写http://gitlab-svc.cicd.svc,然后点击 Test Connection,显示 Success,表示成功。四、webhook配置通常在企业实际开发过程中,当代码提交到master分支或者创建tag时,gitlab请求jenkins的webhook地址,完成持续构建和持续部署流程。4.1创建jenkins流水线项目4.1.1新建一个类型为流水线的任务pipeline { agent any stages { stage('Checkout') { steps { // 修正参数名并补充必要参数 git branch: 'master', credentialsId: 'gitlab-xing-password', // Jenkins凭据ID url: 'http://192.168.30.181/xing/vue3_vite_element-plus.git', poll: true, // 对应"√ Include in polling" changelog: true // 对应"√ Include in changelog" } } stage('build') { steps { echo '编译打包完成' } } } }如果不选择沙盒会报错接下来点击立即构建,测试是否可以正常拉取代码4.2 开启webhook配置配置gitlab策略,使用root用户登录——>管理员——>网络——>出站请求——>允许来自webhook和集成对本地网络的请求。获取jenkins webhook令牌 修改流水线任务,点击**Build when a change is pushed to GitLab的高级选项,生成令牌。切换回cuiliang用户——>vue项目——>设置——>webhooks——>填写jenkins生成的webhook地址和令牌。触发来源选择所有分支。查看jenkins构建历史,发现触发了自动构建五、项目添加Jenkinsfile通常在企业开发中,jenkinsfile文件存放在项目指定路径下,与仓库代码一同维护,根据环境灵活配置,而非jenkins中的固定配置。修改流水线配置,选择pipeline文件来自仓库提交代码到仓库后,查看jenkins构建历史,发现已经自动触发了一次构建
gitlab和jenkins连接 一、gitlab配置 1.1 创建用户并登录1.2 导入项目需要管理员后台开启导入功能此处以Vue项目为例,项目地址:https://gitee.com/cuiliang0302/vue3_vite_element-plus.git二、jenkins配置 2.1 安装gitlab插件依次点击jenkins——>Manage Jenkins——>插件管理——>Plugins,在Jenkins的插件管理中安装GitLab插件三、连接测试 3.1 SSH验证#在容器中生成秘钥 root@k8s-01:~# kubectl get pods -n cicd NAME READY STATUS RESTARTS AGE jenkins-c884498c6-jt5rd 1/1 Running 4 (11m ago) 36h root@k8s-01:~# kubectl exec -it -n cicd jenkins-c884498c6-jt5rd -- /bin/sh $ ssh-keygen Generating public/private rsa key pair. Enter file in which to save the key (/var/jenkins_home/.ssh/id_rsa): Created directory '/var/jenkins_home/.ssh'. Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /var/jenkins_home/.ssh/id_rsa Your public key has been saved in /var/jenkins_home/.ssh/id_rsa.pub The key fingerprint is: SHA256:vslPYI4OboQAv+ClSj+l0s5BcOgWy71KoF3CFJnOKEM jenkins@jenkins-c884498c6-jt5rd The key's randomart image is: +---[RSA 3072]----+ | .o | |.E+. | |oO.. | |OoX. | |+O==. S | |+=+oo. = . | |+.+++ . o . | |o.o*oo . + | | .o+o . +.. | +----[SHA256]-----+ $ cat ~/.ssh/id_rsa.pub ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDAmjMVNkGL2gzFKQZDaC5jxOCXniZfBdkdYvqdralfhdVMTqxSgbQNbBX3E3S98L736/d0p7kgqZb/6FNGtNeAzHaQuWC2buPz1JAVw38dYuNbMazrpnsEcuoajbjACASwPSYfHhvq6zZ9xYMZMPqlgFgAgZGPmrC22cIgg1mFapwOIUyc56XqXViDOUZMGof5HQC+pNSV3iKfCt6agzPvDk6jXauis77n1T5gNiyeZixFDsXf9/6ORvd6XNUX0OfqZF2TUceIOWk+u1N/k5Y8CDjnHAJxftJJWFWtDwkANnqux1HA2BcUYCmZlvyPUNJHKTBWvQZ4Q7EbH0fX6YNN/n3doYovU4aA+OfpVlPv+4tzwUHSy5bauVUDT42Bg1KZtCwDIvf2rxrTmWCbb8ceNPti8/XzzccuZ8al382cE2yK0i6/PUjrI3Azk/NAKVdCERb/RgYpimALfWmUoduPdcLHNwZOsm3JjvxHuP88YxxvRG5JkzpU8bbg/a1RKeM= jenkins@jenkins-c884498c6-jt5rd在gitlab中添加ssh密钥信息获取jenkins容器用户名和私钥$ whoami jenkins $ cat ~/.ssh/id_rsa -----BEGIN OPENSSH PRIVATE KEY----- b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn NhAAAAAwEAAQAAAYEAwJozFTZBi9oMxSkGQ2guY8Tgl54mXwXZHWL6na2pX4XVTE6sUoG0 DWwV9xN0vfC+9+v3dKe5IKmW/+hTRrTXgMx2kLlgtm7j89SQFcN/HWLjWzGs66Z7BHLqGo 24wAgEsD0mHx4b6us2fcWDGTD6pYBYAIGRj5qwttnCIINZhWqcDiFMnOel6l1YgzlGTBqH +R0AvqTUld4inwremoMz7w5Oo12rorO+59U+YDYsnmYsRQ7F3/f+jkb3elzVF9Dn6mRdk1 HHiDlpPrtTf5OWPAg45xwCcX7SSVhVrQ8JADZ6rsdRwNgXFGApmZb8j1DSRykwVr0GeEOx Gx9H1+mDTf593aGKL1OGgPjn6VZT7/uLc8FB0suW2rlVA0+NgYNSmbQsAyL39q8a05lgm2 /HHjT7YvP1883HLmfGpd/NnBNsitIuvz1I6yNwM5PzQClXQhEW/0YGKYpgC31plKHbj3XC xzcGTrJtyY78R7j/PGMcb0RuSZM6VPG24P2tUSnjAAAFmDaXUJE2l1CRAAAAB3NzaC1yc2 EAAAGBAMCaMxU2QYvaDMUpBkNoLmPE4JeeJl8F2R1i+p2tqV+F1UxOrFKBtA1sFfcTdL3w vvfr93SnuSCplv/oU0a014DMdpC5YLZu4/PUkBXDfx1i41sxrOumewRy6hqNuMAIBLA9Jh 8eG+rrNn3Fgxkw+qWAWACBkY+asLbZwiCDWYVqnA4hTJznpepdWIM5Rkwah/kdAL6k1JXe Ip8K3pqDM+8OTqNdq6KzvufVPmA2LJ5mLEUOxd/3/o5G93pc1RfQ5+pkXZNRx4g5aT67U3 +TljwIOOccAnF+0klYVa0PCQA2eq7HUcDYFxRgKZmW/I9Q0kcpMFa9BnhDsRsfR9fpg03+ fd2hii9ThoD45+lWU+/7i3PBQdLLltq5VQNPjYGDUpm0LAMi9/avGtOZYJtvxx40+2Lz9f PNxy5nxqXfzZwTbIrSLr89SOsjcDOT80ApV0IRFv9GBimKYAt9aZSh2491wsc3Bk6ybcmO /Ee4/zxjHG9EbkmTOlTxtuD9rVEp4wAAAAMBAAEAAAGABpcgKVkmbAUli7eIJdVSRQqvDr EUKgs2ryk8XxnaolCfiFFm1xnmEdGBfOdXBsrOlggmewDkNkhnSNFnzBMTDq6wXeph80wf E7BRz9TVLCm+ktfDzXpwWioedZMk37lGg8tL2yO6G9M5lZslDb8dzHz0RewpEWtfIZqY6G jmLskDlv4vs2y/wiG4jiDvFVqRDYafCGb2eTxVHfEOxeW4aLUqHq/tWA9jeGZVEJC5/R+M 4z4Kqku/k5m9DRxRFFQLFEKxuWidau45/e3Kqx7RHSFQuKIyGo44KBCQed3XcVnEexS9SI UUdhvYNqBX3KdCiDQphFcYoG360/+Pt9NVQ4/yTpHp7A2qSXHgVtEtYtUCdEd3TdsOeir5 s3dRDjRb3Hp+gJPVNSJ2cZJG8pBrVWfwLqv4wl/vJwDS3E20jCY2a+roc21LAbVV52bmjS MjfMpzayKHTamoeDvWA7+9pyeW0X/s/PDgkXgHqMlLpUsDloF7Xn6bHgmHtu02m88BAAAA wQCt/X9vXe7SbvE9q/DyQpWWRLFNYhB+qTEiLqh5ndyoej9cCsrpj9BrudPS2uh2xMxfS9 JfpUqk++tSKQxJb6LXQBmFh5+gEXVql415iIWFCUhm28QeaJ5IxvYVdN6uAqNH81mWnpo7 K3pzKKp1oJfMMbToLrJFrxgwSnrPRhhegjA0Hb6CmfO7N+sBss0SAmbQx3SMfXL30Hxjqa 0DeSrzg4i4HArm8cd89wSQEfx6500yhUG+AARHzCxpcSeuTaYAAADBAOuBZ4LO9glbwUCV FulNeVvnbrlFpFbovu9eg1ROYxkB8yEMS3s6HtGyM/0c6QxT14Qam1siGuxLYR9UgGSvl5 EOpS/1aGbr5UYBVDXrGh3OdrfyD0OIZuxxyY5liZ7sRA+LC+6cR6qmOaShwS/8Afru8KdU 1CYGU9Ndit8gS156imT/jRJgci0m+pSgtP9ZsGbxbfZCGZyG1QOmgQTOHmFw/eXm/qPZ6t SuBzz3IprArOn+MaNKxlh/qGB6kSjzAQAAAMEA0Vz/hyPNJwErFfngA8DdAo4OZPw9thcM 3n0Kv6/jeDglDWQ4/FfSVp9PdQdZNKlk/Yp5wXxUV1SxtKCEDXLC8DofDhxoVh9UKTJkpU LnoD5mfr5oHsZ9BONixBS1OkX/NDdIe+pQ+oGX1TaxavQnGwXulI/Xu4x8GIulwgDEaXYd NbXSU1Wu1/mmVuGrCq2s6hXgOJF8xJ0DiX0JmdgH9yNPOteJiaQcoZbL90xmlOM76zWyv7 5AbWNqZ4UL8bDjAAAAH2plbmtpbnNAamVua2lucy1jODg0NDk4YzYtanQ1cmQBAgM= -----END OPENSSH PRIVATE KEY----- jenkins创建密钥凭据,类型选择ssh username with private key获取仓库git连接地址创建自由风格的软件项目在源码管理中添加仓库地址,需要注意的是默认地址为git@gitlab-559d798d49-hpcjt:cuiliang/vue3_vite_element-plus.git,修改为git@gitlab-svc.cicd.svc:cuiliang/vue3_vite_element-plus.git,并在jenkins容器中执行命令,添加远程仓库地址。 #上面是gitlab跑在k8s当中需要修改的 下面是gitlab裸部署 git@192.168.30.181:xing/vue3_vite_element-plus.git$ $ git ls-remote -h -- git@192.168.30.181:xing/vue3_vite_element-plus.git HEAD The authenticity of host '192.168.30.181 (192.168.30.181)' can't be established. ED25519 key fingerprint is SHA256:2awMz8VKsoMHs1ylz/z1bl11ATG3AcIVJEABqhR51p0. This key is not known by any other names. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '192.168.30.181' (ED25519) to the list of known hosts.点击立即构建,可以拉取代码并获取git commit信息。3.2 http/https连接添加jenkins凭据 在jenkins中添加凭据,账号为gitlab账户和密码。 jenkins——>系统管理——>Credentials——>添加类型为username with password的全局凭据获取项目克隆地址访问gitlab项目页,获取项目http克隆地址。 http://192.168.30.181/xing/vue3_vite_element-plus.git创建自由风格任务测试新建一个自由风格软件项目测试如果是gitlab是跑在k8s里面的在源码管理中填写http仓库地址,并选择账号密码凭据,需要注意的是仓库地址默认使用gitlab的pod名称,需要改为svc名称方式。即http://gitlab-svc.cicd.svc/cuiliang/vue3_vite_element-plus.git点击立即构建,查看控制台日志,已经可以正常拉取项目代码,获取到git commit信息。3.3Access Token验证登录gitlab,依次点击项目——>设置——>访问令牌。角色设置为guest,授予api权限即可。glpat-d2zMJyr9Z3u_1b-B43s1创建凭据,依次点击jenkins——>系统管理——>Credentials——> Add Credentials,类型选择gitlab api token配置gitlab信息 jenkins——>系统管理——>系统配置,找到gitlab配置区域, gitlab url填写http://gitlab-svc.cicd.svc,然后点击 Test Connection,显示 Success,表示成功。四、webhook配置通常在企业实际开发过程中,当代码提交到master分支或者创建tag时,gitlab请求jenkins的webhook地址,完成持续构建和持续部署流程。4.1创建jenkins流水线项目4.1.1新建一个类型为流水线的任务pipeline { agent any stages { stage('Checkout') { steps { // 修正参数名并补充必要参数 git branch: 'master', credentialsId: 'gitlab-xing-password', // Jenkins凭据ID url: 'http://192.168.30.181/xing/vue3_vite_element-plus.git', poll: true, // 对应"√ Include in polling" changelog: true // 对应"√ Include in changelog" } } stage('build') { steps { echo '编译打包完成' } } } }如果不选择沙盒会报错接下来点击立即构建,测试是否可以正常拉取代码4.2 开启webhook配置配置gitlab策略,使用root用户登录——>管理员——>网络——>出站请求——>允许来自webhook和集成对本地网络的请求。获取jenkins webhook令牌 修改流水线任务,点击**Build when a change is pushed to GitLab的高级选项,生成令牌。切换回cuiliang用户——>vue项目——>设置——>webhooks——>填写jenkins生成的webhook地址和令牌。触发来源选择所有分支。查看jenkins构建历史,发现触发了自动构建五、项目添加Jenkinsfile通常在企业开发中,jenkinsfile文件存放在项目指定路径下,与仓库代码一同维护,根据环境灵活配置,而非jenkins中的固定配置。修改流水线配置,选择pipeline文件来自仓库提交代码到仓库后,查看jenkins构建历史,发现已经自动触发了一次构建