搜索到
3
篇与
的结果
-
 traefik-gatway 测试yamlroot@k8s-01:~# cat traefik-gateway-nginx.yaml --- apiVersion: gateway.networking.k8s.io/v1 kind: GatewayClass metadata: name: traefik spec: controllerName: traefik.io/gateway-controller --- apiVersion: gateway.networking.k8s.io/v1 kind: Gateway metadata: name: traefik-gw namespace: default spec: gatewayClassName: traefik listeners: - name: http protocol: HTTP port: 8000 # ? 这里从 80 改成 8000,匹配 Traefik 的 entryPoints.web allowedRoutes: namespaces: from: Same --- apiVersion: apps/v1 kind: Deployment metadata: name: nginx namespace: default spec: replicas: 1 selector: matchLabels: app: nginx template: metadata: labels: app: nginx spec: containers: - name: nginx image: nginx:latest ports: - containerPort: 80 --- apiVersion: v1 kind: Service metadata: name: nginx namespace: default spec: selector: app: nginx ports: - port: 80 targetPort: 80 --- apiVersion: gateway.networking.k8s.io/v1 kind: HTTPRoute metadata: name: nginx namespace: default spec: parentRefs: - name: traefik-gw namespace: default sectionName: http # ? 明确绑定到上面 listener 名称 http(可选,但更清晰) hostnames: - "nginx.example.com" rules: - matches: - path: type: PathPrefix value: / backendRefs: - name: nginx port: 80 traefik 启用 Gateway API Providerroot@k8s-01:/woke/traefik# ls Changelog.md Chart.yaml crds EXAMPLES.md Guidelines.md LICENSE README.md templates traefik-values.yaml VALUES.md values.schema.json values.yaml root@k8s-01:/woke/traefik# cat traefik-values.yaml # 1. Dashboard / API 配置 api: dashboard: true # ⚠️ 这里是顶层的 ingressRoute,不在 api 下面 ingressRoute: dashboard: enabled: false # 关键:改成 web,让它走 80 端口(NodePort 30080) entryPoints: - web matchRule: PathPrefix(`/dashboard`) || PathPrefix(`/api`) annotations: {} labels: {} middlewares: [] tls: {} # 2. 入口点配置(保持你原来的) ports: traefik: port: 8080 expose: default: false exposedPort: 8080 protocol: TCP web: port: 8000 expose: default: true exposedPort: 80 protocol: TCP nodePort: 30080 websecure: port: 8443 hostPort: containerPort: expose: default: true exposedPort: 443 protocol: TCP nodePort: 30443 # 3. Service 配置:NodePort service: enabled: true type: NodePort single: true spec: externalTrafficPolicy: Cluster annotations: {} labels: {} # 4. RBAC rbac: enabled: true # 5. metrics(你这里开 prometheus 也没问题) metrics: prometheus: enabled: true logs: general: level: INFO access: enabled: true format: common # 6. 启用 Gateway API Provider providers: kubernetesGateway: enabled: true
traefik-gatway 测试yamlroot@k8s-01:~# cat traefik-gateway-nginx.yaml --- apiVersion: gateway.networking.k8s.io/v1 kind: GatewayClass metadata: name: traefik spec: controllerName: traefik.io/gateway-controller --- apiVersion: gateway.networking.k8s.io/v1 kind: Gateway metadata: name: traefik-gw namespace: default spec: gatewayClassName: traefik listeners: - name: http protocol: HTTP port: 8000 # ? 这里从 80 改成 8000,匹配 Traefik 的 entryPoints.web allowedRoutes: namespaces: from: Same --- apiVersion: apps/v1 kind: Deployment metadata: name: nginx namespace: default spec: replicas: 1 selector: matchLabels: app: nginx template: metadata: labels: app: nginx spec: containers: - name: nginx image: nginx:latest ports: - containerPort: 80 --- apiVersion: v1 kind: Service metadata: name: nginx namespace: default spec: selector: app: nginx ports: - port: 80 targetPort: 80 --- apiVersion: gateway.networking.k8s.io/v1 kind: HTTPRoute metadata: name: nginx namespace: default spec: parentRefs: - name: traefik-gw namespace: default sectionName: http # ? 明确绑定到上面 listener 名称 http(可选,但更清晰) hostnames: - "nginx.example.com" rules: - matches: - path: type: PathPrefix value: / backendRefs: - name: nginx port: 80 traefik 启用 Gateway API Providerroot@k8s-01:/woke/traefik# ls Changelog.md Chart.yaml crds EXAMPLES.md Guidelines.md LICENSE README.md templates traefik-values.yaml VALUES.md values.schema.json values.yaml root@k8s-01:/woke/traefik# cat traefik-values.yaml # 1. Dashboard / API 配置 api: dashboard: true # ⚠️ 这里是顶层的 ingressRoute,不在 api 下面 ingressRoute: dashboard: enabled: false # 关键:改成 web,让它走 80 端口(NodePort 30080) entryPoints: - web matchRule: PathPrefix(`/dashboard`) || PathPrefix(`/api`) annotations: {} labels: {} middlewares: [] tls: {} # 2. 入口点配置(保持你原来的) ports: traefik: port: 8080 expose: default: false exposedPort: 8080 protocol: TCP web: port: 8000 expose: default: true exposedPort: 80 protocol: TCP nodePort: 30080 websecure: port: 8443 hostPort: containerPort: expose: default: true exposedPort: 443 protocol: TCP nodePort: 30443 # 3. Service 配置:NodePort service: enabled: true type: NodePort single: true spec: externalTrafficPolicy: Cluster annotations: {} labels: {} # 4. RBAC rbac: enabled: true # 5. metrics(你这里开 prometheus 也没问题) metrics: prometheus: enabled: true logs: general: level: INFO access: enabled: true format: common # 6. 启用 Gateway API Provider providers: kubernetesGateway: enabled: true -
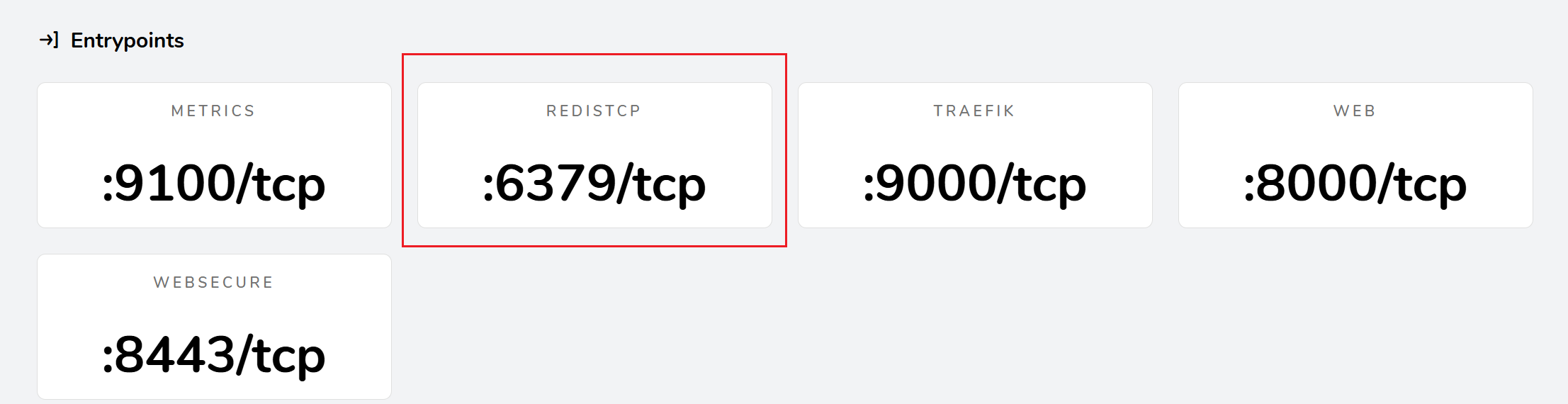
 traefik添加路由 一、路由配置(IngressRouteTCP) 1、TCP路由(不带TLS证书)#在yaml文件中添加端口 ports: - name: metrics containerPort: 9100 protocol: TCP - name: traefik containerPort: 9000 protocol: TCP - name: web containerPort: 8000 protocol: TCP - name: websecure containerPort: 8443 protocol: TCP securityContext: allowPrivilegeEscalation: false capabilities: drop: - ALL - NET_BIND_SERVICE readOnlyRootFilesystem: false volumeMounts: - name: data mountPath: /data readOnly: false # 允许写入 args: - "--global.checknewversion" - "--global.sendanonymoususage" - "--entryPoints.metrics.address=:9100/tcp" - "--entryPoints.traefik.address=:9000/tcp" - "--entryPoints.web.address=:8000/tcp" - "--entryPoints.websecure.address=:8443/tcp" - "--api.dashboard=true" - "--entryPoints.redistcp.address=:6379/tcp" #添加端口 - "--ping=true" - "--metrics.prometheus=true" - "--metrics.prometheus.entrypoint=metrics" - "--providers.kubernetescrd" - "--providers.kubernetescrd.allowEmptyServices=true" - "--providers.kubernetesingress" - "--providers.kubernetesingress.allowEmptyServices=true" - "--providers.kubernetesingress.ingressendpoint.publishedservice=traefik/traefik-release" - "--entryPoints.websecure.http.tls=true" - "--log.level=INFO"#实例 root@k8s01:~/helm/traefik/test# cat redis.yaml # redis.yaml apiVersion: apps/v1 kind: Deployment metadata: name: redis spec: selector: matchLabels: app: redis template: metadata: labels: app: redis spec: containers: - name: redis image: registry.cn-guangzhou.aliyuncs.com/xingcangku/redis:1.0 resources: limits: memory: "128Mi" cpu: "500m" ports: - containerPort: 6379 protocol: TCP --- apiVersion: v1 kind: Service metadata: name: redis spec: selector: app: redis ports: - port: 6379 targetPort: 6379 root@k8s01:~/helm/traefik/test# cat redis-IngressRoute.yaml apiVersion: traefik.io/v1alpha1 kind: IngressRouteTCP metadata: name: redis namespace: default # 确保在 Redis 的命名空间 spec: entryPoints: - redistcp # 使用新定义的入口点 routes: - match: HostSNI(`*`) # 正确语法 services: - name: redis port: 6379 #redis_Ingress.yaml apiVersion: traefik.io/v1alpha1 kind: IngressRouteTCP metadata: name: redis namespace: default # 确保在 Redis 的命名空间 spec: entryPoints: - redistcp # 使用新定义的入口点 routes: - match: HostSNI(`*`) # 正确语法 services: - name: redis port: 6379#可以查询6379映射的端口 kubectl -n traefik get endpoints #集群外部客户端配置hosts解析192.168.93.128 redis.test.com(域名可以随意填写,只要能解析到traefik所在节点即可),然后通过redis-cli工具访问redis,记得指定tcpep的端口。 # redis-cli -h redis.test.com -p 上面查询映射的端口 redis.test.com:9200> set key_a value_a OK redis.test.com:9200> get key_a "value_a" redis.test.com:9200> 2、TCP路由(带TLS证书)有时候为了安全要求,tcp传输也需要使用TLS证书加密,redis从6.0开始支持了tls证书通信。root@k8s01:~/helm/traefik/test/redis-ssl# openssl genrsa -out ca.key 4096 Generating RSA private key, 4096 bit long modulus (2 primes) ..........................................................................................................................................................................................................................................................++++ ................++++ e is 65537 (0x010001) root@k8s01:~/helm/traefik/test/redis-ssl# ls ca.key root@k8s01:~/helm/traefik/test/redis-ssl# openssl req -x509 -new -nodes -sha256 -key ca.key -days 3650 -subj '/O=Redis Test/CN=Certificate Authority' -out ca.crt root@k8s01:~/helm/traefik/test/redis-ssl# ls ca.crt ca.key root@k8s01:~/helm/traefik/test/redis-ssl# openssl genrsa -out redis.key 2048 Generating RSA private key, 2048 bit long modulus (2 primes) ..........................................................+++++ ...................................................................+++++ e is 65537 (0x010001) root@k8s01:~/helm/traefik/test/redis-ssl# openssl req -new -sha256 -key redis.key -subj '/O=Redis Test/CN=Server' | openssl x509 -req -sha256 -CA ca.crt -CAkey ca.key -CAserial ca.txt -CAcreateserial -days 365 -out redis.crt Signature ok subject=O = Redis Test, CN = Server Getting CA Private Key root@k8s01:~/helm/traefik/test/redis-ssl# openssl dhparam -out redis.dh 2048 Generating DH parameters, 2048 bit long safe prime, generator 2 This is going to take a long time ...............................................+..................................................................................................................................................................................................+................+..........................................+...........+.............+..............................................................+................................................................+.+....................................................................................................................................................................................................................................................................................................+..............+................................................................................................................................................................................................+...................................................................................................................................................................................................................................................................................+...........................................................................................................................................................................+........................................+.+.............................+....................................................................................................................................................+.............................................................................+.++*++*++*++* root@k8s01:~/helm/traefik/test/redis-ssl# ll total 24 drwxr-xr-x 2 root root 98 Jun 8 06:57 ./ drwxr-xr-x 3 root root 249 Jun 8 06:55 ../ -rw-r--r-- 1 root root 1895 Jun 8 06:56 ca.crt -rw------- 1 root root 3243 Jun 8 06:55 ca.key -rw-r--r-- 1 root root 41 Jun 8 06:57 ca.txt -rw-r--r-- 1 root root 1407 Jun 8 06:57 redis.crt -rw-r--r-- 1 root root 424 Jun 8 06:57 redis.dh -rw------- 1 root root 1679 Jun 8 06:56 redis.key root@k8s01:~/helm/traefik/test/redis-ssl# ca.crt # 根证书 (公开) ca.key # CA 私钥 (绝密) ca.txt # 证书序列号记录 redis.key # Redis 服务器私钥 (绝密) redis.crt # Redis 服务器证书 (公开) redis.dh # Diffie-Hellman 参数 (公开)#生成 CA 私钥 openssl genrsa -out ca.key 4096 作用:创建根证书颁发机构(CA)的私钥 genrsa:生成 RSA 私钥 -out ca.key:输出到文件 ca.key 4096:密钥长度(4096 位高安全级别) 输出文件:ca.key(CA 私钥,需严格保密)#生成 CA 根证书 openssl req -x509 -new -nodes -sha256 -key ca.key -days 3650 -subj '/O=Redis Test/CN=Certificate Authority' -out ca.crt 下面是对您生成 Redis SSL/TLS 证书的每一步命令的解析: 1. 生成 CA 私钥 openssl genrsa -out ca.key 4096 作用:创建根证书颁发机构(CA)的私钥 genrsa:生成 RSA 私钥 -out ca.key:输出到文件 ca.key 4096:密钥长度(4096 位高安全级别) 输出文件:ca.key(CA 私钥,需严格保密) 2. 生成 CA 根证书 openssl req -x509 -new -nodes -sha256 -key ca.key -days 3650 -subj '/O=Redis Test/CN=Certificate Authority' -out ca.crt 作用:创建自签名的根证书 req -x509:创建自签名证书(而不是证书请求) -new:生成新证书 -nodes:不加密私钥(No DES,明文存储) -sha256:使用 SHA-256 哈希算法 -key ca.key:指定 CA 私钥 -days 3650:有效期 10 年 -subj:证书主题信息 /O=Redis Test:组织名称 /CN=Certificate Authority:通用名称(标识为 CA) -out ca.crt:输出到 ca.crt 输出文件:ca.crt(受信任的根证书)#生成 Redis 服务器私钥 openssl genrsa -out redis.key 2048 作用:创建 Redis 服务器的私钥 与步骤 1 类似,但密钥长度 2048 位(更短,性能更好) 输出文件:redis.key(服务器私钥,需保密)#生成并签署 Redis 服务器证书 openssl req -new -sha256 -key redis.key -subj '/O=Redis Test/CN=Server' | openssl x509 -req -sha256 -CA ca.crt -CAkey ca.key -CAserial ca.txt -CAcreateserial -days 365 -out redis.crt #前半部分(生成证书请求) openssl req -new -sha256 -key redis.key -subj '/O=Redis Test/CN=Server' req -new:创建证书签名请求(CSR) -subj '/O=Redis Test/CN=Server':主题信息 CN=Server:标识为 Redis 服务器 #后半部分(签署证书) openssl x509 -req ... -out redis.crt x509 -req:签署证书请求 -CA ca.crt:指定 CA 证书 -CAkey ca.key:指定 CA 私钥 -CAserial ca.txt:指定序列号记录文件 -CAcreateserial:如果序列号文件不存在则创建 -days 365:有效期 1 年 输出文件: redis.crt:Redis 服务器证书 ca.txt:证书序列号记录文件(首次生成) #生成 Diffie-Hellman 参数 openssl dhparam -out redis.dh 2048 作用:创建安全密钥交换参数 dhparam:生成 Diffie-Hellman 参数 2048:密钥长度 输出文件:redis.dh(用于前向保密 PFS)创建secret资源,使用tls类型,包含redis.crt和redis.keyroot@k8s01:~/helm/traefik/test/redis-ssl# kubectl create secret tls redis-tls --key=redis.key --cert=redis.crt secret/redis-tls created root@k8s01:~/helm/traefik/test/redis-ssl# kubectl describe secrets redis-tls Name: redis-tls Namespace: default Labels: <none> Annotations: <none> Type: kubernetes.io/tls Data ==== tls.crt: 1407 bytes tls.key: 1679 bytes root@k8s01:~/helm/traefik/test/redis-ssl# 创建secret资源,使用generic类型,包含ca.crtroot@k8s01:~/helm/traefik/test/redis-ssl# kubectl create secret generic redis-ca --from-file=ca.crt=ca.crt secret/redis-ca created root@k8s01:~/helm/traefik/test/redis-ssl# kubectl describe secrets redis-ca Name: redis-ca Namespace: default Labels: <none> Annotations: <none> Type: Opaque Data ==== ca.crt: 1895 bytes root@k8s01:~/helm/traefik/test/redis-ssl# 修改redis配置,启用tls证书,并挂载证书文件apiVersion: v1 kind: ConfigMap metadata: name: redis labels: app: redis data: redis.conf : |- port 0 tls-port 6379 tls-cert-file /etc/tls/tls.crt tls-key-file /etc/tls/tls.key tls-ca-cert-file /etc/ca/ca.crt --- apiVersion: apps/v1 kind: Deployment metadata: name: redis spec: selector: matchLabels: app: redis template: metadata: labels: app: redis spec: containers: - name: redis image: registry.cn-guangzhou.aliyuncs.com/xingcangku/redis:1.0 resources: limits: memory: "128Mi" cpu: "500m" ports: - containerPort: 6379 protocol: TCP volumeMounts: - name: config mountPath: /etc/redis - name: tls mountPath: /etc/tls - name: ca mountPath: /etc/ca args: - /etc/redis/redis.conf volumes: - name: config configMap: name: redis - name: tls secret: secretName: redis-tls - name: ca secret: secretName: redis-ca --- apiVersion: v1 kind: Service metadata: name: redis spec: selector: app: redis ports: - port: 6379 targetPort: 6379root@k8s01:~/helm/traefik/test# kubectl apply -f redis.yaml configmap/redis created deployment.apps/redis configured service/redis unchangedroot@k8s01:~/helm/traefik/test/redis-ssl# # 生成客户端证书 root@k8s01:~/helm/traefik/test/redis-ssl# openssl req -newkey rsa:4096 -nodes \ > -keyout client.key \ > -subj "/CN=redis-client" \ > -out client.csr rt \ -days 365Generating a RSA private key ...........................................++++ .........................................................................................................++++ writing new private key to 'client.key' ----- root@k8s01:~/helm/traefik/test/redis-ssl# root@k8s01:~/helm/traefik/test/redis-ssl# # 用同一CA签发 root@k8s01:~/helm/traefik/test/redis-ssl# openssl x509 -req -in client.csr \ > -CA ca.crt \ > -CAkey ca.key \ > -CAcreateserial \ > -out client.crt \ > -days 365 Signature ok subject=CN = redis-client Getting CA Private Key root@k8s01:~/helm/traefik/test/redis-ssl# scp {client.crt,client.key,ca.crt} root@192.168.3.131:/tmp/redis-ssl/ root@192.168.3.131's password: client.crt 100% 1732 308.5KB/s 00:00 client.key 100% 3272 972.0KB/s 00:00 ca.crt 100% 1895 1.0MB/s 00:00 root@k8s01:~/helm/traefik/test# cat redis-IngressRoute-tls.yaml # redis-IngressRoute-tls.yaml apiVersion: traefik.io/v1alpha1 kind: IngressRouteTCP metadata: name: redis spec: entryPoints: - tcpep routes: - match: HostSNI(`redis.test.com`) services: - name: redis port: 6379 tls: passthrough: true # 重要:这里是启用透传的正确位置 root@k8s01:~/helm/traefik/test# #到集群意外的机器测试redis连接 低版本不支持TLS,需要编译安装6.0以上版本,并在编译时开启TLS root@ubuntu02:~/redis-stable# ./src/redis-cli -h redis.test.com -p 31757 --tls --sni redis.test.com --cert /tmp/redis-ssl/client.crt --key /tmp/redis-ssl/client.key --cacert /tmp/redis-ssl/ca.crt redis.test.com:31757> get key "1" redis.test.com:31757> root@ubuntu02:~/redis-stable# ./src/redis-cli \ > -h redis.test.com \ > -p 31757 \ > --tls \ > --sni redis.test.com \ > --cert /tmp/redis-ssl/client.crt \ > --key /tmp/redis-ssl/client.key \ > --cacert /tmp/redis-ssl/ca.crt redis.test.com:31757> set v1=1 (error) ERR wrong number of arguments for 'set' command redis.test.com:31757> set key 1 OK #配置对比 # redis-IngressRoute-tls.yaml apiVersion: traefik.io/v1alpha1 kind: IngressRouteTCP metadata: name: redis spec: entryPoints: ◦ tcpep routes: ◦ match: HostSNI(`redis.test.com`) services: ▪ name: redis port: 6379 tls: passthrough: true #上面的配置可以用 下面的配置用不了 # redis-IngressRoute-tls.yaml apiVersion: traefik.io/v1alpha1 kind: IngressRouteTCP metadata: name: redis spec: entryPoints: ◦ tcpep routes: ◦ match: HostSNI(`redis.test.com`) services: ▪ name: redis port: 6379 tls: secretName: redis-tls工作配置: 客户端 → [TLS握手] → Traefik (透传) → Redis服务器 │ └─ 直接处理TLS 失败配置: 客户端 → [TLS握手] → Traefik (终止TLS) → Redis服务器 │ │ ├─验证Traefik证书 └─ 接收明文连接但期望加密 └─客户端CA不信任Traefik证书 因为第一个配置是不经过Traefik直接到redis认证证书 工作原理:Traefik 不处理TLS流量,直接透传加密数据到Redis服务器 证书使用:客户端直接与Redis服务器进行TLS握手,使用Redis服务器自身的证书 验证过程:客户端用自有的ca.crt验证Redis服务器证书(CN=redis.test.com) 第二个是需要先和Traefik认证 工作原理:Traefik 在入口处终止TLS连接,然后以明文转发到Redis服务器 证书使用: 客户端验证 Traefik 的证书(来自 redis-tls secret) Redis 服务器接收非加密流量 验证过程:客户端验证的是 Traefik 的证书,而不是Redis服务器证书 失败的核心原因 证书不匹配问题: 当使用 secretName: redis-tls 时,Traefik 使用该 Secret 中的证书 但是客户端配置的CA证书是用于验证Redis服务器证书(CN=redis.test.com)的 Traefik 的证书(CN=TRAEFIK DEFAULT CERT)无法通过客户端CA验证
traefik添加路由 一、路由配置(IngressRouteTCP) 1、TCP路由(不带TLS证书)#在yaml文件中添加端口 ports: - name: metrics containerPort: 9100 protocol: TCP - name: traefik containerPort: 9000 protocol: TCP - name: web containerPort: 8000 protocol: TCP - name: websecure containerPort: 8443 protocol: TCP securityContext: allowPrivilegeEscalation: false capabilities: drop: - ALL - NET_BIND_SERVICE readOnlyRootFilesystem: false volumeMounts: - name: data mountPath: /data readOnly: false # 允许写入 args: - "--global.checknewversion" - "--global.sendanonymoususage" - "--entryPoints.metrics.address=:9100/tcp" - "--entryPoints.traefik.address=:9000/tcp" - "--entryPoints.web.address=:8000/tcp" - "--entryPoints.websecure.address=:8443/tcp" - "--api.dashboard=true" - "--entryPoints.redistcp.address=:6379/tcp" #添加端口 - "--ping=true" - "--metrics.prometheus=true" - "--metrics.prometheus.entrypoint=metrics" - "--providers.kubernetescrd" - "--providers.kubernetescrd.allowEmptyServices=true" - "--providers.kubernetesingress" - "--providers.kubernetesingress.allowEmptyServices=true" - "--providers.kubernetesingress.ingressendpoint.publishedservice=traefik/traefik-release" - "--entryPoints.websecure.http.tls=true" - "--log.level=INFO"#实例 root@k8s01:~/helm/traefik/test# cat redis.yaml # redis.yaml apiVersion: apps/v1 kind: Deployment metadata: name: redis spec: selector: matchLabels: app: redis template: metadata: labels: app: redis spec: containers: - name: redis image: registry.cn-guangzhou.aliyuncs.com/xingcangku/redis:1.0 resources: limits: memory: "128Mi" cpu: "500m" ports: - containerPort: 6379 protocol: TCP --- apiVersion: v1 kind: Service metadata: name: redis spec: selector: app: redis ports: - port: 6379 targetPort: 6379 root@k8s01:~/helm/traefik/test# cat redis-IngressRoute.yaml apiVersion: traefik.io/v1alpha1 kind: IngressRouteTCP metadata: name: redis namespace: default # 确保在 Redis 的命名空间 spec: entryPoints: - redistcp # 使用新定义的入口点 routes: - match: HostSNI(`*`) # 正确语法 services: - name: redis port: 6379 #redis_Ingress.yaml apiVersion: traefik.io/v1alpha1 kind: IngressRouteTCP metadata: name: redis namespace: default # 确保在 Redis 的命名空间 spec: entryPoints: - redistcp # 使用新定义的入口点 routes: - match: HostSNI(`*`) # 正确语法 services: - name: redis port: 6379#可以查询6379映射的端口 kubectl -n traefik get endpoints #集群外部客户端配置hosts解析192.168.93.128 redis.test.com(域名可以随意填写,只要能解析到traefik所在节点即可),然后通过redis-cli工具访问redis,记得指定tcpep的端口。 # redis-cli -h redis.test.com -p 上面查询映射的端口 redis.test.com:9200> set key_a value_a OK redis.test.com:9200> get key_a "value_a" redis.test.com:9200> 2、TCP路由(带TLS证书)有时候为了安全要求,tcp传输也需要使用TLS证书加密,redis从6.0开始支持了tls证书通信。root@k8s01:~/helm/traefik/test/redis-ssl# openssl genrsa -out ca.key 4096 Generating RSA private key, 4096 bit long modulus (2 primes) ..........................................................................................................................................................................................................................................................++++ ................++++ e is 65537 (0x010001) root@k8s01:~/helm/traefik/test/redis-ssl# ls ca.key root@k8s01:~/helm/traefik/test/redis-ssl# openssl req -x509 -new -nodes -sha256 -key ca.key -days 3650 -subj '/O=Redis Test/CN=Certificate Authority' -out ca.crt root@k8s01:~/helm/traefik/test/redis-ssl# ls ca.crt ca.key root@k8s01:~/helm/traefik/test/redis-ssl# openssl genrsa -out redis.key 2048 Generating RSA private key, 2048 bit long modulus (2 primes) ..........................................................+++++ ...................................................................+++++ e is 65537 (0x010001) root@k8s01:~/helm/traefik/test/redis-ssl# openssl req -new -sha256 -key redis.key -subj '/O=Redis Test/CN=Server' | openssl x509 -req -sha256 -CA ca.crt -CAkey ca.key -CAserial ca.txt -CAcreateserial -days 365 -out redis.crt Signature ok subject=O = Redis Test, CN = Server Getting CA Private Key root@k8s01:~/helm/traefik/test/redis-ssl# openssl dhparam -out redis.dh 2048 Generating DH parameters, 2048 bit long safe prime, generator 2 This is going to take a long time ...............................................+..................................................................................................................................................................................................+................+..........................................+...........+.............+..............................................................+................................................................+.+....................................................................................................................................................................................................................................................................................................+..............+................................................................................................................................................................................................+...................................................................................................................................................................................................................................................................................+...........................................................................................................................................................................+........................................+.+.............................+....................................................................................................................................................+.............................................................................+.++*++*++*++* root@k8s01:~/helm/traefik/test/redis-ssl# ll total 24 drwxr-xr-x 2 root root 98 Jun 8 06:57 ./ drwxr-xr-x 3 root root 249 Jun 8 06:55 ../ -rw-r--r-- 1 root root 1895 Jun 8 06:56 ca.crt -rw------- 1 root root 3243 Jun 8 06:55 ca.key -rw-r--r-- 1 root root 41 Jun 8 06:57 ca.txt -rw-r--r-- 1 root root 1407 Jun 8 06:57 redis.crt -rw-r--r-- 1 root root 424 Jun 8 06:57 redis.dh -rw------- 1 root root 1679 Jun 8 06:56 redis.key root@k8s01:~/helm/traefik/test/redis-ssl# ca.crt # 根证书 (公开) ca.key # CA 私钥 (绝密) ca.txt # 证书序列号记录 redis.key # Redis 服务器私钥 (绝密) redis.crt # Redis 服务器证书 (公开) redis.dh # Diffie-Hellman 参数 (公开)#生成 CA 私钥 openssl genrsa -out ca.key 4096 作用:创建根证书颁发机构(CA)的私钥 genrsa:生成 RSA 私钥 -out ca.key:输出到文件 ca.key 4096:密钥长度(4096 位高安全级别) 输出文件:ca.key(CA 私钥,需严格保密)#生成 CA 根证书 openssl req -x509 -new -nodes -sha256 -key ca.key -days 3650 -subj '/O=Redis Test/CN=Certificate Authority' -out ca.crt 下面是对您生成 Redis SSL/TLS 证书的每一步命令的解析: 1. 生成 CA 私钥 openssl genrsa -out ca.key 4096 作用:创建根证书颁发机构(CA)的私钥 genrsa:生成 RSA 私钥 -out ca.key:输出到文件 ca.key 4096:密钥长度(4096 位高安全级别) 输出文件:ca.key(CA 私钥,需严格保密) 2. 生成 CA 根证书 openssl req -x509 -new -nodes -sha256 -key ca.key -days 3650 -subj '/O=Redis Test/CN=Certificate Authority' -out ca.crt 作用:创建自签名的根证书 req -x509:创建自签名证书(而不是证书请求) -new:生成新证书 -nodes:不加密私钥(No DES,明文存储) -sha256:使用 SHA-256 哈希算法 -key ca.key:指定 CA 私钥 -days 3650:有效期 10 年 -subj:证书主题信息 /O=Redis Test:组织名称 /CN=Certificate Authority:通用名称(标识为 CA) -out ca.crt:输出到 ca.crt 输出文件:ca.crt(受信任的根证书)#生成 Redis 服务器私钥 openssl genrsa -out redis.key 2048 作用:创建 Redis 服务器的私钥 与步骤 1 类似,但密钥长度 2048 位(更短,性能更好) 输出文件:redis.key(服务器私钥,需保密)#生成并签署 Redis 服务器证书 openssl req -new -sha256 -key redis.key -subj '/O=Redis Test/CN=Server' | openssl x509 -req -sha256 -CA ca.crt -CAkey ca.key -CAserial ca.txt -CAcreateserial -days 365 -out redis.crt #前半部分(生成证书请求) openssl req -new -sha256 -key redis.key -subj '/O=Redis Test/CN=Server' req -new:创建证书签名请求(CSR) -subj '/O=Redis Test/CN=Server':主题信息 CN=Server:标识为 Redis 服务器 #后半部分(签署证书) openssl x509 -req ... -out redis.crt x509 -req:签署证书请求 -CA ca.crt:指定 CA 证书 -CAkey ca.key:指定 CA 私钥 -CAserial ca.txt:指定序列号记录文件 -CAcreateserial:如果序列号文件不存在则创建 -days 365:有效期 1 年 输出文件: redis.crt:Redis 服务器证书 ca.txt:证书序列号记录文件(首次生成) #生成 Diffie-Hellman 参数 openssl dhparam -out redis.dh 2048 作用:创建安全密钥交换参数 dhparam:生成 Diffie-Hellman 参数 2048:密钥长度 输出文件:redis.dh(用于前向保密 PFS)创建secret资源,使用tls类型,包含redis.crt和redis.keyroot@k8s01:~/helm/traefik/test/redis-ssl# kubectl create secret tls redis-tls --key=redis.key --cert=redis.crt secret/redis-tls created root@k8s01:~/helm/traefik/test/redis-ssl# kubectl describe secrets redis-tls Name: redis-tls Namespace: default Labels: <none> Annotations: <none> Type: kubernetes.io/tls Data ==== tls.crt: 1407 bytes tls.key: 1679 bytes root@k8s01:~/helm/traefik/test/redis-ssl# 创建secret资源,使用generic类型,包含ca.crtroot@k8s01:~/helm/traefik/test/redis-ssl# kubectl create secret generic redis-ca --from-file=ca.crt=ca.crt secret/redis-ca created root@k8s01:~/helm/traefik/test/redis-ssl# kubectl describe secrets redis-ca Name: redis-ca Namespace: default Labels: <none> Annotations: <none> Type: Opaque Data ==== ca.crt: 1895 bytes root@k8s01:~/helm/traefik/test/redis-ssl# 修改redis配置,启用tls证书,并挂载证书文件apiVersion: v1 kind: ConfigMap metadata: name: redis labels: app: redis data: redis.conf : |- port 0 tls-port 6379 tls-cert-file /etc/tls/tls.crt tls-key-file /etc/tls/tls.key tls-ca-cert-file /etc/ca/ca.crt --- apiVersion: apps/v1 kind: Deployment metadata: name: redis spec: selector: matchLabels: app: redis template: metadata: labels: app: redis spec: containers: - name: redis image: registry.cn-guangzhou.aliyuncs.com/xingcangku/redis:1.0 resources: limits: memory: "128Mi" cpu: "500m" ports: - containerPort: 6379 protocol: TCP volumeMounts: - name: config mountPath: /etc/redis - name: tls mountPath: /etc/tls - name: ca mountPath: /etc/ca args: - /etc/redis/redis.conf volumes: - name: config configMap: name: redis - name: tls secret: secretName: redis-tls - name: ca secret: secretName: redis-ca --- apiVersion: v1 kind: Service metadata: name: redis spec: selector: app: redis ports: - port: 6379 targetPort: 6379root@k8s01:~/helm/traefik/test# kubectl apply -f redis.yaml configmap/redis created deployment.apps/redis configured service/redis unchangedroot@k8s01:~/helm/traefik/test/redis-ssl# # 生成客户端证书 root@k8s01:~/helm/traefik/test/redis-ssl# openssl req -newkey rsa:4096 -nodes \ > -keyout client.key \ > -subj "/CN=redis-client" \ > -out client.csr rt \ -days 365Generating a RSA private key ...........................................++++ .........................................................................................................++++ writing new private key to 'client.key' ----- root@k8s01:~/helm/traefik/test/redis-ssl# root@k8s01:~/helm/traefik/test/redis-ssl# # 用同一CA签发 root@k8s01:~/helm/traefik/test/redis-ssl# openssl x509 -req -in client.csr \ > -CA ca.crt \ > -CAkey ca.key \ > -CAcreateserial \ > -out client.crt \ > -days 365 Signature ok subject=CN = redis-client Getting CA Private Key root@k8s01:~/helm/traefik/test/redis-ssl# scp {client.crt,client.key,ca.crt} root@192.168.3.131:/tmp/redis-ssl/ root@192.168.3.131's password: client.crt 100% 1732 308.5KB/s 00:00 client.key 100% 3272 972.0KB/s 00:00 ca.crt 100% 1895 1.0MB/s 00:00 root@k8s01:~/helm/traefik/test# cat redis-IngressRoute-tls.yaml # redis-IngressRoute-tls.yaml apiVersion: traefik.io/v1alpha1 kind: IngressRouteTCP metadata: name: redis spec: entryPoints: - tcpep routes: - match: HostSNI(`redis.test.com`) services: - name: redis port: 6379 tls: passthrough: true # 重要:这里是启用透传的正确位置 root@k8s01:~/helm/traefik/test# #到集群意外的机器测试redis连接 低版本不支持TLS,需要编译安装6.0以上版本,并在编译时开启TLS root@ubuntu02:~/redis-stable# ./src/redis-cli -h redis.test.com -p 31757 --tls --sni redis.test.com --cert /tmp/redis-ssl/client.crt --key /tmp/redis-ssl/client.key --cacert /tmp/redis-ssl/ca.crt redis.test.com:31757> get key "1" redis.test.com:31757> root@ubuntu02:~/redis-stable# ./src/redis-cli \ > -h redis.test.com \ > -p 31757 \ > --tls \ > --sni redis.test.com \ > --cert /tmp/redis-ssl/client.crt \ > --key /tmp/redis-ssl/client.key \ > --cacert /tmp/redis-ssl/ca.crt redis.test.com:31757> set v1=1 (error) ERR wrong number of arguments for 'set' command redis.test.com:31757> set key 1 OK #配置对比 # redis-IngressRoute-tls.yaml apiVersion: traefik.io/v1alpha1 kind: IngressRouteTCP metadata: name: redis spec: entryPoints: ◦ tcpep routes: ◦ match: HostSNI(`redis.test.com`) services: ▪ name: redis port: 6379 tls: passthrough: true #上面的配置可以用 下面的配置用不了 # redis-IngressRoute-tls.yaml apiVersion: traefik.io/v1alpha1 kind: IngressRouteTCP metadata: name: redis spec: entryPoints: ◦ tcpep routes: ◦ match: HostSNI(`redis.test.com`) services: ▪ name: redis port: 6379 tls: secretName: redis-tls工作配置: 客户端 → [TLS握手] → Traefik (透传) → Redis服务器 │ └─ 直接处理TLS 失败配置: 客户端 → [TLS握手] → Traefik (终止TLS) → Redis服务器 │ │ ├─验证Traefik证书 └─ 接收明文连接但期望加密 └─客户端CA不信任Traefik证书 因为第一个配置是不经过Traefik直接到redis认证证书 工作原理:Traefik 不处理TLS流量,直接透传加密数据到Redis服务器 证书使用:客户端直接与Redis服务器进行TLS握手,使用Redis服务器自身的证书 验证过程:客户端用自有的ca.crt验证Redis服务器证书(CN=redis.test.com) 第二个是需要先和Traefik认证 工作原理:Traefik 在入口处终止TLS连接,然后以明文转发到Redis服务器 证书使用: 客户端验证 Traefik 的证书(来自 redis-tls secret) Redis 服务器接收非加密流量 验证过程:客户端验证的是 Traefik 的证书,而不是Redis服务器证书 失败的核心原因 证书不匹配问题: 当使用 secretName: redis-tls 时,Traefik 使用该 Secret 中的证书 但是客户端配置的CA证书是用于验证Redis服务器证书(CN=redis.test.com)的 Traefik 的证书(CN=TRAEFIK DEFAULT CERT)无法通过客户端CA验证 -
 k8s安装traefik与实操 一、安装traefik先安装traefik-crds、下面的--- # Source: traefik/templates/rbac/serviceaccount.yaml kind: ServiceAccount apiVersion: v1 metadata: name: traefik-release namespace: traefik labels: app.kubernetes.io/name: traefik app.kubernetes.io/instance: traefik-release-default helm.sh/chart: traefik-35.4.0 app.kubernetes.io/managed-by: Helm annotations: automountServiceAccountToken: false --- # Source: traefik/templates/rbac/clusterrole.yaml kind: ClusterRole apiVersion: rbac.authorization.k8s.io/v1 metadata: name: traefik-release-default labels: app.kubernetes.io/name: traefik app.kubernetes.io/instance: traefik-release-default helm.sh/chart: traefik-35.4.0 app.kubernetes.io/managed-by: Helm rules: - apiGroups: - "" resources: - configmaps - nodes - services verbs: - get - list - watch - apiGroups: - discovery.k8s.io resources: - endpointslices verbs: - list - watch - apiGroups: - "" resources: - secrets verbs: - get - list - watch - apiGroups: - extensions - networking.k8s.io resources: - ingressclasses - ingresses verbs: - get - list - watch - apiGroups: - extensions - networking.k8s.io resources: - ingresses/status verbs: - update - apiGroups: - traefik.io resources: - ingressroutes - ingressroutetcps - ingressrouteudps - middlewares - middlewaretcps - serverstransports - serverstransporttcps - tlsoptions - tlsstores - traefikservices verbs: - get - list - watch --- # Source: traefik/templates/rbac/clusterrolebinding.yaml kind: ClusterRoleBinding apiVersion: rbac.authorization.k8s.io/v1 metadata: name: traefik-release-default labels: app.kubernetes.io/name: traefik app.kubernetes.io/instance: traefik-release-default helm.sh/chart: traefik-35.4.0 app.kubernetes.io/managed-by: Helm roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: traefik-release-default subjects: - kind: ServiceAccount name: traefik-release namespace: traefik --- # 添加PVC定义 apiVersion: v1 kind: PersistentVolumeClaim metadata: name: traefik-data-pvc namespace: traefik spec: accessModes: - ReadWriteMany # CephFS支持多节点读写 storageClassName: ceph-cephfs resources: requests: storage: 1Gi # 根据实际需求调整大小 --- # Source: traefik/templates/deployment.yaml apiVersion: apps/v1 kind: Deployment metadata: name: traefik-release namespace: traefik labels: app.kubernetes.io/name: traefik app.kubernetes.io/instance: traefik-release-default helm.sh/chart: traefik-35.4.0 app.kubernetes.io/managed-by: Helm annotations: spec: replicas: 1 selector: matchLabels: app.kubernetes.io/name: traefik app.kubernetes.io/instance: traefik-release-default strategy: type: RollingUpdate rollingUpdate: maxUnavailable: 0 maxSurge: 1 minReadySeconds: 0 template: metadata: annotations: prometheus.io/scrape: "true" prometheus.io/path: "/metrics" prometheus.io/port: "9100" labels: app.kubernetes.io/name: traefik app.kubernetes.io/instance: traefik-release-default helm.sh/chart: traefik-35.4.0 app.kubernetes.io/managed-by: Helm spec: securityContext: runAsUser: 0 runAsGroup: 0 fsGroup: 0 capabilities: add: ["NET_BIND_SERVICE"] serviceAccountName: traefik-release automountServiceAccountToken: true terminationGracePeriodSeconds: 60 hostNetwork: false containers: - image: registry.cn-guangzhou.aliyuncs.com/xingcangku/traefik:v3.0.0 imagePullPolicy: IfNotPresent name: traefik-release resources: readinessProbe: httpGet: path: /ping port: 9000 scheme: HTTP failureThreshold: 1 initialDelaySeconds: 2 periodSeconds: 10 successThreshold: 1 timeoutSeconds: 2 livenessProbe: httpGet: path: /ping port: 9000 scheme: HTTP failureThreshold: 3 initialDelaySeconds: 2 periodSeconds: 10 successThreshold: 1 timeoutSeconds: 2 lifecycle: ports: - name: metrics containerPort: 9100 protocol: TCP - name: traefik containerPort: 9000 protocol: TCP - name: web containerPort: 8000 protocol: TCP - name: websecure containerPort: 8443 protocol: TCP securityContext: allowPrivilegeEscalation: false capabilities: drop: - ALL - NET_BIND_SERVICE readOnlyRootFilesystem: false volumeMounts: - name: data mountPath: /data readOnly: false # 允许写入 args: - "--global.checknewversion" - "--global.sendanonymoususage" - "--entryPoints.metrics.address=:9100/tcp" - "--entryPoints.traefik.address=:9000/tcp" - "--entryPoints.web.address=:8000/tcp" - "--entryPoints.websecure.address=:8443/tcp" - "--api.dashboard=true" - "--ping=true" - "--metrics.prometheus=true" - "--metrics.prometheus.entrypoint=metrics" - "--providers.kubernetescrd" - "--providers.kubernetescrd.allowEmptyServices=true" - "--providers.kubernetesingress" - "--providers.kubernetesingress.allowEmptyServices=true" - "--providers.kubernetesingress.ingressendpoint.publishedservice=traefik/traefik-release" - "--entryPoints.websecure.http.tls=true" - "--log.level=INFO" env: - name: POD_NAME valueFrom: fieldRef: fieldPath: metadata.name - name: POD_NAMESPACE valueFrom: fieldRef: fieldPath: metadata.namespace volumes: # 替换emptyDir为PVC - name: data persistentVolumeClaim: claimName: traefik-data-pvc securityContext: runAsGroup: 65532 runAsNonRoot: true runAsUser: 65532 --- # Source: traefik/templates/service.yaml apiVersion: v1 kind: Service metadata: name: traefik namespace: traefik labels: app.kubernetes.io/name: traefik app.kubernetes.io/instance: traefik-release-default helm.sh/chart: traefik-35.4.0 app.kubernetes.io/managed-by: Helm annotations: spec: type: LoadBalancer selector: app.kubernetes.io/name: traefik app.kubernetes.io/instance: traefik-release-default ports: - port: 8000 name: web targetPort: web protocol: TCP - port: 8443 name: websecure targetPort: websecure protocol: TCP --- # Source: traefik/templates/ingressclass.yaml apiVersion: networking.k8s.io/v1 kind: IngressClass metadata: annotations: ingressclass.kubernetes.io/is-default-class: "true" labels: app.kubernetes.io/name: traefik app.kubernetes.io/instance: traefik-release-default helm.sh/chart: traefik-35.4.0 app.kubernetes.io/managed-by: Helm name: traefik-release spec: controller: traefik.io/ingress-controller root@k8s01:~/helm/traefik/traefik-helm-chart-35.4.0/traefik# cat dashboard.yaml apiVersion: traefik.io/v1alpha1 kind: IngressRoute metadata: name: dashboard namespace: traefik spec: entryPoints: - web routes: - match: Host(`traefik.local.com`) kind: Rule services: - name: api@internal kind: TraefikService 二、测试traefikkubectl create ns test-ns kubectl -n test-ns create deployment test-app --image=registry.cn-guangzhou.aliyuncs.com/xingcangku/nginx-alpine:1.0 kubectl -n test-ns expose deployment test-app --port=80cat <<EOF | kubectl apply -f - > apiVersion: networking.k8s.io/v1 > kind: Ingress > metadata: > name: test-ingress > namespace: test-ns > spec: > ingressClassName: traefik > rules: > - http: > paths: > - path: /test > pathType: Prefix > backend: > service: > name: test-app > port: > number: 80 > EOFWEB_PORT=$(kubectl get svc -n traefik traefik -o jsonpath='{.spec.ports[?(@.name=="web")].nodePort}')curl -v http://$NODE_IP:$WEB_PORT/test * Trying 192.168.3.200:32305... * Connected to 192.168.3.200 (192.168.3.200) port 32305 (#0) > GET /test HTTP/1.1 > Host: 192.168.3.200:32305 > User-Agent: curl/7.81.0 > Accept: */* > * Mark bundle as not supporting multiuse < HTTP/1.1 404 Not Found < Content-Length: 153 < Content-Type: text/html < Date: Thu, 29 May 2025 18:06:51 GMT < Server: nginx/1.27.5 < <html> <head><title>404 Not Found</title></head> <body> <center><h1>404 Not Found</h1></center> <hr><center>nginx/1.27.5</center> </body> </html> * Connection #0 to host 192.168.3.200 left intact#更新路径 cat <<EOF | kubectl apply -f - > apiVersion: networking.k8s.io/v1 > kind: Ingress > metadata: > name: test-ingress > namespace: test-ns > spec: > ingressClassName: traefik > rules: > - http: > paths: > - path: / > pathType: Prefix > backend: > service: > name: test-app > port: > number: 80 > EOF # 测试访问根路径 curl -v http://$NODE_IP:$WEB_PORT/ * Trying 192.168.3.200:32305... * Connected to 192.168.3.200 (192.168.3.200) port 32305 (#0) > GET / HTTP/1.1 > Host: 192.168.3.200:32305 > User-Agent: curl/7.81.0 > Accept: */* > * Mark bundle as not supporting multiuse < HTTP/1.1 200 OK < Accept-Ranges: bytes < Content-Length: 615 < Content-Type: text/html < Date: Thu, 29 May 2025 18:08:48 GMT < Etag: "67ffa8c6-267" < Last-Modified: Wed, 16 Apr 2025 12:55:34 GMT < Server: nginx/1.27.5 < <!DOCTYPE html> <html> <head> <title>Welcome to nginx!</title> <style> html { color-scheme: light dark; } body { width: 35em; margin: 0 auto; font-family: Tahoma, Verdana, Arial, sans-serif; } </style> </head> <body> <h1>Welcome to nginx!</h1> <p>If you see this page, the nginx web server is successfully installed and working. Further configuration is required.</p> <p>For online documentation and support please refer to <a href="http://nginx.org/">nginx.org</a>.<br/> Commercial support is available at <a href="http://nginx.com/">nginx.com</a>.</p> <p><em>Thank you for using nginx.</em></p> </body> </html> * Connection #0 to host 192.168.3.200 left intact#可以在集群内部访问 curl http://traefik-service.default.svc.cluster.localroot@k8s01:~/helm/traefik/test# kubectl get ingress -n test-ns NAME CLASS HOSTS ADDRESS PORTS AGE test-ingress traefik * 80 48m root@k8s01:~/helm/traefik/test# kubectl describe ingress test-ingress -n test-ns Name: test-ingress Labels: <none> Namespace: test-ns Address: Ingress Class: traefik Default backend: <default> Rules: Host Path Backends ---- ---- -------- * / test-app:80 (10.244.1.13:80) Annotations: <none> Events: <none> #命令查询 root@k8s01:~/helm/traefik/traefik-helm-chart-35.4.0/traefik# kubectl -n traefik describe svc traefik Name: traefik Namespace: traefik Labels: app.kubernetes.io/instance=traefik-release-default app.kubernetes.io/managed-by=Helm app.kubernetes.io/name=traefik helm.sh/chart=traefik-35.4.0 Annotations: <none> Selector: app.kubernetes.io/instance=traefik-release-default,app.kubernetes.io/name=traefik Type: LoadBalancer IP Family Policy: SingleStack IP Families: IPv4 IP: 10.103.186.47 IPs: 10.103.186.47 Port: web 8000/TCP TargetPort: web/TCP NodePort: web 30615/TCP Endpoints: 10.244.2.30:8000 Port: websecure 8443/TCP TargetPort: websecure/TCP NodePort: websecure 32113/TCP Endpoints: 10.244.2.30:8443 Session Affinity: None External Traffic Policy: Cluster Events: <none> root@k8s01:~/helm/traefik/traefik-helm-chart-35.4.0/traefik# kubectl -n traefik get endpoints NAME ENDPOINTS AGE traefik 10.244.2.30:8000,10.244.2.30:8443 26s traefik-crds 10.244.0.169:8000,10.244.0.169:8443 2d4h root@k8s01:~/helm/traefik/traefik-helm-chart-35.4.0/traefik# cat service.yaml # Source: traefik/templates/service.yaml apiVersion: v1 kind: Service metadata: name: traefik namespace: traefik labels: app.kubernetes.io/name: traefik app.kubernetes.io/instance: traefik-release-default helm.sh/chart: traefik-35.4.0 app.kubernetes.io/managed-by: Helm annotations: spec: type: LoadBalancer selector: app.kubernetes.io/name: traefik app.kubernetes.io/instance: traefik-release-default ports: - port: 8000 name: web targetPort: web protocol: TCP - port: 8443 name: websecure targetPort: websecure protocol: TCP root@k8s01:~/helm/traefik/traefik-helm-chart-35.4.0/traefik# kubectl get -n traefik svc NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE traefik LoadBalancer 10.103.186.47 <pending> 8000:30615/TCP,8443:32113/TCP 7m11s traefik-crds LoadBalancer 10.101.202.240 <pending> 80:31080/TCP,443:32480/TCP,6379:30634/TCP 2d5h root@k8s01:~/helm/traefik/traefik-helm-chart-35.4.0/traefik# kubectl get pods -n traefik -o wide NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES traefik-crds-766d79b985-c2sbr 1/1 Running 3 (6h13m ago) 2d4h 10.244.0.169 k8s01 <none> <none> traefik-release-589c7ff647-pdjh4 1/1 Running 0 25m 10.244.2.30 k8s03 <none> <none> root@k8s01:~/helm/traefik/traefik-helm-chart-35.4.0/traefik#
k8s安装traefik与实操 一、安装traefik先安装traefik-crds、下面的--- # Source: traefik/templates/rbac/serviceaccount.yaml kind: ServiceAccount apiVersion: v1 metadata: name: traefik-release namespace: traefik labels: app.kubernetes.io/name: traefik app.kubernetes.io/instance: traefik-release-default helm.sh/chart: traefik-35.4.0 app.kubernetes.io/managed-by: Helm annotations: automountServiceAccountToken: false --- # Source: traefik/templates/rbac/clusterrole.yaml kind: ClusterRole apiVersion: rbac.authorization.k8s.io/v1 metadata: name: traefik-release-default labels: app.kubernetes.io/name: traefik app.kubernetes.io/instance: traefik-release-default helm.sh/chart: traefik-35.4.0 app.kubernetes.io/managed-by: Helm rules: - apiGroups: - "" resources: - configmaps - nodes - services verbs: - get - list - watch - apiGroups: - discovery.k8s.io resources: - endpointslices verbs: - list - watch - apiGroups: - "" resources: - secrets verbs: - get - list - watch - apiGroups: - extensions - networking.k8s.io resources: - ingressclasses - ingresses verbs: - get - list - watch - apiGroups: - extensions - networking.k8s.io resources: - ingresses/status verbs: - update - apiGroups: - traefik.io resources: - ingressroutes - ingressroutetcps - ingressrouteudps - middlewares - middlewaretcps - serverstransports - serverstransporttcps - tlsoptions - tlsstores - traefikservices verbs: - get - list - watch --- # Source: traefik/templates/rbac/clusterrolebinding.yaml kind: ClusterRoleBinding apiVersion: rbac.authorization.k8s.io/v1 metadata: name: traefik-release-default labels: app.kubernetes.io/name: traefik app.kubernetes.io/instance: traefik-release-default helm.sh/chart: traefik-35.4.0 app.kubernetes.io/managed-by: Helm roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: traefik-release-default subjects: - kind: ServiceAccount name: traefik-release namespace: traefik --- # 添加PVC定义 apiVersion: v1 kind: PersistentVolumeClaim metadata: name: traefik-data-pvc namespace: traefik spec: accessModes: - ReadWriteMany # CephFS支持多节点读写 storageClassName: ceph-cephfs resources: requests: storage: 1Gi # 根据实际需求调整大小 --- # Source: traefik/templates/deployment.yaml apiVersion: apps/v1 kind: Deployment metadata: name: traefik-release namespace: traefik labels: app.kubernetes.io/name: traefik app.kubernetes.io/instance: traefik-release-default helm.sh/chart: traefik-35.4.0 app.kubernetes.io/managed-by: Helm annotations: spec: replicas: 1 selector: matchLabels: app.kubernetes.io/name: traefik app.kubernetes.io/instance: traefik-release-default strategy: type: RollingUpdate rollingUpdate: maxUnavailable: 0 maxSurge: 1 minReadySeconds: 0 template: metadata: annotations: prometheus.io/scrape: "true" prometheus.io/path: "/metrics" prometheus.io/port: "9100" labels: app.kubernetes.io/name: traefik app.kubernetes.io/instance: traefik-release-default helm.sh/chart: traefik-35.4.0 app.kubernetes.io/managed-by: Helm spec: securityContext: runAsUser: 0 runAsGroup: 0 fsGroup: 0 capabilities: add: ["NET_BIND_SERVICE"] serviceAccountName: traefik-release automountServiceAccountToken: true terminationGracePeriodSeconds: 60 hostNetwork: false containers: - image: registry.cn-guangzhou.aliyuncs.com/xingcangku/traefik:v3.0.0 imagePullPolicy: IfNotPresent name: traefik-release resources: readinessProbe: httpGet: path: /ping port: 9000 scheme: HTTP failureThreshold: 1 initialDelaySeconds: 2 periodSeconds: 10 successThreshold: 1 timeoutSeconds: 2 livenessProbe: httpGet: path: /ping port: 9000 scheme: HTTP failureThreshold: 3 initialDelaySeconds: 2 periodSeconds: 10 successThreshold: 1 timeoutSeconds: 2 lifecycle: ports: - name: metrics containerPort: 9100 protocol: TCP - name: traefik containerPort: 9000 protocol: TCP - name: web containerPort: 8000 protocol: TCP - name: websecure containerPort: 8443 protocol: TCP securityContext: allowPrivilegeEscalation: false capabilities: drop: - ALL - NET_BIND_SERVICE readOnlyRootFilesystem: false volumeMounts: - name: data mountPath: /data readOnly: false # 允许写入 args: - "--global.checknewversion" - "--global.sendanonymoususage" - "--entryPoints.metrics.address=:9100/tcp" - "--entryPoints.traefik.address=:9000/tcp" - "--entryPoints.web.address=:8000/tcp" - "--entryPoints.websecure.address=:8443/tcp" - "--api.dashboard=true" - "--ping=true" - "--metrics.prometheus=true" - "--metrics.prometheus.entrypoint=metrics" - "--providers.kubernetescrd" - "--providers.kubernetescrd.allowEmptyServices=true" - "--providers.kubernetesingress" - "--providers.kubernetesingress.allowEmptyServices=true" - "--providers.kubernetesingress.ingressendpoint.publishedservice=traefik/traefik-release" - "--entryPoints.websecure.http.tls=true" - "--log.level=INFO" env: - name: POD_NAME valueFrom: fieldRef: fieldPath: metadata.name - name: POD_NAMESPACE valueFrom: fieldRef: fieldPath: metadata.namespace volumes: # 替换emptyDir为PVC - name: data persistentVolumeClaim: claimName: traefik-data-pvc securityContext: runAsGroup: 65532 runAsNonRoot: true runAsUser: 65532 --- # Source: traefik/templates/service.yaml apiVersion: v1 kind: Service metadata: name: traefik namespace: traefik labels: app.kubernetes.io/name: traefik app.kubernetes.io/instance: traefik-release-default helm.sh/chart: traefik-35.4.0 app.kubernetes.io/managed-by: Helm annotations: spec: type: LoadBalancer selector: app.kubernetes.io/name: traefik app.kubernetes.io/instance: traefik-release-default ports: - port: 8000 name: web targetPort: web protocol: TCP - port: 8443 name: websecure targetPort: websecure protocol: TCP --- # Source: traefik/templates/ingressclass.yaml apiVersion: networking.k8s.io/v1 kind: IngressClass metadata: annotations: ingressclass.kubernetes.io/is-default-class: "true" labels: app.kubernetes.io/name: traefik app.kubernetes.io/instance: traefik-release-default helm.sh/chart: traefik-35.4.0 app.kubernetes.io/managed-by: Helm name: traefik-release spec: controller: traefik.io/ingress-controller root@k8s01:~/helm/traefik/traefik-helm-chart-35.4.0/traefik# cat dashboard.yaml apiVersion: traefik.io/v1alpha1 kind: IngressRoute metadata: name: dashboard namespace: traefik spec: entryPoints: - web routes: - match: Host(`traefik.local.com`) kind: Rule services: - name: api@internal kind: TraefikService 二、测试traefikkubectl create ns test-ns kubectl -n test-ns create deployment test-app --image=registry.cn-guangzhou.aliyuncs.com/xingcangku/nginx-alpine:1.0 kubectl -n test-ns expose deployment test-app --port=80cat <<EOF | kubectl apply -f - > apiVersion: networking.k8s.io/v1 > kind: Ingress > metadata: > name: test-ingress > namespace: test-ns > spec: > ingressClassName: traefik > rules: > - http: > paths: > - path: /test > pathType: Prefix > backend: > service: > name: test-app > port: > number: 80 > EOFWEB_PORT=$(kubectl get svc -n traefik traefik -o jsonpath='{.spec.ports[?(@.name=="web")].nodePort}')curl -v http://$NODE_IP:$WEB_PORT/test * Trying 192.168.3.200:32305... * Connected to 192.168.3.200 (192.168.3.200) port 32305 (#0) > GET /test HTTP/1.1 > Host: 192.168.3.200:32305 > User-Agent: curl/7.81.0 > Accept: */* > * Mark bundle as not supporting multiuse < HTTP/1.1 404 Not Found < Content-Length: 153 < Content-Type: text/html < Date: Thu, 29 May 2025 18:06:51 GMT < Server: nginx/1.27.5 < <html> <head><title>404 Not Found</title></head> <body> <center><h1>404 Not Found</h1></center> <hr><center>nginx/1.27.5</center> </body> </html> * Connection #0 to host 192.168.3.200 left intact#更新路径 cat <<EOF | kubectl apply -f - > apiVersion: networking.k8s.io/v1 > kind: Ingress > metadata: > name: test-ingress > namespace: test-ns > spec: > ingressClassName: traefik > rules: > - http: > paths: > - path: / > pathType: Prefix > backend: > service: > name: test-app > port: > number: 80 > EOF # 测试访问根路径 curl -v http://$NODE_IP:$WEB_PORT/ * Trying 192.168.3.200:32305... * Connected to 192.168.3.200 (192.168.3.200) port 32305 (#0) > GET / HTTP/1.1 > Host: 192.168.3.200:32305 > User-Agent: curl/7.81.0 > Accept: */* > * Mark bundle as not supporting multiuse < HTTP/1.1 200 OK < Accept-Ranges: bytes < Content-Length: 615 < Content-Type: text/html < Date: Thu, 29 May 2025 18:08:48 GMT < Etag: "67ffa8c6-267" < Last-Modified: Wed, 16 Apr 2025 12:55:34 GMT < Server: nginx/1.27.5 < <!DOCTYPE html> <html> <head> <title>Welcome to nginx!</title> <style> html { color-scheme: light dark; } body { width: 35em; margin: 0 auto; font-family: Tahoma, Verdana, Arial, sans-serif; } </style> </head> <body> <h1>Welcome to nginx!</h1> <p>If you see this page, the nginx web server is successfully installed and working. Further configuration is required.</p> <p>For online documentation and support please refer to <a href="http://nginx.org/">nginx.org</a>.<br/> Commercial support is available at <a href="http://nginx.com/">nginx.com</a>.</p> <p><em>Thank you for using nginx.</em></p> </body> </html> * Connection #0 to host 192.168.3.200 left intact#可以在集群内部访问 curl http://traefik-service.default.svc.cluster.localroot@k8s01:~/helm/traefik/test# kubectl get ingress -n test-ns NAME CLASS HOSTS ADDRESS PORTS AGE test-ingress traefik * 80 48m root@k8s01:~/helm/traefik/test# kubectl describe ingress test-ingress -n test-ns Name: test-ingress Labels: <none> Namespace: test-ns Address: Ingress Class: traefik Default backend: <default> Rules: Host Path Backends ---- ---- -------- * / test-app:80 (10.244.1.13:80) Annotations: <none> Events: <none> #命令查询 root@k8s01:~/helm/traefik/traefik-helm-chart-35.4.0/traefik# kubectl -n traefik describe svc traefik Name: traefik Namespace: traefik Labels: app.kubernetes.io/instance=traefik-release-default app.kubernetes.io/managed-by=Helm app.kubernetes.io/name=traefik helm.sh/chart=traefik-35.4.0 Annotations: <none> Selector: app.kubernetes.io/instance=traefik-release-default,app.kubernetes.io/name=traefik Type: LoadBalancer IP Family Policy: SingleStack IP Families: IPv4 IP: 10.103.186.47 IPs: 10.103.186.47 Port: web 8000/TCP TargetPort: web/TCP NodePort: web 30615/TCP Endpoints: 10.244.2.30:8000 Port: websecure 8443/TCP TargetPort: websecure/TCP NodePort: websecure 32113/TCP Endpoints: 10.244.2.30:8443 Session Affinity: None External Traffic Policy: Cluster Events: <none> root@k8s01:~/helm/traefik/traefik-helm-chart-35.4.0/traefik# kubectl -n traefik get endpoints NAME ENDPOINTS AGE traefik 10.244.2.30:8000,10.244.2.30:8443 26s traefik-crds 10.244.0.169:8000,10.244.0.169:8443 2d4h root@k8s01:~/helm/traefik/traefik-helm-chart-35.4.0/traefik# cat service.yaml # Source: traefik/templates/service.yaml apiVersion: v1 kind: Service metadata: name: traefik namespace: traefik labels: app.kubernetes.io/name: traefik app.kubernetes.io/instance: traefik-release-default helm.sh/chart: traefik-35.4.0 app.kubernetes.io/managed-by: Helm annotations: spec: type: LoadBalancer selector: app.kubernetes.io/name: traefik app.kubernetes.io/instance: traefik-release-default ports: - port: 8000 name: web targetPort: web protocol: TCP - port: 8443 name: websecure targetPort: websecure protocol: TCP root@k8s01:~/helm/traefik/traefik-helm-chart-35.4.0/traefik# kubectl get -n traefik svc NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE traefik LoadBalancer 10.103.186.47 <pending> 8000:30615/TCP,8443:32113/TCP 7m11s traefik-crds LoadBalancer 10.101.202.240 <pending> 80:31080/TCP,443:32480/TCP,6379:30634/TCP 2d5h root@k8s01:~/helm/traefik/traefik-helm-chart-35.4.0/traefik# kubectl get pods -n traefik -o wide NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES traefik-crds-766d79b985-c2sbr 1/1 Running 3 (6h13m ago) 2d4h 10.244.0.169 k8s01 <none> <none> traefik-release-589c7ff647-pdjh4 1/1 Running 0 25m 10.244.2.30 k8s03 <none> <none> root@k8s01:~/helm/traefik/traefik-helm-chart-35.4.0/traefik#